Even with Slack, Groups, and each new communication instrument on the market, e mail stays the highest assault vector for companies. Why? As a result of it’s acquainted, trusted, and simple to use.
One convincing message is all it takes and threats slip proper previous filters, AVs, and EDRs with out making a sound.
Under are 5 actual examples of assaults that went undetected by conventional instruments however had been totally uncovered in ANY.RUN’s interactive sandbox.
Test them out to see how they work and how one can cease threats like these with far much less effort.
1. Malware Attachments: The Menace That Seems Routine
For a lot of SOCs, malware attachments stay one of the irritating blind spots. On the floor, these information seem like on a regular basis enterprise paperwork, PDFs, invoices, transport notes.
They usually go by as a result of static evaluation doesn’t catch what the file really does.
Why SOCs miss it:
Static scanners solely examine signatures, not conduct
Trusted providers (like SharePoint) internet hosting the payload enhance false negatives
No actual person interplay means the total payload chain doesn’t execute in take a look at environments
However with an interactive sandbox like ANY.RUN, SOC groups get precisely what’s been lacking: full visibility into the total execution chain, from the second a file is opened to the ultimate exfiltration try.
In contrast to static scanners, the sandbox actively interacts with the file, clicks buttons, opens hyperlinks, and triggers hidden payloads, exposing behaviors that might in any other case keep dormant.
Even information that seem clear on the floor reveal their true nature when watched in actual time.
Actual Case: A Harmful PDF That Seems Legit
Suspicious PDF attachment analyzed inside ANY.RUN sandbox
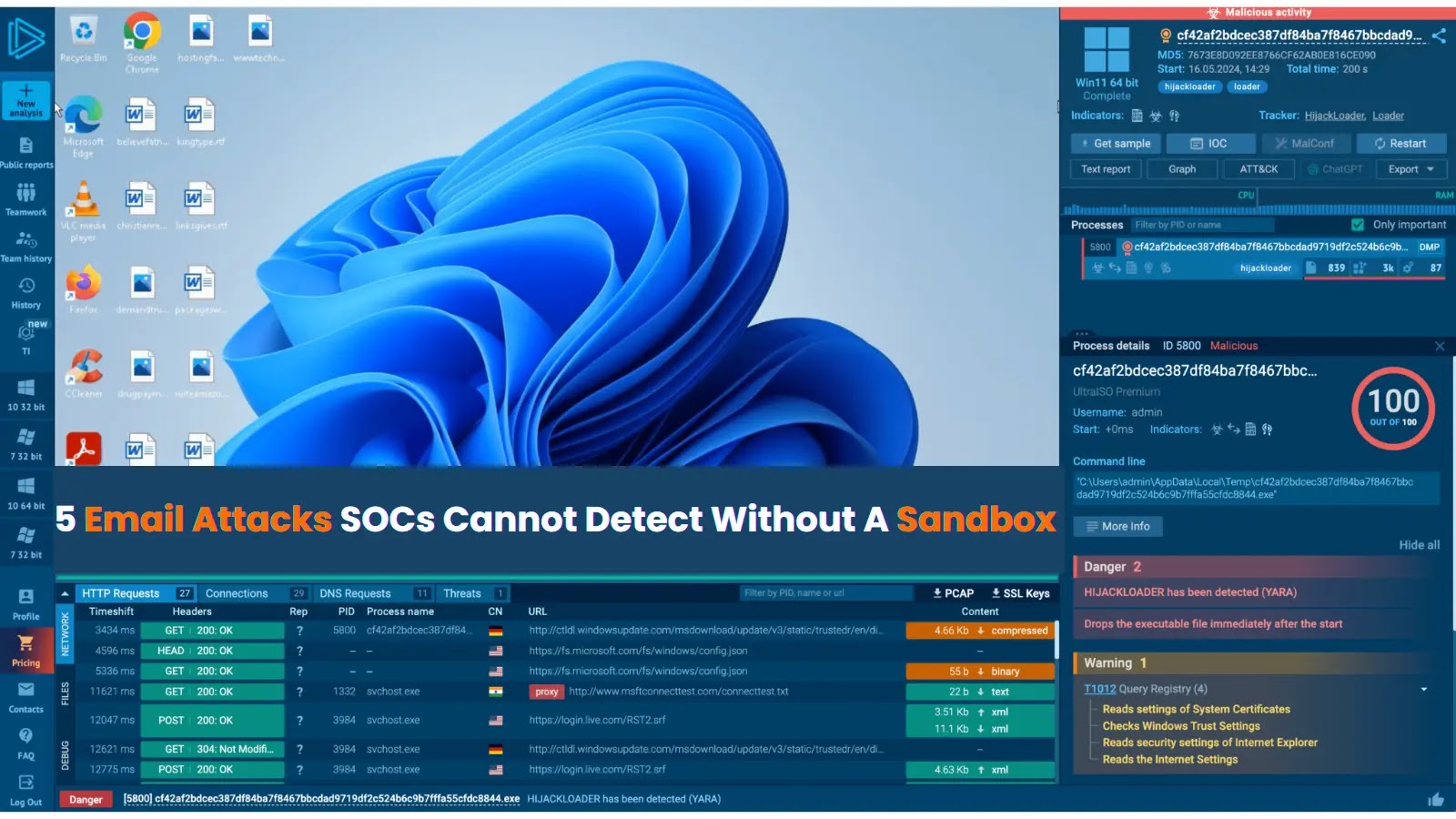
At first look, Rauscher-Fahrzeugeinrichtungen.pdf seemed like a routine enterprise file. However when detonated in ANY.RUN’s sandbox, a a lot totally different image emerged.
The second the file was opened, it reached out to a phishing web page hosted on SharePoint; a trusted Microsoft area usually used to bypass filters.
Inside, obfuscated JavaScript silently triggered additional system exercise, together with the launch of Adobe Acrobat and Microsoft Edge.
Phishing web page with malicious attachment hosted on SharePoint
Edge loaded a faux Microsoft login web page, constructed to steal credentials. In the meantime, background processes linked to exterior servers to exfiltrate knowledge.
Faux Microsoft web page used to steal credentials from potential victims
ANY.RUN flagged this as a social engineering assault, mapping it to MITRE T1566 (Phishing) and exposing the total execution chain, from open to credential theft try.
And not using a sandbox, this file would’ve seemed clear. With ANY.RUN, SOC groups get the visibility they should detect, perceive, and cease threats earlier than they do injury.
Equip your SOC with ANY.RUN’s sandbox to detect evasive e mail threats in actual time and lower response time with much less handbook effort -> Enroll now
2. Credential Theft: When One Click on Opens The Door
Credential theft stays one of the harmful e mail threats for SOCs, particularly when it’s paired with instruments designed to bypass MFA.
These phishing campaigns usually depend on well-crafted hyperlinks that look reputable and set off conduct that’s practically invisible to conventional defenses.
Most SOC instruments scan for recognized indicators, however they hardly ever catch what occurs after a hyperlink is clicked. That’s the place interactive sandboxes make all of the distinction.
Actual Case: Phishing with Tycoon 2FA
Phishing e mail with Tycoon 2FA analyzed inside ANY.RUN sandbox
On this assault, a phishing e mail contained a hyperlink tied to Tycoon 2FA; a instrument used to bypass MFA on Microsoft and Google accounts.
As soon as clicked, ANY.RUN’s sandbox noticed a number of Edge processes launching; an early pink flag. These processes started altering browser cache and person knowledge and even began modifying registry keys.
Registry keys beneath HKEY_CURRENT_USERSoftwareMicrosoft are being edited silently by the browser
The sufferer was then redirected to an ideal duplicate of a Microsoft login web page, hosted on a malicious area. Any credentials entered right here would go straight to the attacker.
The sandbox additionally flagged a possible Tor connection, probably used to exfiltrate the stolen knowledge.
Faux Microsoft login web page revealed inside interactive sandbox
And not using a sandbox, this sort of phishing exercise seems to be like a standard looking session.
However with ANY.RUN, your SOC can see the total assault circulation, determine suspicious patterns, detect MFA bypass makes an attempt, and block them earlier than credentials are misplaced.
3. Zero-Day Exploits: The Assaults That Don’t Wait
Zero-days are a nightmare for SOCs as a result of they exploit flaws that don’t have a patch or signature but. Conventional instruments can’t catch what they don’t acknowledge and that’s precisely what makes these threats so harmful.
One latest case concerned CVE-2024-43451, a Home windows vulnerability that leaks NTLMv2 hashes simply by interacting with a malicious shortcut file.
No clicks wanted, merely previewing the e-mail was sufficient to launch the assault.
Actual Case: Phishing with Zero-Day Exploit
.eml e mail with a zipped attachment that silently triggers system exercise when previewed
Contained in the ANY.RUN sandbox, a malicious .eml file was opened. With none person motion, it triggered Edge, then WinRAR, and eventually launched hidden instructions that abused the vulnerability.
Using CVE-2024-43451 detected by ANY.RUN sandbox
Lastly, a silent SMB connection that exfiltrated the person’s NTLMv2 hash gave attackers a path to pass-the-hash lateral motion.
ANY.RUN reveals a profitable connection to an exterior SMB server, exposing a possible company privateness violation
For SOCs, that is precisely why behavioral visibility issues. With ANY.RUN, it’s detected and mapped in beneath a minute, earlier than attackers get in.
4. Quishing: The QR Code Trick Most Instruments Miss
Quishing, phishing by way of QR codes, is a rising problem for SOCs. These assaults embed malicious QR codes in emails or attachments, luring customers to scan them with their telephones.
Since cell units usually sit outdoors company defenses, the assault bypasses filters, EDRs, and e mail gateways utterly.
Actual Case: Voicemail Phish by way of QR
ANY.RUN sandbox revealing the malicious URL in seconds with out handbook interplay
On this ANY.RUN session, a phishing e mail claimed the person had a voicemail. The catch? They needed to scan a QR code to listen to it.
Contained in the sandbox, ANY.RUN’s automated interactivity kicked in, scanning the code, decoding the URL, and exposing the phishing website in seconds, with none handbook steps wanted from the analyst.
Malicious URL uncovered within the Static discovering part inside ANY.RUN sandbox
For SOC groups, this implies quicker detection, much less analyst time, and the flexibility to catch threats that bypass conventional e mail protections fully.
5. CVE-2017-11882: Outdated Exploit, Ongoing Menace
Regardless of being years previous, CVE-2017-11882 remains to be actively exploited, primarily by malicious .RTF or .DOC information delivered by way of phishing emails.
The vulnerability lives within the outdated Microsoft Equation Editor and allows distant code execution as quickly because the doc is opened.
For SOCs, some of these legacy exploits usually go undetected as a result of the payload seems to be like a normal Workplace file till it’s actively run.
Actual Case: Exploit Triggered by way of E mail Attachment
Malicious e mail with CVE-2017-11882 vulnerability analyzed inside ANY.RUN sandbox
On this ANY.RUN session, the assault arrived by way of a .eml file containing an Workplace doc.
When opened, it triggered the EQNEDT32.EXE course of and commenced executing a sequence of malicious actions; studying system configs, accessing certificates, dropping information, and reaching out to exterior servers.
EQNEDT32.EXE altering system information inside ANY.RUN’s interactive sandbox
ANY.RUN flagged the exploit immediately and mapped it to MITRE ATT&CK, giving the SOC group quick readability and saving time on handbook investigation.
Exploitation of CVE-2017-11882 revealed within the MITRE ATT&CK part of ANY.RUN sandbox
By detecting recognized exploits like this in actual time, sandboxes assist groups scale back MTTD and cease even outdated assault strategies earlier than they unfold.
Make Your SOC Prepared For Actual-World E mail Threats
The 5 e mail assaults are actual circumstances captured within the wild, usually bypassing conventional defenses and touchdown instantly in worker inboxes.
For many SOCs, static scans, e mail filters, and EDRs aren’t sufficient to reveal what’s actually taking place after the press. That’s why you want an answer like ANY.RUN’s interactive sandbox.
With ANY.RUN sandbox, your SOC positive factors:
Deep behavioral visibility into attachments, hyperlinks, and payloads
Detection of evasive threats that bypass conventional instruments
Automation that reduces analyst workload and response time
Enriched IOCs for quicker investigation and SIEM integration
Detailed, shareable studies to assist response and compliance
Begin your 14-day trial of ANY.RUN and produce real-world detection energy into your SOC.