There’s a second, proper after a brand new alert hits, when the room holds its breath. Everybody waits for context; is it actual, is it noise, is it already too late?
In these seconds, the distinction between a median SOC and a fantastic one is clear. Some scramble for solutions; others transfer in sync, sharing context quick and turning confusion into readability earlier than the panic begins.
That stage of management doesn’t come from luck however a number of easy guidelines that maintain elite SOCs quick, centered, and forward of the sport.
Rule #1: Velocity Turns Panic into Precision
Velocity modifications the whole lot. When threats hit, quick visibility turns chaos into readability. The sooner a group understands what’s occurring, the sooner it may well cease the unfold, reduce harm, and regain management.
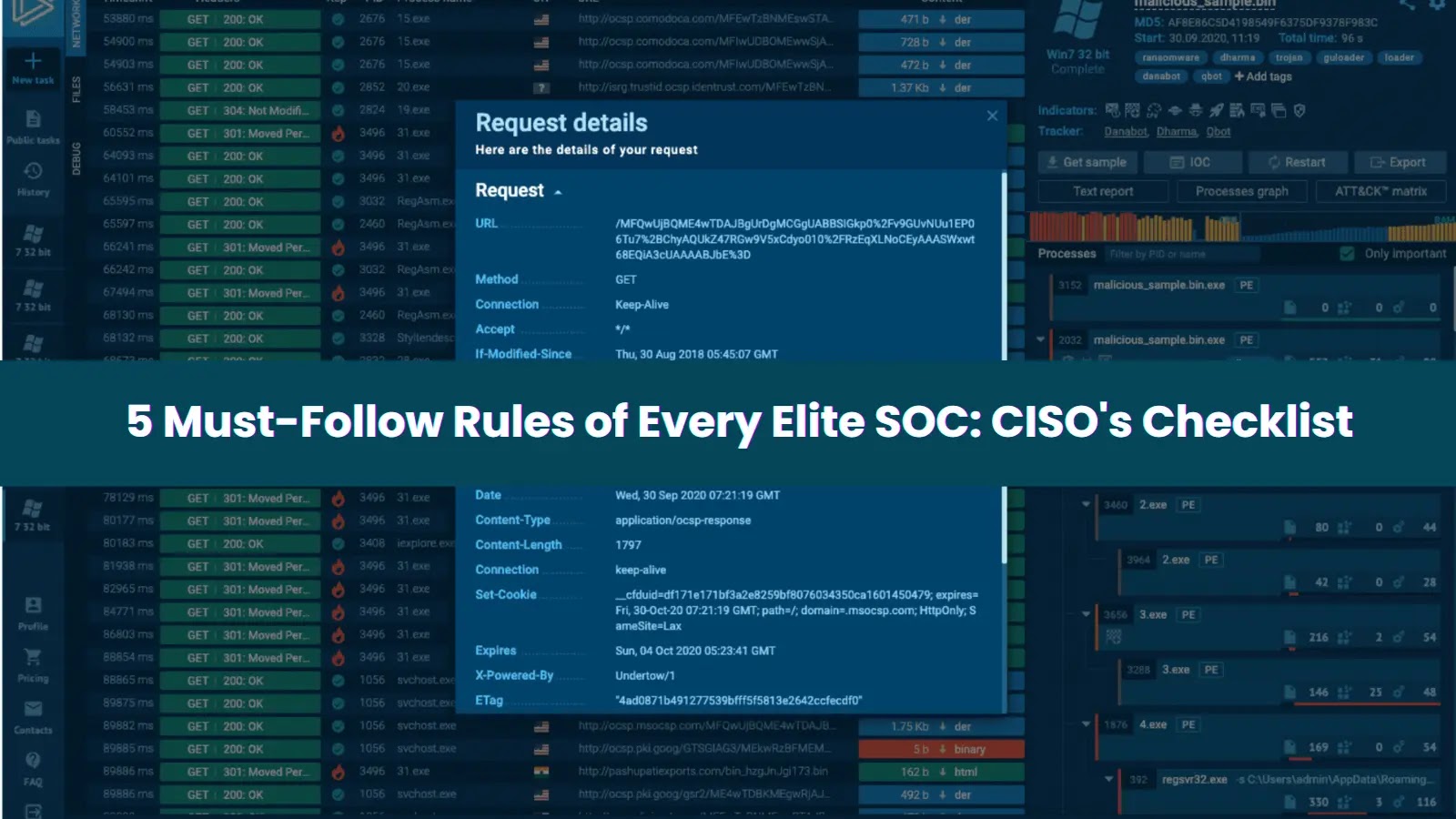
That’s why most fashionable SOCs depend on cloud-based sandboxes like ANY.RUN to make pace their first line of protection. There’s no must deploy or keep digital machines; evaluation launches in seconds, giving groups a direct look into the total assault chain.
LockBit assault totally analyzed inside ANY.RUN’s cloud sandbox
The decision of most analyses is prepared in beneath 60 seconds, offering actionable perception lengthy earlier than conventional instruments even end scanning.
As an example, in a single current evaluation, a LockBit assault was totally uncovered in simply 33 seconds; full with associated IOCs, mapped TTPs, habits particulars, and course of timber.
View LockBit assault uncovered totally in 30 seconds
30 seconds required from ANY.RUN sandbox to point out the malicious verdict
When detection is that this quick, panic by no means has an opportunity to set in. Groups can shift immediately from response to technique, understanding the menace, planning the response, and staying firmly in management.
Flip pace into technique; join with ANY.RUN and see how instantaneous detection powers stronger, sooner selections throughout your SOC: Speak to ANY.RUN Specialists
Rule #2: Risk Detection is a Workforce Sport
Even the very best analysts can’t detect the whole lot alone. When communication breaks down and groups work in silos, essential context slips away; alerts are missed, work will get repeated, and investigations sluggish to a crawl.
That’s why collaboration has develop into a core a part of fashionable SOC efficiency. Contained in the ANY.RUN sandbox, the Teamwork function lets analysts be a part of the identical stay workspace, share ends in actual time, and coordinate throughout roles with out switching instruments. Workforce leads can assign duties, monitor progress, and monitor productiveness; all from a single interface that retains the group aligned, irrespective of the time zone.
Workforce administration displayed inside ANY.RUN sandbox
The result’s a SOC that thinks and strikes as one. Each analyst is aware of their focus, each lead sees the total image, and selections occur with out hesitation. That’s what actual teamwork seems like, and that’s how robust menace detection truly occurs.
Rule #3: Automate What Slows You Down
Each SOC is aware of the sensation; too many alerts, too many clicks, not sufficient time. Analysts lose hours on repetitive actions: opening recordsdata, working scripts, clicking by means of pop-ups, or fixing CAPTCHAs simply to set off hidden payloads.
With Automated Interactivity contained in the ANY.RUN sandbox, all these steps occur mechanically. The system opens malicious hyperlinks hidden behind QR codes, interacts with pretend installers, solves CAPTCHAs, and performs different routine actions; no human enter wanted. The sandbox handles these interactions by itself, exposing each stage of the assault chain in a fraction of the time.
ANY.RUN sandbox fixing CAPTCHA mechanically, revealing the total assault chain in 20 seconds
The profit? Analysts skip the busywork and bounce straight to perception. Quicker detection, cleaner information, and extra time for the investigations that require human judgment. Automation clears the trail for cybersecurity professionals to do their finest work, saving huge time.
Rule #4: Go Arms-On to Expose Hidden Threats
Even the very best detection instruments miss issues. False negatives occur on a regular basis; a file marked “secure” can nonetheless disguise malicious habits deep in its code or set off solely beneath particular circumstances.
That’s why elite SOCs by no means depend on automation alone. When one thing seems suspicious, analysts dig deeper in an interactive surroundings, the place they’ll open recordsdata, click on buttons, comply with hyperlinks, and provoke actual habits in actual time.
Interacting with the pretend Microsoft web page inside ANY.RUN sandbox
Contained in the ANY.RUN sandbox, this hands-on management turns static evaluation into lively discovery, revealing payloads, persistence mechanisms, and hidden community exercise that automated scanners overlook.
Automation provides you pace; hands-on provides you certainty. It’s the stability between the 2 that stops actual harm.
Rule #5: Practice Analysts By Actual Expertise
You may’t prepare nice analysts on idea alone. Actual talent comes from seeing how threats behave, testing hypotheses, and studying by means of direct expertise, not static examples or outdated labs.
That’s why fashionable SOCs use sandboxes to show real-world incidents into studying alternatives. Contained in the ANY.RUN sandbox, junior analysts can safely discover stay samples, experiment with habits, and construct instinct that no textbook can train.
In the meantime, by means of Teamwork Administration options, managers can observe progress in actual time, monitoring how analysts examine, collaborate, and develop with every session.
Monitoring group members’ productiveness inside ANY.RUN’s sandbox
The result’s sooner onboarding, stronger retention, and a group that learns from precise threats as an alternative of simulated ones. It saves each time and coaching prices whereas constructing actual, lasting experience throughout the SOC.
Construct the SOC That Units the Customary
When these 5 guidelines develop into a part of your day by day SOC workflow, outcomes comply with quick.Groups that mix automation, collaboration, and hands-on evaluation work smarter, with measurable enhancements throughout each tier.
As much as 58% extra threats recognized: Detect assaults that bypass normal defenses with interactive evaluation and information from 15K+ world companies.
88% of assaults seen inside 60 seconds: See stay habits immediately, automate detection, and enrich alerts with key indicators.
94% of customers report sooner triage: Accumulate IOCs and TTPs, simplify assessments, and act sooner with actual menace information.
95% of SOC groups pace up investigations: Collaborate in actual time, deal with extra alerts, and monitor efficiency in a single workspace.
As much as 20% decrease Tier 1 workload and 30% fewer escalations: Cut back guide effort, take away {hardware} prices, and remove alert fatigue.
Contact ANY.RUN specialists to carry these outcomes to your group and construct a SOC that actually units the usual.