A large resurgence of the Sha1-Hulud provide chain malware has struck the open-source ecosystem, compromising over 800 npm packages and tens of 1000’s of GitHub repositories in a marketing campaign the attackers have dubbed “The Second Coming.”
This subtle wave targets high-profile dependencies from main organizations, together with AsyncAPI, Postman, PostHog, Zapier, and ENS, affecting an estimated 132 million month-to-month downloads.
The assault leverages the Bun runtime setting to bypass conventional detection strategies and introduces a catastrophic fallback mechanism able to wiping sufferer knowledge.
Probably the most alarming evolution on this variant is its aggressive volatility. Whereas the first purpose stays credential theft, the malware features a damaging fail-safe that triggers if it can not set up persistence or exfiltrate knowledge.
If the malware fails to authenticate to GitHub, create a repository, fetch a GitHub token, or find an NPM token, it executes a wiper routine.
Sha1-Hulud Provide Chain Assault
This logic makes an attempt to destroy the sufferer’s total house listing by deleting each writable file owned by the present person. This shift signifies that if Sha1-Hulud can not steal credentials or safe an exfiltration channel, it defaults to catastrophic knowledge destruction to eradicate proof or trigger disruption.
The assault chain first noticed by Aikido Safety begins with a file named setup_bun.js, which installs the Bun runtime to execute the core malicious payload contained in bun_environment.js. This technique permits the malware to function exterior the usual Node.js execution path, usually evading static evaluation instruments.
As soon as lively, the worm makes use of TruffleHog to scan the contaminated setting for API keys and tokens. Not like earlier variations that used hardcoded repository names, this iteration creates randomly named GitHub repositories to retailer stolen secrets and techniques.
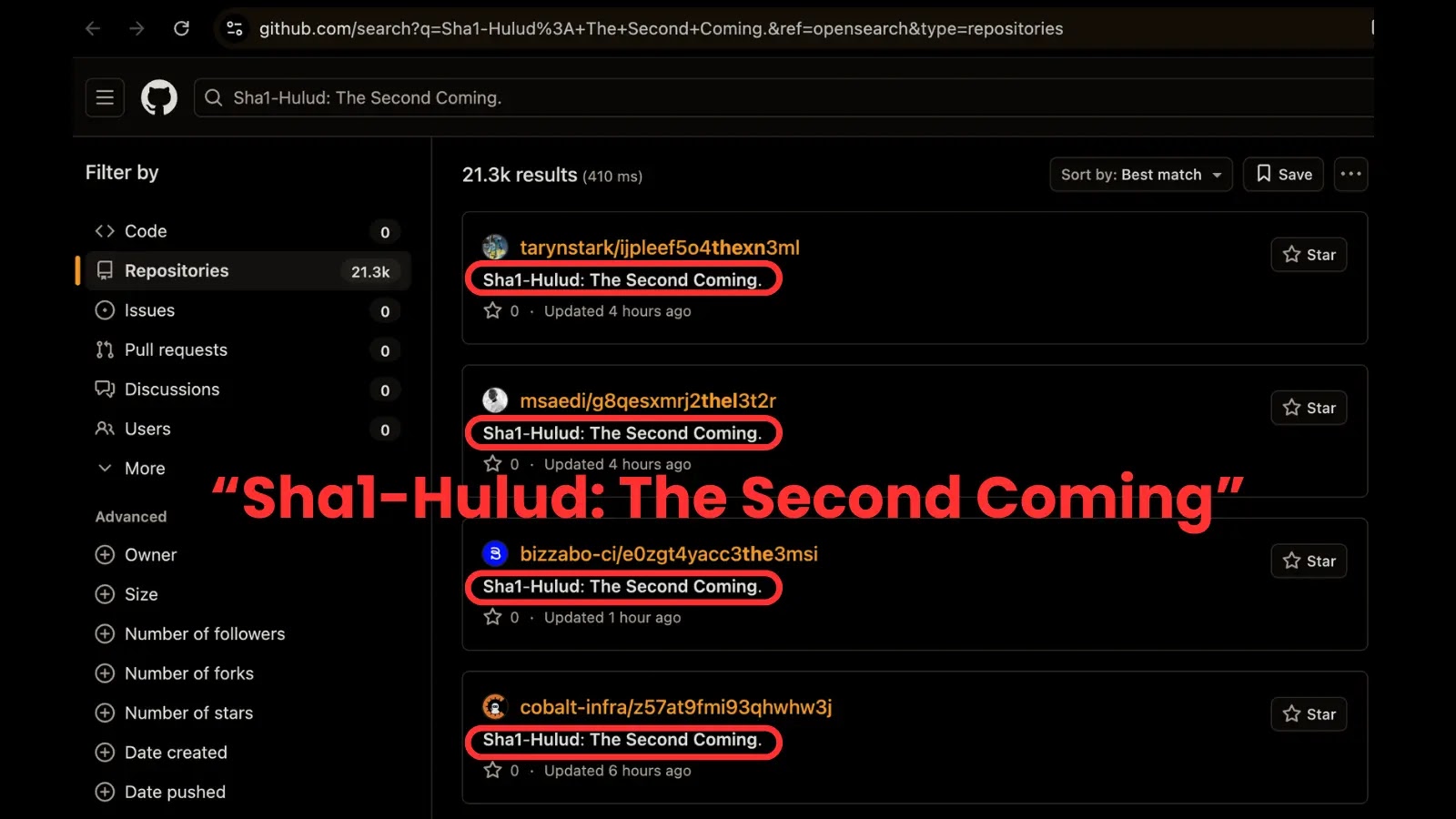
These repositories are recognized by the outline “Sha1-Hulud: The Second Coming,” with safety researchers at the moment figuring out roughly 26,300 uncovered repositories.
Idan Dartikman, co-founder and CTO of Koi Safety, emphasised the escalation in techniques. “This wave is bigger, spreads extra shortly, and is extra violent than the final,” Dartikman said. “There’s additionally an enormous safety change coming to NPM, and it is vitally attainable that the risk actor labored quick to contaminate as many victims as attainable earlier than that.”
The timing of this marketing campaign seems calculated to precede npm’s scheduled revocation of traditional tokens on December 9, 2025. The compromise has affected important infrastructure software program, together with vital parts of the AsyncAPI and Postman ecosystems.
Safety groups are suggested to instantly audit dependencies for the precise file indicators and rotate all credentials uncovered in CI/CD environments.
Sufferer OrganizationAffected Scope/Bundle ExamplesEstimated ImpactAsyncAPI@asyncapi/cli,@asyncapi/generator,asyncapi-previewCritical improvement instruments used for event-driven architectures.PostHog@posthog/cli,@posthog/node,posthog-jsAnalytics knowledge ingestion and plugin infrastructure.Postman@postman/collection-fork,@postman/tunnel-agentAPI improvement and testing utilities.Zapier@zapier/zapier-sdk,zapier-platform-coreIntegration and automation SDKs.ENS Domains@ensdomains/ensjs,@ensdomains/thorinEthereum Identify Service frontend and contract interactions.
Comply with us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to function your tales.