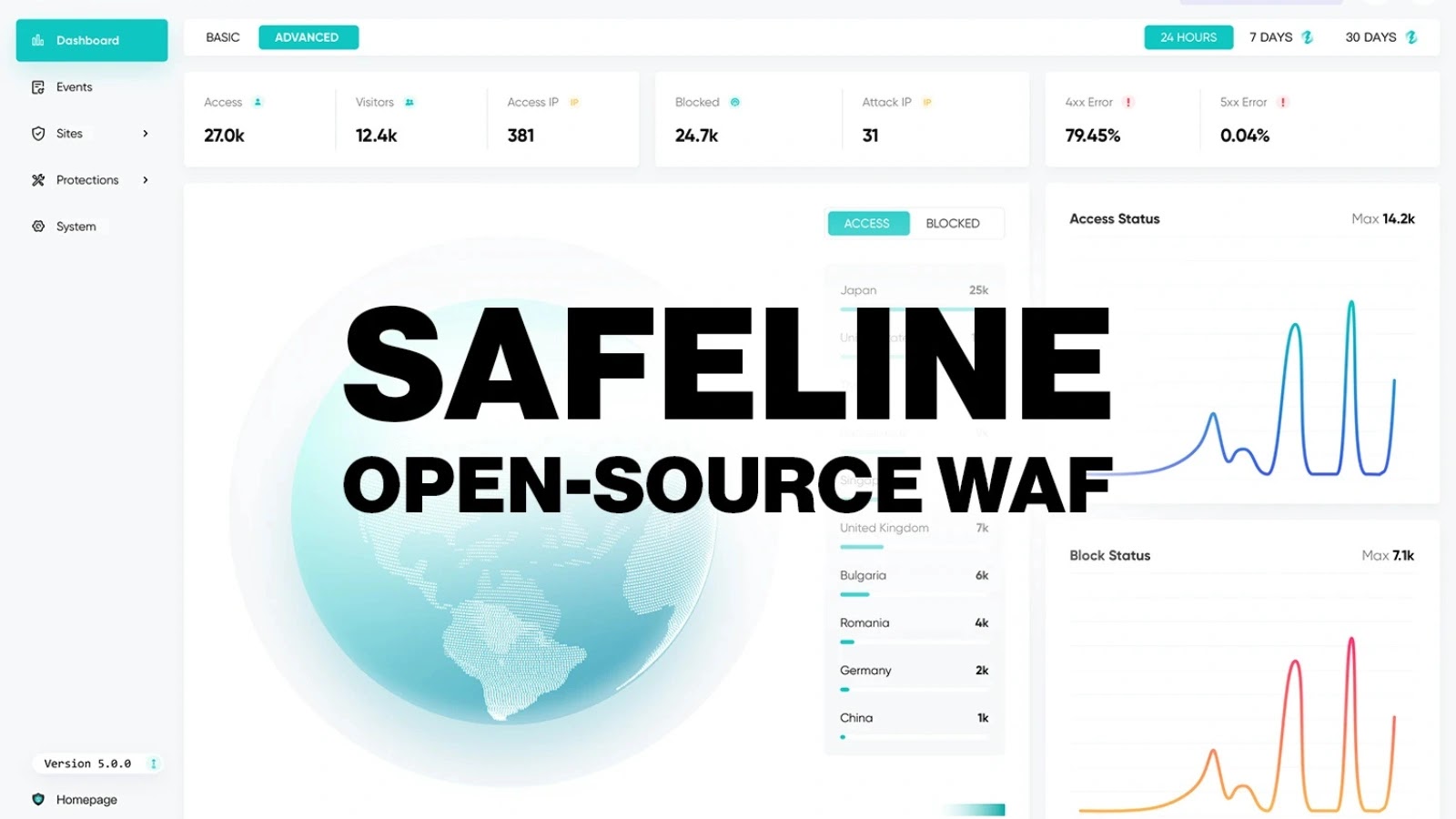
Each kind of group—whether or not it’s a multinational large with 1000’s of staff or a single tech fanatic operating a homelab—wants an internet utility firewall (WAF).
The reason being simple: internet functions face fixed threats from cyber assaults that may exploit vulnerabilities to steal knowledge, disrupt providers, or harm fame.
The prices related to server assets, alongside numerous operational and safety software program bills, could be overwhelming. That’s the place a free, highly effective resolution like SafeLine turns into a lifesaver, offering sturdy safety with out including monetary burden.
Introducing SafeLine: The Most Starred WAF Venture on GitHub in 2025
SafeLine gained exceptional recognition on GitHub in 2025, boasting 17.5k stars—making it the best starred WAF venture of the yr.
Its adoption is intensive, with greater than 400,000 situations deployed worldwide, spanning enterprises, instructional establishments, authorities businesses, and hobbyists.
Developed by Chaitin Tech, SafeLine is designed as a next-generation internet utility firewall that mixes robust security measures with ease of deployment and use. It’s community-driven, enabling steady innovation and adaptation to rising threats.
SafeLine’s Zero Belief Functionality: Free Identification-Based mostly Safety
One in all SafeLine’s most compelling options is its built-in zero belief safety mannequin. This implies organizations can defend their internet functions with each a firewall and 0 belief protection mechanisms—all for free of charge.
Zero belief is a safety framework centered on the thought of “by no means belief, at all times confirm.” SafeLine integrates identification authentication options that confirm each person or system trying to entry protected functions.
Particularly, SafeLine’s identification authentication presents Single Signal-On (SSO) and two-factor authentication (2FA). Along with the standard username and password login, it helps third-party login strategies resembling GitHub, OIDC, and LDAP.
Furthermore, the authentication web page is absolutely customizable, permitting organizations to tailor the person expertise to their particular wants.
By combining WAF protections with zero belief identification controls, SafeLine ensures that solely respectable customers can work together with essential internet providers, dramatically enhancing safety posture with out requiring pricey extra instruments.
Why Select SafeLine Amongst Many WAF Choices?
Whereas many WAF options exist, they usually include limitations. Right here’s how SafeLine overcomes widespread challenges:
Low False Positives/NegativesMany WAFs depend on signature or rule-based detection, which regularly leads to respectable visitors being mistakenly flagged as malicious (false positives), or new assaults slipping by (false negatives).
SafeLine employs Chaitin Tech’s proprietary semantic evaluation engine. It dynamically analyzes the syntax and semantics of incoming visitors, permitting it to detect zero-day exploits, novel assault vectors, and obfuscated threats that always bypass signature-focused techniques. This method considerably reduces each false alarms and detection blind spots.
Moreover, SafeLine’s semantic evaluation adapts repeatedly by studying from new knowledge and evolving threats, offering proactive and clever safety.
This know-how makes it extraordinarily troublesome for attackers to evade detection, guaranteeing that SafeLine stays efficient even in opposition to superior and rising cyber threats.
Easy Set up and Configuration
Many WAFs usually require prolonged studying curves and sophisticated configurations, demanding specialised data.
However SafeLine is designed with simplicity and user-friendliness in thoughts, making set up and configuration simple even for these with restricted technical experience.
Your entire setup course of could be accomplished with a single command, eliminating the necessity for complicated guide steps or deep system data:
bash -c “$(curl -fsSLk — –en
Full Set up Information
As soon as put in, SafeLine’s clear and intuitive web-based interface permits customers to simply handle all configurations without having to jot down sophisticated scripts or instructions.
From setting safety insurance policies to monitoring visitors and adjusting safety ranges, every thing could be executed by accessible menus and easy controls.
This ease of use considerably reduces the educational curve, enabling people and organizations of all sizes to deploy efficient internet utility safety shortly and effectively.
Proof against Evasion AttacksAttackers usually search to bypass WAF protections utilizing new protocols or evasion methods. SafeLine’s semantic engine is troublesome to bypass as a result of it understands the intent behind requests fairly than simply matching recognized patterns.
Scalable and Excessive-PerformanceUnder excessive visitors volumes, many WAFs expertise efficiency degradation.
SafeLine helps multi-node configuration synchronization, permitting organizations to simply arrange load balancing and failover mechanisms with minimal effort.
By configuring a number of SafeLine nodes, customers can distribute incoming visitors evenly throughout servers, guaranteeing optimum efficiency and stopping any single node from turning into a bottleneck.
This setup not solely improves the general responsiveness of internet functions but additionally enhances system reliability.
Within the occasion that one node experiences failure or downtime, it may well redirect visitors to wholesome nodes with out interrupting person entry.
The synchronization course of retains all nodes updated with the newest safety insurance policies and configuration modifications, sustaining constant safety throughout your complete deployment.
Implementing a resilient, high-availability atmosphere is easy with SafeLine—even for groups with out intensive infrastructure administration expertise.
Superior Bot and Automated Menace DefenseHandling malicious bots and automatic assaults has grow to be an more and more complicated and pressing problem, particularly as AI applied sciences proceed to advance and empower attackers with extra refined instruments.
SafeLine rises to fulfill this problem by integrating Chaitin Tech’s proprietary IP risk intelligence database, which maintains an up-to-date repository of recognized malicious IP addresses and rising threats worldwide.
This database allows SafeLine to proactively establish and block suspicious sources earlier than they’ll trigger hurt.
Past risk intelligence, SafeLine incorporates sturdy anti-bot problem mechanisms which might be extremely customizable, permitting organizations to tailor defenses in accordance with their distinctive visitors patterns and safety insurance policies.
Moreover, SafeLine employs superior HTML and JavaScript dynamic encryption methods, rendering it exceedingly troublesome for stylish botnets to investigate, bypass, or manipulate safety controls.
Licensing Choices Tailor-made for Each Consumer
SafeLine presents clear and versatile licensing to accommodate all customers:
Private Version (Free):No registration, no bank card binding. Installs with a single command and is able to use instantly—good for people, builders, and small initiatives.
Full Set up Information
Lite Version:Helps as much as 20 functions (The Private Version helps including as much as 10 functions.), consists of enhanced options past the free tier, and is tailor-made for small companies and homelabs. Priced affordably at $10 per 30 days.
Professional Version:Designed for organizations of all sizes, providing a full suite of superior capabilities. Obtainable through annual or month-to-month cost to unlock the complete options of SafeLine, with no hidden charges—best for enterprises demanding complete safety.
Closing Ideas
In abstract, SafeLine stands out as an accessible, sturdy, and 0 trust-enabled WAF resolution that bridges the hole between high-cost enterprise safety and user-friendly, free safety.
Its superior semantic evaluation, easy but highly effective options, and versatile licensing make it an unbeatable alternative for securing internet functions in 2026 and past.