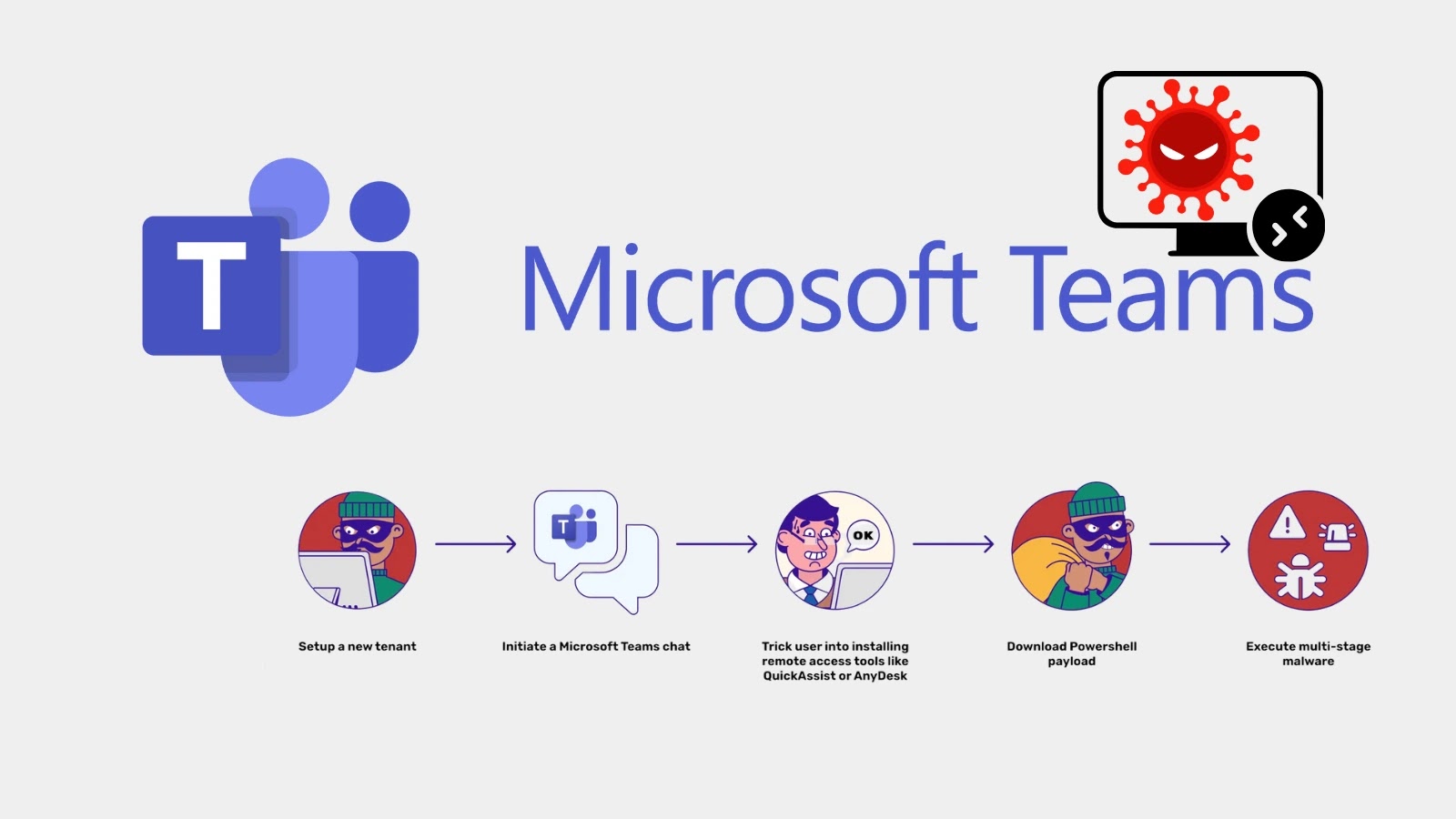
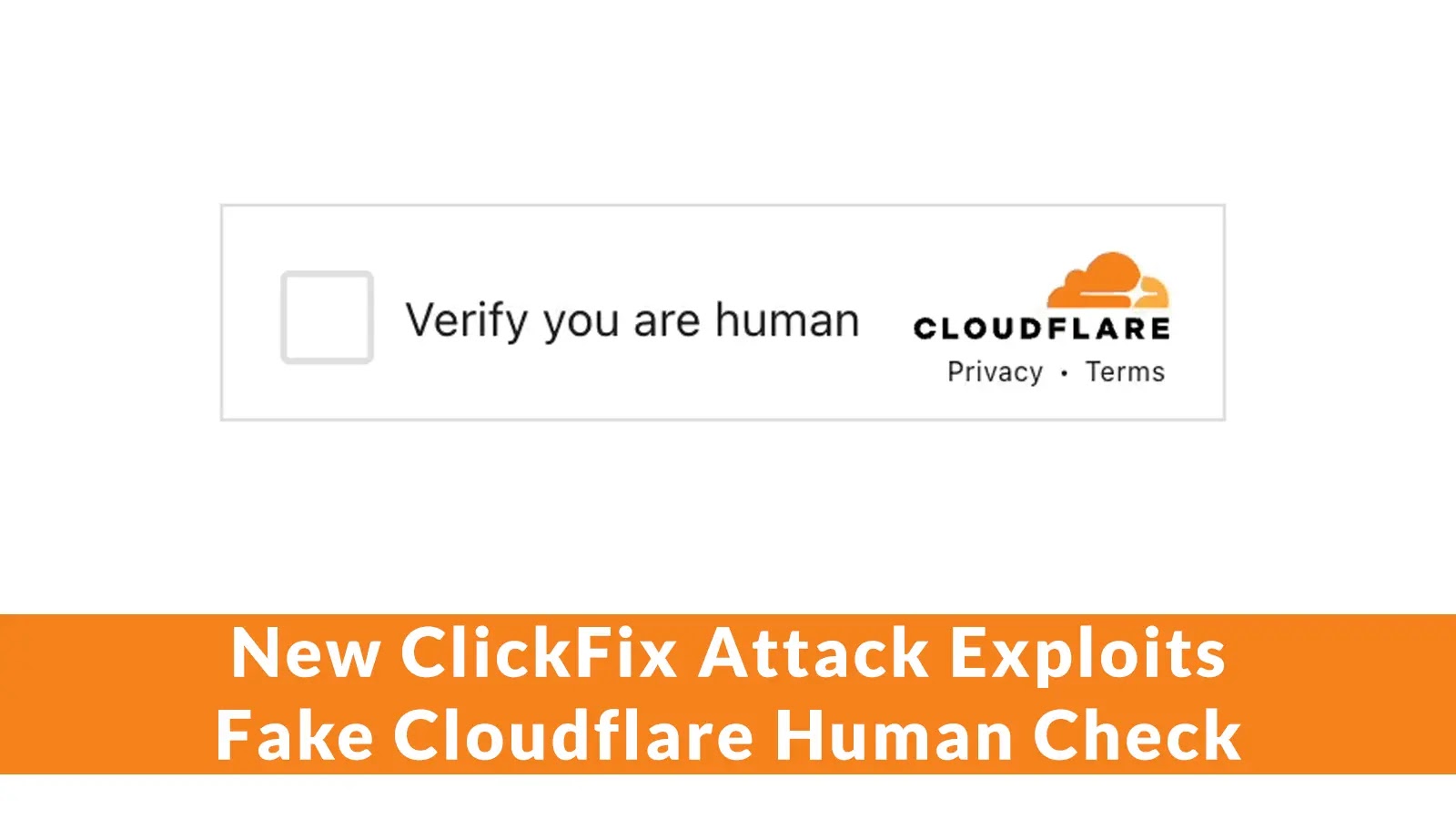
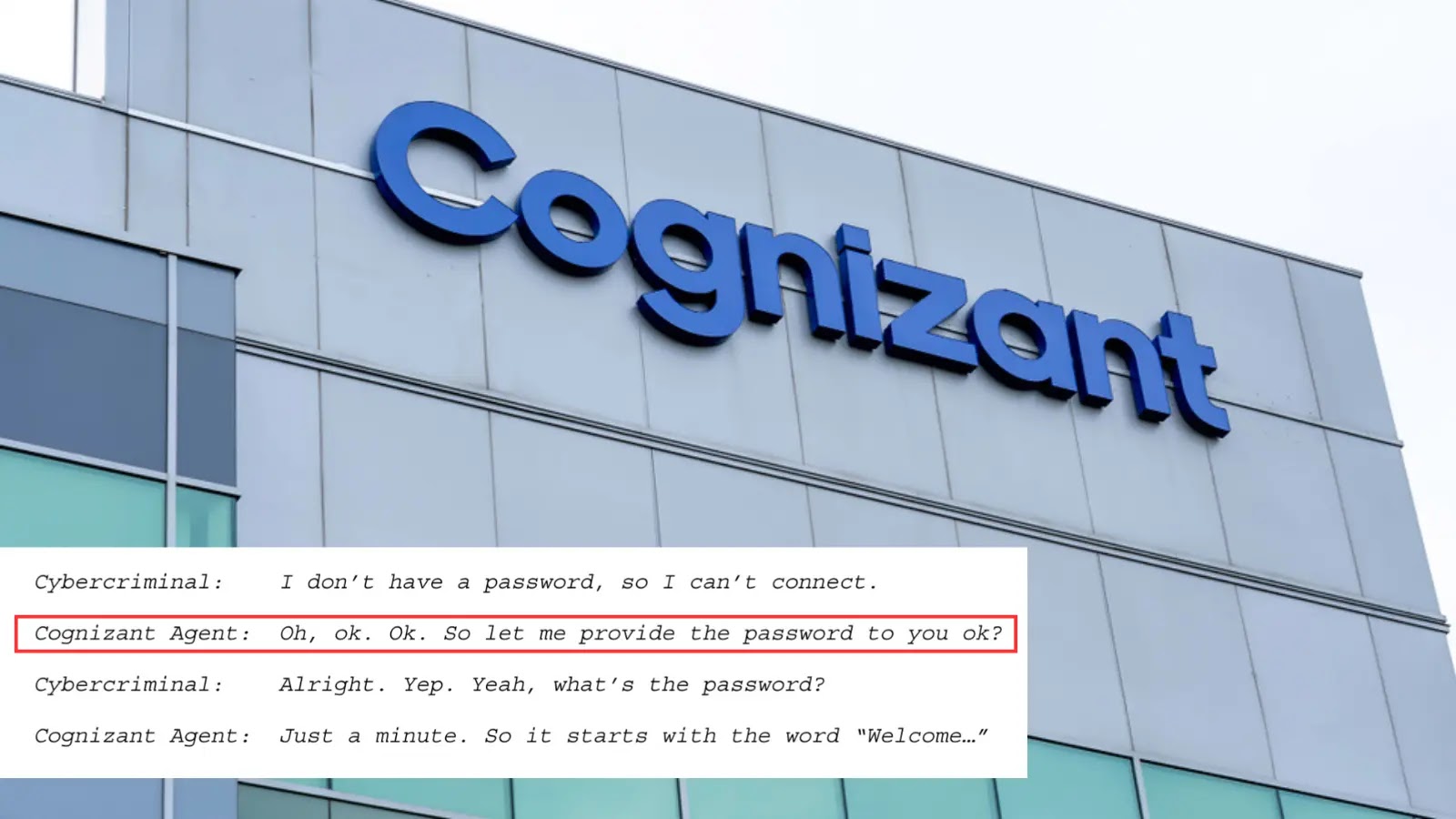
As we progress by 2025, organizations worldwide face an more and more intricate net of information privateness rules.
With new legal guidelines taking impact throughout a number of jurisdictions and current frameworks changing into extra stringent, attaining compliance has by no means been more difficult or important.
Firms should adapt shortly to keep away from hefty penalties whereas sustaining client belief in an period the place information safety has turn into a aggressive benefit.
The Increasing Regulatory Patchwork
The worldwide information privateness panorama continues to evolve quickly, with important developments reshaping compliance necessities throughout areas. In america alone, the variety of complete state privateness legal guidelines in drive will develop to 16 by year-end.
5 new state legal guidelines took impact in January 2025 in Delaware, Iowa, Nebraska, New Hampshire, and New Jersey, with further laws coming into drive in Minnesota and Tennessee (July 2025) and Maryland (October 2025).
“The patchwork of complete state privateness legal guidelines persevering with to develop has led many corporations in the direction of a ‘nationwide strategy,’” notes a current business report, “adopting compliance plans that construct on the commonalities and account for the outlier provisions among the many legal guidelines.”
Past America’s borders, a number of main privateness frameworks are reaching implementation milestones this 12 months.
India’s Digital Private Knowledge Safety Act is predicted to be absolutely operational in 2025, whereas China carried out necessary information safety compliance audits starting Could 1.
Vietnam’s new Private Knowledge Safety Regulation will come into drive in January 2026, and Brazil continues amending its Common Knowledge Safety Regulation.
Key Compliance Challenges and Approaches
Organizations face a number of crucial challenges in attaining compliance throughout these various frameworks. Cross-border information transfers stay notably problematic, with various necessities throughout jurisdictions complicating worldwide enterprise operations.
“Knowledge localization necessities in nations together with China and Russia mandate native storage of sure information varieties, forcing organizations to spend money on regional infrastructure and modify information architectures,” explains one privateness knowledgeable.
To successfully navigate these challenges, privateness professionals suggest implementing complete information privateness frameworks that outline clear insurance policies for information dealing with.
Common danger assessments have turn into important for figuring out vulnerabilities in safety controls and serving to organizations prioritize actions to mitigate potential threats.
A current business evaluation notes that “a structured strategy to danger assessments improves safety preparedness. “Figuring out and addressing vulnerabilities earlier than they result in breaches strengthens information privateness and regulatory compliance whereas decreasing monetary and authorized dangers.”
Embracing Expertise Options
Privateness-enhancing applied sciences (PETs) are more and more crucial to compliance methods in 2025.
These embody homomorphic encryption, differential privateness, and federated studying. These allow information evaluation with out exposing uncooked info, which is especially invaluable for sectors like finance, healthcare, and AI growth.
In response to expertise analysts, “PETs permit companies to leverage the growing quantity of information whereas making certain private or delicate info stays personal. “
Synthetic intelligence performs a twin function within the privateness panorama. Whereas it introduces new considerations about information safety, AI additionally provides enhanced capabilities for monitoring compliance, detecting anomalies, and automating privateness safeguards.
In the meantime, Zero-trust architectures grew to become the usual safety mannequin in 2025. They’re constructed on the precept of “by no means belief, all the time confirm” to make sure each entry request is authenticated, approved, and repeatedly monitored.
Greatest Practices for 2025 Compliance
Organizations attaining profitable compliance in 2025 are implementing a number of constant practices:
Knowledge minimization has turn into a cornerstone technique, with corporations amassing solely the minimal crucial info for particular functions. This strategy reduces breach dangers and helps meet regulatory necessities throughout a number of frameworks.
Worker coaching stays crucial, as human error continues to be a number one trigger of information breaches. Common training on safety practices, phishing prevention, and regulatory necessities strengthens a company’s total privateness posture.
Privateness insurance policies and documentation require common updates to mirror altering necessities. Business compliance checklists emphasize that companies ought to “frequently replace privateness insurance policies and compliance documentation” to keep up alignment with evolving requirements.
Common audits have turn into commonplace follow, with organizations conducting periodic critiques to evaluate compliance and tackle gaps. Exterior auditors more and more present further assurance of regulatory adherence.
Trying Forward
As we advance by 2025, information privateness compliance will demand important consideration from organizations throughout industries. Firms that succeed on this surroundings view privateness not merely as a regulatory requirement however as a strategic benefit.
With customers more and more privacy-conscious and regulators extra vigilant than ever, investing in strong privateness frameworks, acceptable applied sciences, and ongoing compliance monitoring is not non-obligatory—it’s important for sustainable enterprise operations in our data-driven world.
Discover this Information Fascinating! Observe us on Google Information, LinkedIn, & X to Get Prompt Updates!