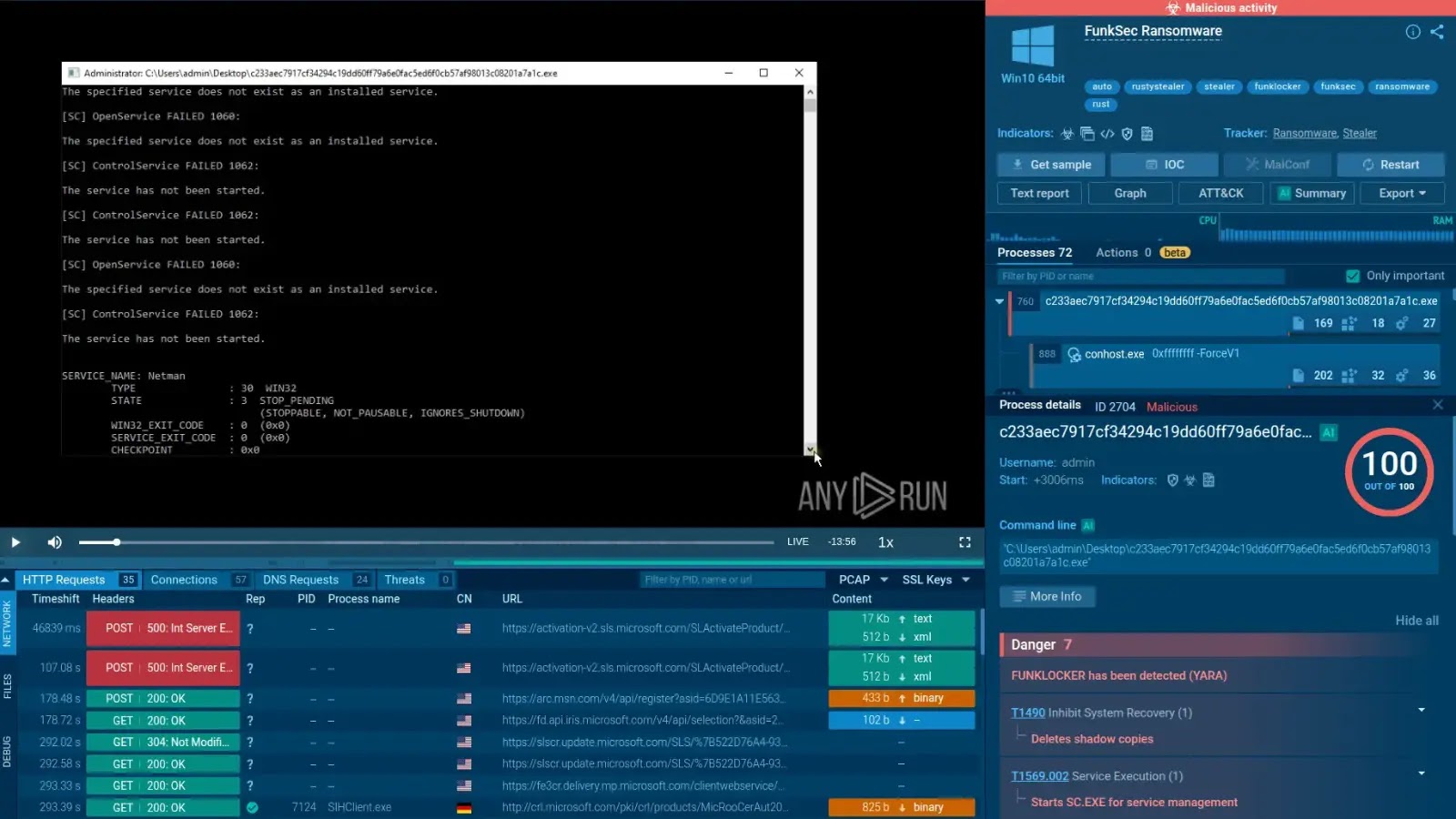
A brand new ransomware pressure, dubbed FunkLocker, is leveraging synthetic intelligence to expedite its growth, whereas counting on the abuse of reputable Home windows utilities to disable safety defenses and disrupt programs.
The ransomware, attributed to a gaggle generally known as FunkSec, highlights a rising development of risk actors utilizing AI to piece collectively malware with various levels of success.
The event of FunkLocker seems to observe an “Ask AI → Paste snippet” mannequin, leading to code that’s usually inconsistent. Whereas some builds of the ransomware are barely practical, others incorporate extra superior options like anti-virtual machine checks.
This AI-assisted method permits for speedy creation however sacrifices the soundness and class seen in malware from extra established teams. These ransomware must be analyzed in secure Sandbox environments.
Upon execution, FunkLocker aggressively terminates a predefined listing of processes and companies. It makes use of normal Home windows command-line instruments like taskkill.exe to cease purposes and sc.exe to halt companies.
This brute-force technique usually generates quite a few errors because it makes an attempt to cease non-existent or protected companies, but it surely finally succeeds in crippling system defenses and purposes.
The listing of focused companies contains safety instruments like Home windows Defender and Home windows Firewall, in addition to important system parts just like the Shell Expertise Host, which causes the sufferer’s display to go black.
Disabling Defenses and Encrypting Recordsdata
In accordance with ANY.RUN sandbox evaluation the FunkLocker closely abuses PowerShell to dismantle safety measures systematically.
It runs a collection of instructions to disable real-time monitoring in Home windows Defender, clear safety and software occasion logs utilizing wevtutil, and bypass the PowerShell execution coverage to permit unrestricted script execution.
To stop system restoration, the ransomware makes use of the Quantity Shadow Service Administrator software (vssadmin.exe) to delete all shadow quantity copies.
This motion removes the sufferer’s potential to revive their system from native backups, a typical approach utilized by ransomware to extend stress on the sufferer.
The encryption course of is carried out completely regionally, which means FunkLocker doesn’t talk with a command-and-control (C2) server to retrieve encryption keys.
Recordsdata are encrypted and appended with the .funksec extension. A ransom be aware is then dropped onto the desktop.
Nonetheless, as a result of the malware usually terminates the Shell Expertise Host service, victims could also be unable to view the be aware with out rebooting the compromised system.
Regardless of its disruptive capabilities, FunkLocker displays indicators of poor operational safety. Researchers have noticed the reuse of Bitcoin pockets addresses throughout completely different victims, and evaluation means that encryption keys are both hardcoded into the malware or derived regionally on the sufferer’s machine.
These vulnerabilities have allowed safety researchers at Avast Labs to develop and launch a public decryptor, providing a restoration path for victims.
Since its emergence in late 2024, the FunkSec group has been linked to assaults on greater than 120 organizations worldwide. The group maintains an information leak web site the place it publicizes stolen data.
Targets span numerous sectors, together with authorities, protection, expertise, and finance, with a big variety of victims positioned in america, in addition to reported incidents in India, Spain, and Mongolia.
IOCs
TypeIndicatorDescriptionFile Hash (SHA256)c233aec7917cf34294c19dd60ff79a6e0fac5ed6f0cb57af98013c08201a7a1cSHA256 hash of the FunkLocker ransomware executable.File Hash (SHA256)e29d95bfb815be80075f0f8bef4fa690abcc461e31a7b3b73106bfcd5cd79033SHA256 hash recognized as being related to a ransom be aware file.File Extension.funksecThe extension appended to information after they’ve been encrypted by the ransomware.Ransom NoteREADME-ZasRvdSR44.md, readme.txtNames used for the ransom be aware dropped on the sufferer’s system. The precise identify can range.Risk ActorFunkSecThe Ransomware-as-a-Service (RaaS) group chargeable for creating and distributing FunkLocker[, , ].Behavioralsc.exe, taskkill.exe, wevtutil.exe, vssadmin.exeAbuses reputable Home windows command-line instruments to cease companies, terminate purposes, clear safety logs, and delete Quantity Shadow Copies.
Observe us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to characteristic your tales.