Pink AI Vary (RAR), an open-source AI pink teaming platform, is remodeling the way in which safety professionals assess and harden AI techniques.
Designed to simulate practical assault eventualities, RAR streamlines the invention, evaluation, and mitigation of AI-specific vulnerabilities by leveraging containerized architectures and automatic tooling.
Key Takeaways1. Arsenal/Goal buttons spin up remoted AI testing containers.2. Recording, standing dashboard, and compose export optimize workflows.3. Coaching modules plus distant GPU brokers scale AI pink teaming.
By integrating RAR into essential infrastructure testing pipelines, organizations can proactively establish weaknesses in machine studying fashions, information dealing with processes, and deployment configurations earlier than adversaries exploit them.
Structure Improve AI Vulnerability Evaluation
On the core of Pink AI Vary is a complicated Docker-in-Docker implementation that isolates conflicting dependencies throughout a number of AI frameworks. RAR’s docker-compose.yml defines companies akin to:
This configuration ensures that every simulated AI goal and testing software runs in its personal container, preserving environmental consistency and enabling speedy resets to baseline.
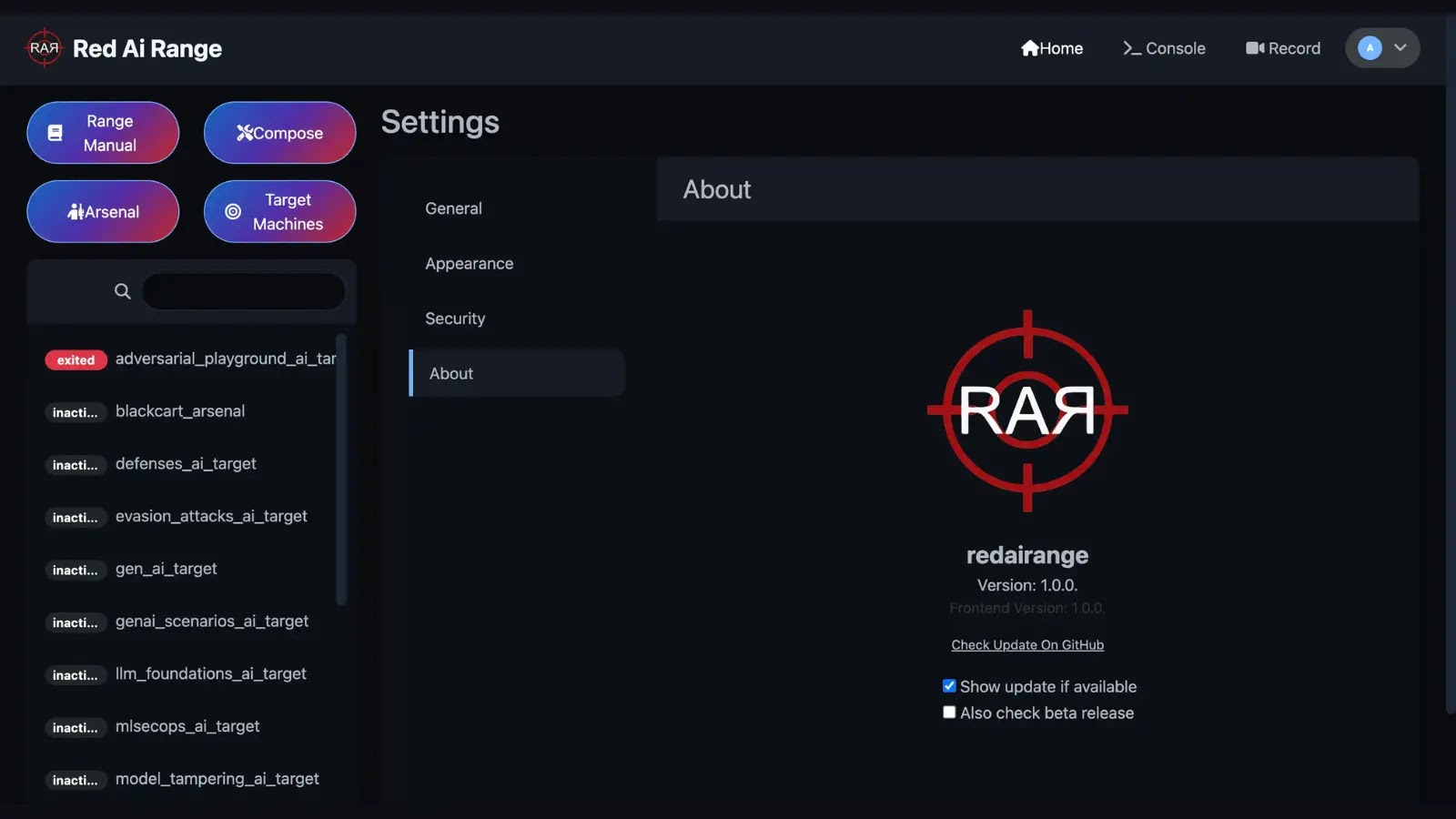
Utilizing the “Arsenal” and “Goal” buttons within the internet UI, pink teamers can deploy vulnerability scanners, adversarial-attack frameworks, and deliberately weak AI fashions, every appended with _arsenal or _ai_target to their stack identify for clear identification.
As soon as containers are up, RAR’s interactive dashboard shows real-time exercise standing exhibiting Energetic, Exited, and Inactive environments—and offers controls to transform working cases into reusable Docker Compose information.
The built-in session recorder successfully captures video recordings and timestamped logs of pink teaming workouts, thereby facilitating complete post-test evaluation and information switch. This software is accessible from GitHub.
Built-in Coaching Modules
Past its core deployment capabilities, Pink AI Vary provides a complete suite of coaching modules that cowl foundational AI safety ideas by way of superior adversarial strategies.
Module subjects vary from poisoning assaults, akin to clean-label backdoor injection, to evasion strategies like Projected Gradient Descent (PGD) and Carlini & Wagner (C&W) assaults.
Every module offers Jupyter Pocket book tutorials, enabling practitioners to experiment interactively with code examples in a managed setting.
RAR additionally helps a distant agent structure, permitting groups to distribute testing workloads throughout GPU-enabled hosts on AWS or on-premises GPU clusters.
Safe authentication between the central RAR console and distant brokers ensures that large-scale vulnerability assessments, particularly these focusing on LLMs or high-compute fashions, might be coordinated seamlessly.
Brokers register through a token-based handshake, after which they seem within the Agent Management Panel for deployment orchestration.
By consolidating AI-specific vulnerabilities, automation instruments, and coaching sources right into a unified framework, Pink AI Vary empowers safety groups to raise their AI pink teaming operations.
As enterprises proceed to undertake AI in essential techniques, integrating RAR into common safety workflows shall be important for uncovering hidden dangers, refining mitigation methods, and sustaining belief in AI-driven companies.
Discover this Story Fascinating! Observe us on Google Information, LinkedIn, and X to Get Extra Prompt Updates.