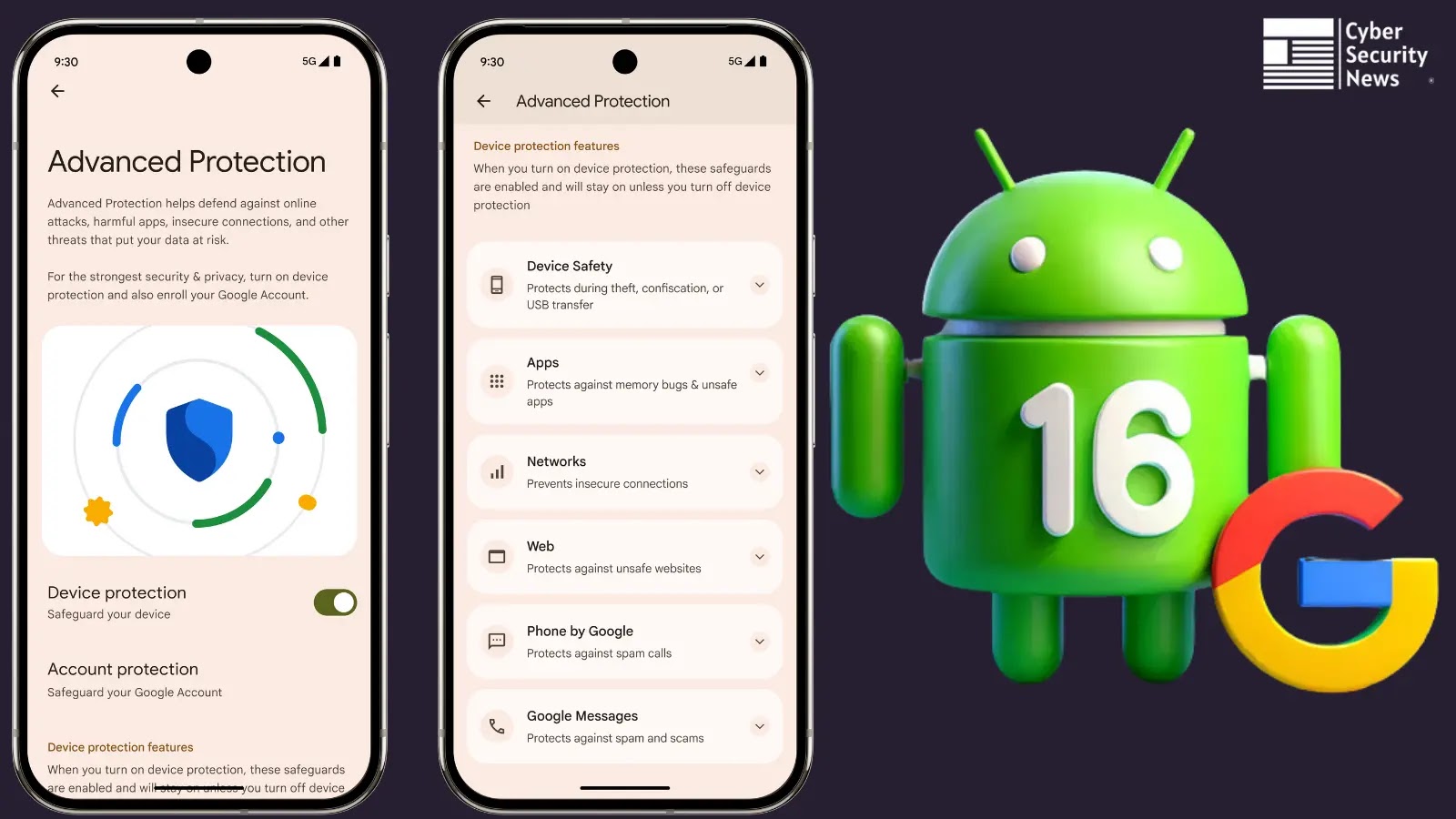
Google has introduced a big enhancement to its Superior Safety Program with the discharge of Android 16, introducing a sturdy device-level safety setting aimed toward safeguarding customers towards subtle cyber threats.
Tailor-made for at-risk people reminiscent of journalists, elected officers, and public figures or anybody prioritizing top-tier safety this replace delivers Google’s strongest cell defenses to this point.
The revamped Superior Safety Program integrates a set of highly effective security measures, combining new instruments with Android’s current top-rated protections.
Designed for simplicity, customers can activate these defenses with ease, making certain minimal disruption whereas fortifying their units towards on-line assaults, dangerous apps, and knowledge breaches.
Key Options of Superior Safety
Greatest-in-Class Safety: Android’s handiest safeguards are enabled by default, providing proactive safety with a seamless, user-friendly expertise.
Protection-in-Depth: As soon as activated, Superior Safety locks essential safety settings to stop unintentional or malicious deactivation, creating a number of layers of protection.
App Integration: This system serves as a single management level, enabling enhanced safety throughout Google apps like Chrome, Google Messages, and Telephone by Google, with plans to incorporate third-party apps sooner or later.
Intrusion Logging: An industry-first characteristic, Intrusion Logging securely shops tamper-resistant gadget logs for forensic evaluation in case of a suspected compromise. This privacy-preserving software, accessible solely to the consumer, will roll out later in 2025 alongside different options like USB safety, rip-off detection integration, and safeguards towards insecure community reconnections.
Superior Safety ensures a complete safety overhaul by managing each new and current options throughout essential areas, making it practically unimaginable for attackers to use vulnerabilities. Google’s “defense-in-depth” method ensures that these protections work in unison, offering peace of thoughts for customers going through focused threats.
Whereas Android 16 customers can instantly entry a core set of Superior Safety options, Google plans to increase this system with extra capabilities later this 12 months. The corporate emphasised its dedication to evolving this system to maintain tempo with rising threats, making certain Android stays a frontrunner in cell safety.
Methods to Get Android 16
Google provides a number of methods to expertise Android 16, catering to customers, builders, and testers. Right here’s how one can get began:
1. Get Android 16 on a Google Pixel Gadget
The best method to attempt Android 16 is by enrolling a supported Google Pixel gadget within the Android Beta for Pixel program. This quick, easy course of delivers common over-the-air (OTA) updates, together with Quarterly Platform Releases (QPRs), all through the discharge cycle. An information backup is advisable, although a full reset is often not required.
Supported Pixel Gadgets:
Pixel 6, 6 Professional, 6a
Pixel 7, 7 Professional, 7a
Pixel Fold, Pixel Pill
Pixel 8, 8 Professional, 8a
Pixel 9, 9 Professional, 9 Professional XL, 9 Professional Fold, 9a
Enrollment: Be part of the beta program to obtain OTA updates. After making use of a secure launch, customers can decide out with out a knowledge wipe for a restricted time.
Guide Set up: For extra management (e.g., automated or regression testing), use the Android Flash Software or manually flash a system picture from the Pixel downloads web page. Flashing a beta construct routinely enrolls the gadget in OTA updates for subsequent builds.
2. Get Android 16 Beta on a Associate Gadget
Android 16 Beta can be accessible on choose units from associate producers, together with HONOR, iQOO, Lenovo, OnePlus, OPPO, realme, vivo, and Xiaomi. Every associate supplies system photos for obtain and flashing, with some providing OTA supply. Go to the associate’s web site through the Android 16 Beta units web page for set up directions and help assets. Suggestions and bug reviews ought to be submitted by means of every associate’s devoted channel.
3. Set Up the Android Emulator
Builders can discover Android 16 options and APIs utilizing the Android Emulator, best for testing conduct adjustments throughout numerous gadget varieties. To arrange:
Set up the most recent Preview model of Android Studio.
Within the SDK Supervisor, choose the most recent Android Emulator model.
Within the Gadget Supervisor, create a digital gadget (telephone or pill) utilizing a supported Pixel gadget definition (e.g., Pixel Pill or Pixel Fold).
Obtain the Android 16 system picture (“Baklava”) and finalize the digital gadget settings.
Begin the digital gadget to start testing.
For big-screen testing, configure pill or foldable units. The resizable emulator permits toggling between telephone, foldable, and pill configurations, together with folded/unfolded states for foldables, streamlining structure validation and runtime testing.
Methods to Uncover Weak Exterior Property Related to a Area or an IP? -> Strive Cyber Asset Finder for Free