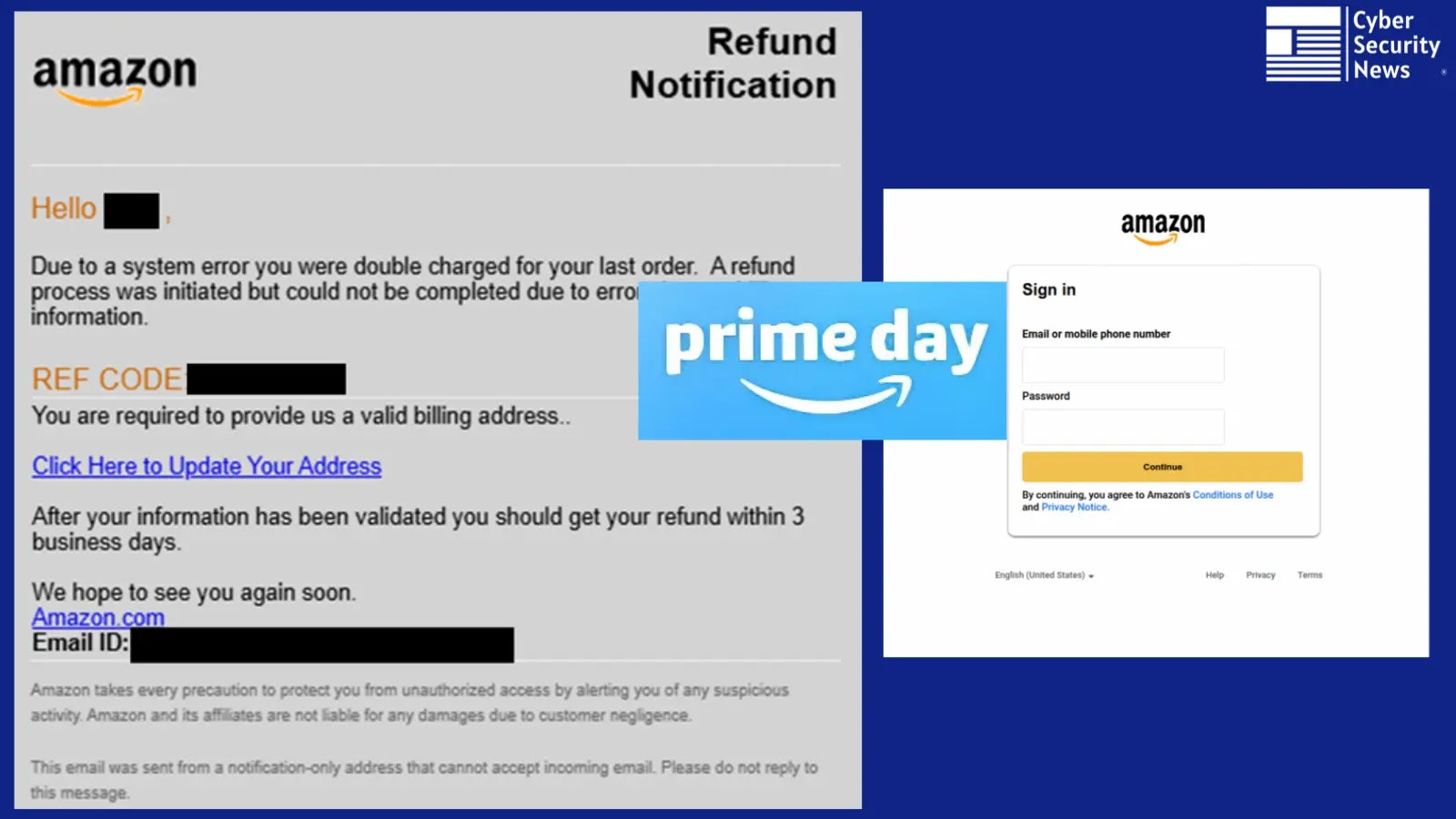
In latest months, a surge in focused intrusions attributed to the Iranian-aligned risk group APT35 has set off alarm bells throughout authorities and navy networks worldwide.
First detected in early 2025, the marketing campaign leverages custom-built malware to infiltrate safe perimeters and harvest consumer credentials.
Preliminary indicators of compromise level to spear-phishing emails with HTML attachments that deploy a multi-stage payload as soon as opened, silently establishing a foothold within the goal atmosphere.
Evaluation of the assault chain reveals that the preliminary vector typically entails weaponized Microsoft Workplace paperwork exploiting CVE-2023-23397 to bypass Outlook’s safety mannequin.
The embedded code downloads a PowerShell stager, which then fetches the first credential-stealer module from a distant command-and-control (C2) server.
Stromshield researchers recognized this conduct throughout a compromise of a protection ministry community in April, noting the seamless transition from doc exploit to stealthy reconnaissance and credential exfiltration.
As soon as deployed, the malware masquerades as respectable system processes to evade detection. It hooks into the Home windows Safety Help Supplier Interface (SSPI) to intercept NTLM challenge-response exchanges, capturing hashed credentials in reminiscence.
These hashes are then relayed to the attacker’s infrastructure, the place a mixture of hash-cracking and pass-the-hash strategies unlock privileged accounts on high-value servers.
The impression has been vital: a number of accounts inside navy communications networks have been compromised with out triggering standard intrusion detection techniques.
In a single documented case, the stager code resembles the next snippet, illustrating how the malware invokes SSPI hooks in PowerShell:-
$sspi = Add-Kind -MemberDefinition @”
[DllImport(“secur32.dll”, CharSet=CharSet.Auto)]
public static extern int LsaLogonUser(
IntPtr LsaHandle, string OriginName, uint LogonType,
uint LogonPackage, IntPtr AuthenticationInfo,
uint AuthenticationInfoLength, IntPtr LocalGroups,
IntPtr SourceContext, out IntPtr ProfileBuffer,
out uint ProfileBufferLength, out uint LogonId,
out IntPtr Token, out uint Quotas, out uint SubStatus);
“@ -Identify “Lsa” -Namespace “WinAPI” -PassThru
An infection Mechanism
The an infection mechanism hinges on a two-stage downloader that first discerns the sufferer’s atmosphere.
Upon profitable doc exploit, the preliminary stager performs atmosphere checks—querying registry keys for safety instruments and scanning loaded kernel modules.
If a acknowledged evaluation sandbox is detected, execution halts to thwart reverse-engineering efforts. In any other case, the stager decodes a base64-encoded second-stage payload, writing it to %AppDatapercentRoamingmsnetcache.dll earlier than loading it through rundll32.exe.
Screenshot from viliam.ude-final[.]on-line (Supply – Stormshield)
This DLL implements the SSPI hook logic, intercepts credentials, after which performs HTTP GET requests to the C2 area over port 443, mixing site visitors with respectable HTTPS periods.
Total, the marketing campaign displays APT35’s rising sophistication in embedding deep inside trusted processes and leveraging native APIs to seize credentials with out dropping overt artifacts.
Continued vigilance and superior behavioral monitoring are essential to detect such stealthy intrusions earlier than important entry is compromised.
Observe us on Google Information, LinkedIn, and X to Get Extra Immediate Updates, Set CSN as a Most popular Supply in Google.