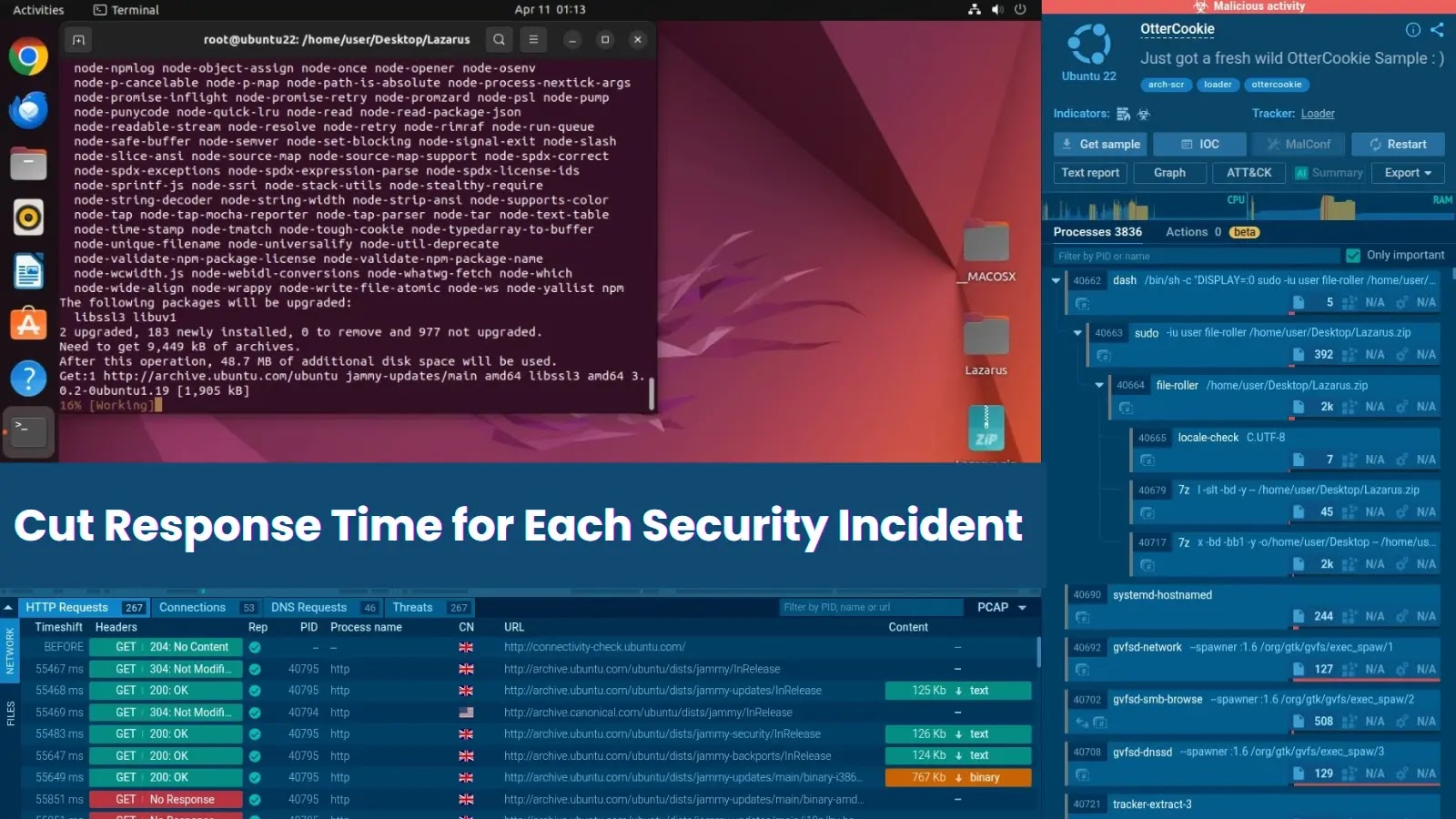
A current marketing campaign by Chinese language state-sponsored menace actor APT41 has unveiled a novel exploitation of Google Calendar for malware command-and-control (C2) operations, marking a big escalation in cyberespionage ways.
The group, tracked underneath aliases together with BARIUM and Brass Storm, focused Taiwanese authorities entities by way of a multi-stage assault chain combining spearphishing, image-based payload supply, and covert C2 through broadly trusted cloud providers.
The marketing campaign throughout forensic evaluation of a compromised authorities web site, revealing a complicated workflow designed to evade conventional detection mechanisms.
The assault begins with spearphishing emails distributing ZIP archives labeled “出境海關申報清單.zip” (“Export Customs Declaration Listing.zip”).
Resecurity researchers recognized that inside, the victims encounter a shortcut LNK file masquerading as a PDF (“申報物品清單.pdf.lnk”) and a picture folder containing seven information.
Whereas information 1–5 show legit arthropod specimens, 6.jpg and seven.jpg harbor encrypted malware elements. When executed, the LNK file shows a decoy PDF about export rules whereas silently deploying APT41’s ToughProgress malware suite.
Encrypted malware elements (Supply – Resecurity)
This three-module framework—PLUSDROP, PLUSINJECT, and TOUGHPROGRESS—combines memory-resident execution, course of hollowing, and cloud-based C2 to take care of persistence.
Resecurity analysts famous the marketing campaign’s innovation lies in its abuse of Google Calendar occasions for bidirectional communication. In contrast to conventional C2 servers, this method blends malicious site visitors with legit Google Workspace API requests, complicating network-based detection.
Rundll32.exe makes an attempt to decrypt 6.jpg (Supply – Resecurity)
The Techniques, Methods, and Procedures (TTPs) map to 14 distinct MITRE ATT&CK entries, spanning preliminary entry (T1566.001) to exfiltration (T1041).
Covert C2 Infrastructure By way of Google Calendar Occasion Manipulation
The TOUGHPROGRESS module establishes persistence by creating Google Calendar occasions dated again to 2023, embedding AES-encrypted instructions inside occasion descriptions.
The malware periodically checks these occasions utilizing OAuth2 tokens, mimicking legit calendar synchronization habits.
Instructions are decrypted utilizing a hardcoded key (0x7D in XOR operations) and executed through injected svchost.exe processes.
// Pattern decryption routine for calendar occasion information
void decrypt_payload(char* encrypted_data, size_t len) {
const char KEY = 0x7D;
for (size_t i = 0; i < len; i++) {
encrypted_data[i] ^= KEY;
}
}
Execution outcomes are exfiltrated by creating new calendar occasions with BASE64-encoded output appended to seemingly benign descriptions.
For example, an occasion titled “Finances Assembly Q3” may include exfiltrated registry information inside its description area.
This method capitalizes on the trustworthiness of Google providers—76% of enterprise firewalls whitelist *.google.com domains, enabling undisturbed information transit.
The malware additional obfuscates C2 patterns utilizing dynamically generated Cloudflare Staff subdomains (*.trycloudflare[.]com) as proxy relays.
These domains resolve to Google Calendar API endpoints, making a hybrid infrastructure that blends bulletproof internet hosting with legit cloud providers.
Key Indicators of Compromise (IOCs) embody the malicious 6.jpg (SHA-256: 50124174a4ac0d65bf8b6fd66f538829d1589edc73aa7cf36502e57aa5513360) and seven.jpg information, which include XOR-encrypted PE headers.
Reminiscence evaluation reveals signature evasion methods comparable to:-
API hashing: Vital capabilities like LdrLoadDll are resolved through customized hash algorithms fairly than direct imports
Part stomping: Malware overwrites .textual content sections of legit processes with malicious code
Shimcache manipulation: Timestamps of malicious information are spoofed to match system binaries
; Instance of API hashing for kernel32!CreateProcessA
mov edi, 0x8F1D8844 ; Precomputed hash worth
name resolve_api_by_hash
take a look at eax, eax
jz error_handler
Defenders ought to monitor for irregular svchost.exe cases with open connections to *.googleapis.com/calendar/v3 and examine calendar occasion metadata for BASE64 blobs.
Resecurity recommends implementing software allowlisting for rundll32.exe and constraining Google Workspace API permissions to mitigate related campaigns.
This operation reveals the APT41’s continued evolution in exploiting belief relationships between customers, software program, and cloud suppliers.
As geopolitical tensions heighten, such hybrid C2 mechanisms will seemingly proliferate amongst state-aligned menace actors searching for believable deniability.
Velocity up and enrich menace investigations with Menace Intelligence Lookup! -> 50 trial search requests