Two important vulnerabilities in Aviatrix Controller, a Software program-Outlined Networking (SDN) utility that allows cloud connectivity throughout totally different distributors and areas.
The vulnerabilities allowed attackers to bypass authentication and execute distant code with root privileges, probably compromising whole cloud infrastructures.
Abstract
1. Two vulnerabilities (CVE-2025-2171 and CVE-2025-2172) in Aviatrix Controller allowed attackers to bypass administrator authentication and execute distant code.
2. Attackers gained root entry by exploiting a command injection flaw within the file add characteristic, utilizing malicious filenames with tab characters.
3. Profitable exploitation granted attackers centralized management over cloud gateways and APIs, probably main to a whole cloud setting takeover.
4. Aviatrix launched safety patches for variations 8.0.0, 7.2.5090, and seven.1.4208, addressing vulnerabilities in Controller variations 7.2.5012 and earlier.
Essential Aviatrix Controller Vulnerabilities
Mandiant safety researchers disclosed safety flaws, tracked as CVE-2025-2171 and CVE-2025-2172, affected Aviatrix Controller variations 7.2.5012 and prior.
CVE-2025-2171 represents an administrator authentication bypass vulnerability, whereas CVE-2025-2172 entails authenticated command injection.
Throughout a pink group engagement, Mandiant researchers found that the authentication bypass could possibly be exploited by a weak password reset mechanism.
Exploitation steps
The system generated 6-digit password reset tokens starting from 111,111 to 999,999, creating solely 888,888 distinctive candidates with a 15-minute validity window.
The researchers efficiently brute-forced the administrator account after 16 hours and 23 minutes of steady makes an attempt.
The Aviatrix Controller structure consists of a Python 3.10 codebase bundled utilizing PyInstaller, referred to as by a PHP front-end that processes HTTP requests. When customers try and log in, the system executes instructions like:
After gaining preliminary entry, researchers recognized a command injection vulnerability within the file add performance.
The system’s upload_file() operate allowed attackers to regulate partial filenames, together with tab characters, which could possibly be exploited to smuggle command-line arguments.
The vulnerability exploited the shlex.break up() operate utilized by the system to tokenize command strings.
By importing information with specifically crafted names containing tab characters, attackers may inject further arguments into shell instructions.
For instance, a filename like foobar.foo{TAB}–bar{TAB}–baz can be tokenized as separate command arguments.
Researchers demonstrated the exploit by focusing on the Proxy Admin utility’s CA certificates set up characteristic, which used the cp command to repeat uploaded information.
By means of cautious argument injection, they overwrote /and so on/crontab with malicious content material, reaching persistent root entry:
CVEsAffected ProductsImpactExploit PrerequisitesCVE-2025-2171Aviatrix Controller variations 7.2.5012 and priorAdministrator authentication bypass permitting unauthorized administrative accessNetwork entry to Aviatrix Controller interface, potential to provoke password reset processCVE-2025-2172Aviatrix Controller variations 7.2.5012 and priorAuthenticated command injection resulting in distant code execution with root privilegesValid administrator credentials ( obtained through CVE-2025-2171), entry to file add performance
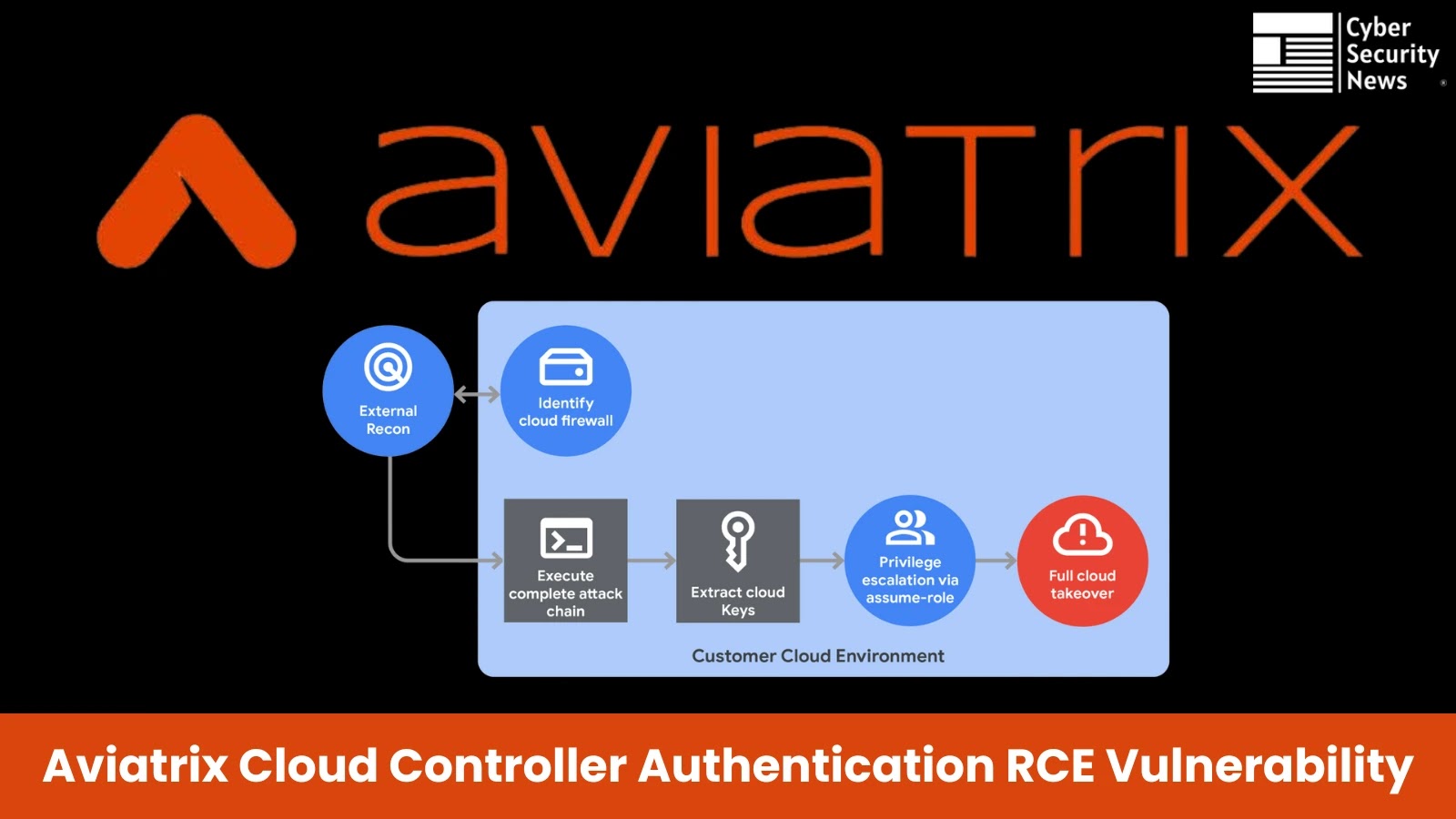
Cloud Infrastructure Compromise
The profitable exploitation offered attackers with root entry to the Aviatrix Controller, which serves as a centralized part managing cloud gateways and APIs throughout a number of cloud suppliers.
From this place, researchers may question the AWS IMDSv2 endpoint to acquire ephemeral cloud credentials and carry out function assumption to realize broader cloud entry.
The assault chain demonstrates how compromising the Aviatrix Controller can result in full cloud setting takeover, because the controller maintains privileged entry to deployed gateways and cloud APIs throughout totally different areas and distributors.
Aviatrix launched safety patches on March 31, 2025, for variations 8.0.0, 7.2.5090, and seven.1.4208, addressing vulnerabilities in Controller variations 7.2.5012 and earlier.
Organizations utilizing affected variations ought to instantly improve to the patched releases to stop potential compromise of their cloud infrastructure.
Are you from SOC/DFIR Groups! – Work together with malware within the sandbox and discover associated IOCs. – Request 14-day free trial