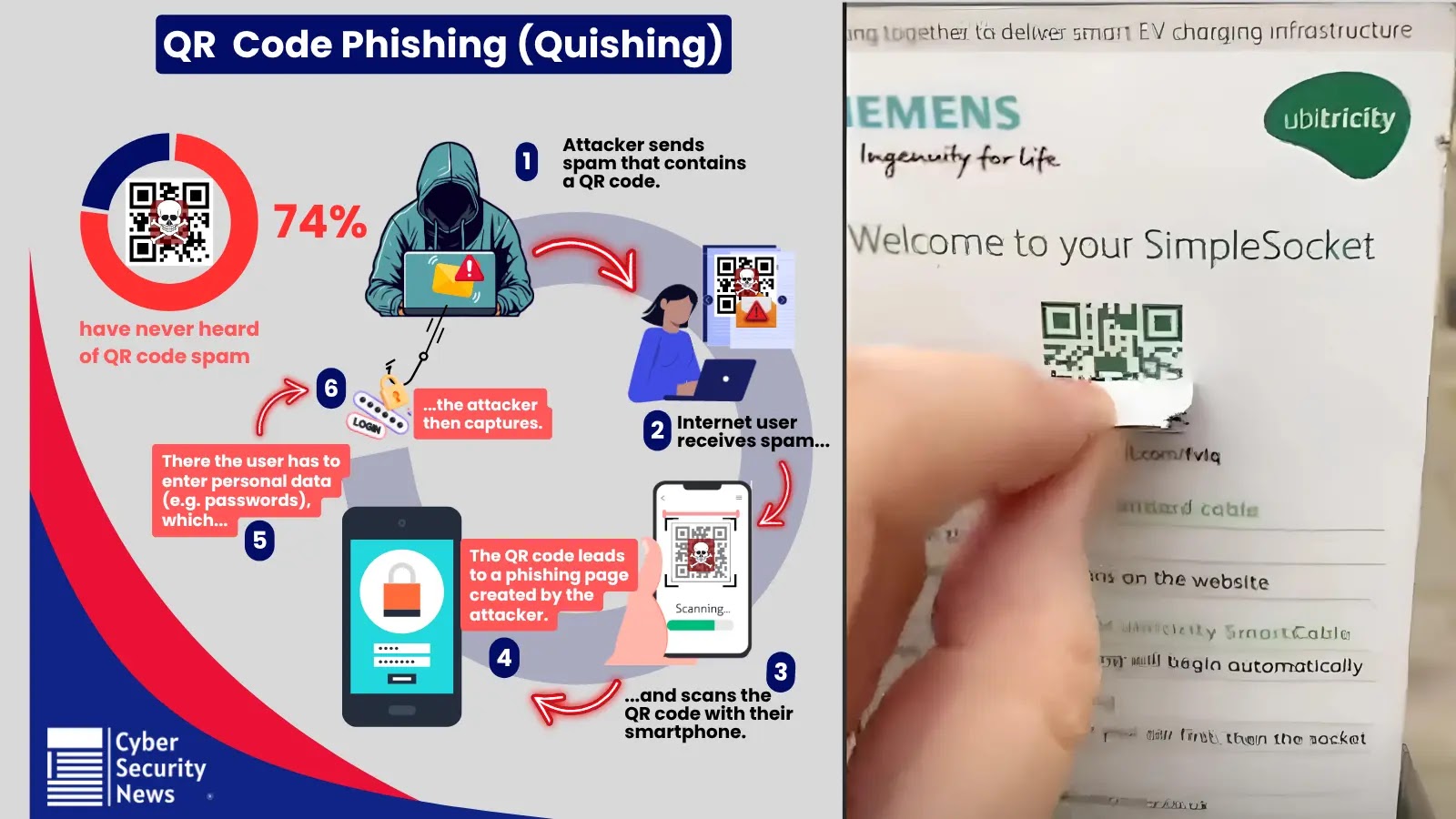
The surge in Digital Well being Information (EHRs), telemedicine, and interconnected medical units has cast a intricate healthcare ecosystem ripe for cyber exploitation.
Sturdy community safety options are non-negotiable to defend delicate affected person information from superior threats.
Healthcare-focused suppliers ship multi-layered protections together with IDS/IPS, end-to-end encryption, zero-trust entry controls, and proactive vulnerability administration powered by risk intelligence and strict HIPAA compliance.
This method fortifies affected person privateness, ensures operational resilience, and upholds regulatory requirements.
Community Safety Musts: The 7-Level Guidelines – Obtain Free – E-Guide
Why is Community Safety is Essential in Healthcare?
The healthcare business’s dependence on digital well being information (EHRs) and interconnected medical units creates a digital panorama ripe for cyberattacks.
Community safety safeguards this delicate ecosystem by using firewalls and intrusion detection methods to thwart unauthorized entry.
Encryption scrambles information in transit and at relaxation, rendering it ineffective even when intercepted. Multi-factor authentication strengthens login protocols, and sturdy entry controls dictate which customers can entry particular information.
Common safety patches handle software program vulnerabilities, and vigilant community segmentation limits the blast radius of a possible breach.
By implementing these measures, healthcare organizations can guarantee affected person information privateness, stop disruptions to essential medical units, and preserve the integrity of life-saving companies.
Measures to Improve Community Safety in Healthcare
Healthcare organizations can fortify their community defenses by implementing a multi-layered method, starting with role-based entry controls (RBAC) that strictly restrict person permissions to delicate information.
Community segmentation can additional isolate essential methods, whereas firewalls and intrusion detection and prevention methods (IDS/IPS) actively block and monitor malicious visitors.
Information encryption, each at relaxation and in transit, safeguards affected person data even throughout a breach.
Healthcare establishments should prioritize endpoint safety by implementing sturdy password insurance policies with multi-factor authentication (MFA) and deploying endpoint detection and response (EDR) options to establish and comprise threats on particular person units.
Common vulnerability assessments and penetration testing pinpoint weaknesses within the community, permitting for well timed remediation and a continually evolving safety posture.
Prime 3 Greatest Community Safety Suppliers for Healthcare
Perimeter 81: You’ll be able to fulfill HIPAA laws and shield PHI with Perimeter 81’s cloud, on-site, and in-transit safety.
Palo Alto Networks: Palo Alto Networks presents healthcare-specific cybersecurity options for community safety, information safety, and compliance with HIPAA, PCI DSS, and GDPR requirements.
Fortinet: Fortinet makes use of instruments like FortiDeceptor to deceive and eradicate threats early within the assault chain numerous applied sciences and techniques to safe healthcare networks, information, and units.
Prime 10 Community Safety Suppliers for Healthcare Trade and its Options
Community Safety Suppliers for Healthcare IndustryFeaturesStandout FeaturePricing1. Perimeter 811. Single Signal-On (SSO) facilitates entry throughout a number of purposes utilizing one login.2. Zero Belief Community Entry secures person entry primarily based on steady verification.3. DNS filtering prevents entry to dangerous websites to attenuate dangers.4. Safe Net Gateway offers net filtering to dam malicious web sites.Intrusion monitoring for information protection30 Days Free Trail2. Palo Alto Networks1. Excessive-performance firewalls are tailor-made for advanced healthcare networks.2. Segmented community entry offers detailed management over community entry and information stream.3. Multi-factor authentication strengthens entry management with further safety layers.4. Endpoint safety protects endpoints with superior risk detection and response.Zero Belief Safety controls and verifies all person and system entry.30 Days Free Trail3. Fortinet1. Excessive-performance firewalls are tailor-made for advanced healthcare networks.2. Segmented community entry offers detailed management over community entry and information stream.3. Multi-Issue authentication strengthens entry management with further safety layers.4. Endpoint safety protects endpoints with superior risk detection and response.Intrusion prevention actively blocks threats earlier than they attain community units.Free demo/ path for 15 days4. Cisco1. Safe SD-Entry offers scalable community entry management and segmentation.2. Endpoint and Malware Safety presents sturdy defenses in opposition to a wide range of threats.3. Cloud-Delivered Firewall ensures safe 4. Web entry and utility utilization.5. Incident response options sturdy capabilities for detecting and responding to threats.The Zero Belief Framework implements stringent entry controls throughout all community sources.free5. SymantecAdvanced Menace Safety detects and blocks subtle assaults.Cloud Safety ensures the safety of cloud purposes and companies.Information Loss Prevention helps stop delicate information from leaving the group.Net and Community Safety features shield in opposition to web-based and network-based threats.Endpoint Safety safeguards units in opposition to malware and different threats.30 Days Free demo6.Pattern MicroComprehensive Safety presents sturdy safety throughout IT, OT, and CT environments.Actual-Time Analytics and Menace Intelligence present proactive risk mitigation.Automation and Scalability options reduce handbook duties and permit adaptation to altering wants.Person-Pleasant Interface simplifies the navigation and utilization of safety features.Centralized Administration permits administration of safety insurance policies and monitoring threats from a single console.30 Days Free Trail7.ImprivataDigital Identification Options streamline scientific experiences and shield delicate information.Multifactor Authentication enhances safety throughout healthcare methods.Privileged Entry Administration (PAM) secures and manages entry for high-level person accounts.Compliance with main requirements similar to HIPAA, NIST, and SOC compliance ensures adherence to laws.Single Signal-On (SSO) simplifies entry to scientific methods and purposes.30 Days Free Trail8. CyberArkSecures privileged entry vulnerabilities to guard essential healthcare data.Adaptable safety options don’t disrupt ongoing enterprise operations.Enhances IT productiveness by specializing in strategic duties.Helps compliance and strengthens total cybersecurity posture.Automation capabilities stop human error in IT operations.free demo9. ZscalerZero Belief Alternate prevents cyber threats by securely connecting customers, units, and purposes.Safe Entry to Public and Personal Apps ensures secure and quick connectivity.Actual-time Menace Prevention and Intelligence supply safety in opposition to rising threats.Simplified IT Operations scale back complexity with cloud-native options.Multi-Tenant Cloud Structure offers scalable and built-in safety as a service.30 Days Free demo10. CrowdStrikeThreat Intelligence presents insights into adversaries’ ways, methods, and procedures.Subsequent-Era Antivirus protects in opposition to all sorts of malware with machine studying.Managed Menace Looking identifies and mitigates threats in actual time.Incident Response and Proactive Companies assist put together and reply to essential safety incidents.Cloud-Native Endpoint Safety offers superior protection mechanisms for healthcare methods.free
10 Greatest Community Safety Suppliers for Healthcare 2026
Perimeter 81
Palo Alto Networks
Fortinet
Cisco
Symantec
Pattern Micro
Imprivata
CyberArk
Zscaler
CrowdStrike
1. Perimeter 81
Perimeter 81
Perimeter 81 presents a cloud-based safe entry service edge (SASE) platform that integrates networking and safety instruments to help healthcare suppliers in complying with HIPAA, GDPR, SOC 2, and different laws.
It presents a complete safety resolution via a centralized administration portal. It offers a complete cloud utilization visibility resolution that evaluates potential dangers and safeguards delicate well being data (PHI).
It additionally enforces information entry and transmission management insurance policies to forestall unauthorized entry and information loss.
Encrypting information at relaxation and in transit eliminates the necessity for breach notification in case of a breach.
Moreover, it presents a hardware-free cloud VPN for safe distant entry, application-by-application entry permissions, complete logging, and centralized administration
Why will we Advocate It?
Simplifies safe community, cloud, and utility entry for the fashionable and cellular workforce
HIPAA-compliant and presents options similar to 2FA, simple scalability, cost-effectiveness, and ease of use
Helps healthcare suppliers meet compliance necessities by offering IT groups with a robust array of unified networking and cybersecurity instruments
Makes use of a multi-layer method to guard affected person information
Presents a single portal for administration
Professionals:
Streamlines assembly HIPAA and different laws.
Offers insights into cloud utilization for higher safety.
Encrypts information and enforces entry controls.
Cons:
It might not eradicate breach notification necessities.
Scaling prices for extra intensive networks.
2. Palo Alto Networks
Palo Alto Networks
Palo Alto Networks presents a unified cybersecurity platform for healthcare organizations by integrating community safety, cloud safety, and safety operations to handle the business’s distinctive challenges.
Permits healthcare suppliers to securely leverage cloud-based options, information analytics, and AI/ML for improved affected person care and information sharing.
The platform strengthens regulatory compliance and secures distant workforces and telemedicine practices via automation and constant safety controls.
By consolidating safety instruments and automating risk evaluation, healthcare organizations can scale back administration complexity and prices whereas enhancing their total cybersecurity posture.
It permits them to ship environment friendly and safe affected person care wherever throughout the evolving healthcare panorama.
Professionals:
Integrates totally different safety options into one platform for simpler administration and decreased complexity.
Presents options like risk evaluation, automation, and constant safety controls to strengthen healthcare cybersecurity.
It permits safe use of the cloud, information analytics, and AI/ML for higher affected person care and information sharing.
Reduces safety sprawl and saves cash by unifying safety administration.
Adapts to the evolving healthcare panorama and rising variety of linked units.
Cons:
It is likely to be advanced to arrange and require experience to handle the platform successfully.
The price of the platform itself is likely to be a consideration for smaller healthcare organizations.
Why will we advocate it?
Protects affected person information and stays forward of threats.
Delivers value-based care with safe clouds, information analytics, and AI/ML.
Improves safety for the distant workforce and telemedicine sufferers.
Unifies community and cloud safety coverage and administration.
It helps handle expertise dangers and elevates cyber resilience for affected person security and privateness.
3. Fortinet
Fortinet
Professionals:
It combines numerous safety features right into a single system, simplifying administration.
Integrates safety with bodily safety methods for higher total safety.
Presents SD-WAN and safe networking options particularly for department places of work.
Delivers sturdy efficiency even with information encryption.
Cons:
It might be costly, relying on the healthcare group’s finances.
The Fortinet Safety Material is a complete cybersecurity resolution for the healthcare business.
Successfully tackles the obstacles of digital transformation by providing complete safety options for networks, information, and units.
Presents options similar to clever segmentation, Community Entry Management (NAC), endpoint safety, and Identification and Entry Administration (IAM) to safe Web of Medical Issues (IoMT) units and customers.
Integrates bodily safety features with cybersecurity options, offering a complete view of safety posture.
It additionally addresses low latency and high-performance processing wants for encrypted visitors, which helps healthcare organizations adjust to laws and enhance operational effectivity.
Why will we advocate it?
Integrates safety and networking features
Secures internet-of-medical-things (IoMT) units
Complies with laws
Responds to cyber threats
Delivers high-performance processing
Secures department areas
4. Cisco
Cisco
Cisco presents healthcare suppliers a set of applied sciences to enhance affected person care, workers workflows, and effectivity.
Their options embrace safe networking for connecting sufferers, suppliers, and workers and collaboration instruments for distant care supply.
Safety is a major focus, with Cisco offering risk evaluation and safety resilience methods.
By enabling a hybrid work mannequin, Cisco’s expertise helps alleviate clinician burnout and enhance the workers expertise.
With intensive expertise within the healthcare business, it’s a trusted accomplice for hospitals and clinics worldwide.
Why will we advocate it?
It presents options to attach sufferers, suppliers, and workers.
Safety options to guard affected person data.
Assist healthcare organizations enhance affected person care.
The clinician’s expertise will be improved with Cisco’s options.
Information-driven care choices will be made.
Professionals:
Improves workflows all through healthcare organizations.
Permits safe connections between suppliers, sufferers, and workers.
Cons:
It requires constructing a technique for safety resilience.
It’s advanced to implement and handle, requiring expert IT workers, which may burden smaller healthcare organizations with restricted IT sources.
It’s costly, with licensing charges and probably excessive implementation prices, which is a barrier for budget-conscious healthcare suppliers.
Whereas it presents options for IoT safety, its core energy lies in conventional IT safety.
5. Symantec
Symantec
Symantec presents numerous safety options to forestall information breaches, together with Symantec Superior Menace Safety (ATP), Symantec Endpoint Safety, and Symantec Hosted Electronic mail Safety.cloud with Messaging Gateway.
ATP permits for centralized investigation and remediation of superior threats throughout endpoints, networks, and e-mail.
Symantec Endpoint Safety leverages world risk intelligence to guard in opposition to recognized and unknown threats on endpoints and digital desktops.
Symantec Hosted Electronic mail Safety. Cloud with Messaging Gateway makes use of risk intelligence and skeptic scanning to safe cloud-based e-mail and block spam and phishing assaults.
It additionally analyzes e-mail content material to forestall information loss and encrypts emails for confidentiality.
Net Safety. Cloud protects customers from malicious downloads and enforces net searching insurance policies.
Why will we advocate it?
It may possibly expose, prioritize, and remediate superior threats throughout endpoints, networks, and e-mail, all from a single console.
Scan for assault artifacts throughout the infrastructure, drill into the main points of an assault, prioritize compromised methods, and rapidly remediate all with a single click on.
Uncover assaults that will in any other case evade detection
Professionals:
Presents a single console to view and handle threats throughout numerous methods (endpoints, community, e-mail).
Permits for faster identification, prioritization, and remediation of threats, probably saving time in comparison with conventional strategies.
p+Offers a mixture of Endpoint Safety, Electronic mail Safety, and Net Safety, providing a layered protection in opposition to numerous assault vectors.
Electronic mail Safety features like Coverage-Based mostly Encryption and Picture Management can assist stop delicate healthcare information from leaking.
Cons:
Whereas providing a centralized view, managing safety throughout a number of methods will be advanced for smaller IT groups.
6. Pattern Micro
Pattern Micro presents safety options for healthcare organizations dealing with growing cyber threats.
Their Community Defence options make the most of superior malware detection, community exercise monitoring, and sandbox evaluation to uncover and cease focused assaults on Digital Protected Well being Info (ePHI).
As healthcare organizations transfer information to the cloud, it offers safety options for hybrid cloud environments.
The Person Safety options supply multi-layered safety for numerous endpoints, cellular units, and Web of Issues (IoT) units, whereas integrating Information Loss Prevention (DLP) to forestall unauthorized information exfiltration.
In addition they supply supplementary safety options for healthcare organizations utilizing Workplace 365 within the cloud.
Why will we advocate it?
Helps healthcare organizations handle challenges confronted in defending affected person information and complying with laws.
Retains affected person information secure.
Meets compliance wants.
It’s hassle-free for smaller organizations.
Professionals:
Protects in opposition to numerous cyber threats, together with ransomware
Presents layered safety with superior safety methods
Manages safety regionally, remotely, or each
Designed for the longer term and simple to combine throughout enterprise methods
Cons:
It’s not very best for small companies within the healthcare business, because it requires particular person licenses for every system needing safety.
It scored low in offline detection exams, a priority for the healthcare business, the place some units could not at all times be linked to the web.
7. Imprivata
Imprivata
A digital identification system can considerably enhance healthcare organizations by streamlining workflows and enhancing safety.
It may possibly obtain this by using sturdy authentication strategies to eradicate handbook logins for cellular entry (decreasing 90% of steps).
The system can routinely detect unauthorized entry to affected person information, stopping 99% of incidents.
Improves affected person privateness and regulatory compliance by safeguarding delicate data all through the care cycle.
Automated identification administration simplifies entry management for clinicians, permitting them to deal with affected person care.
General, a digital identification system optimizes Digital Affected person File (EPR) utilization, manages third-party entry dangers, and improves scientific workflow effectivity.
Why will we advocate it?
Streamlines scientific workflows, permitting for sooner and extra environment friendly care.
Secures essential infrastructure, defending affected person information from cyberattacks.
Protects affected person privateness by making certain solely licensed personnel have entry to medical information.
Reduces handbook authentication steps, saving clinicians time and decreasing errors.
Mechanically identifies unauthorized entry to affected person well being data (PHI).
It may be tailor-made to satisfy the particular wants of recent identification and entry administration in healthcare.
Professionals:
Reduces handbook authentication steps for cellular workflows, liberating up clinician time.
Mechanically identifies unauthorized entry to affected person information.
Simplifies audit recordkeeping and reporting for regulatory necessities.
Automates granting, revoking, and monitoring entry to healthcare methods.
Cons:
Establishing will be advanced and requires help from IT.
Battle with present software program that has an auto login characteristic, inflicting inconvenience.
It doesn’t routinely log off customers after they stroll away from the pc, which is usually a safety concern for some customers.
Restricted customization choices might not be appropriate for organizations that want a extremely personalized resolution.
The reporting performance in Imprivata’s Admin Console could also be restricted.
8. CyberArk
CyberArk
CyberArk presents healthcare organizations a complete identification Safety Platform that protects electronically protected well being data (ePHI) and prevents ransomware assaults.
Their platform secures privileged entry and person identities throughout advanced care supply networks, together with digital care and affected person portals.
It helps healthcare organizations adjust to laws like HIPAA and ISO/IEC 27002 by decreasing the burden on IT workers and enabling safe entry to enterprise purposes for each human and machine identities.
The privileged entry administration resolution helps stop the lateral motion of ransomware and isolate compromised credentials.
We additionally supply buyer and workforce identification options that leverage AI to safe entry, present a passwordless expertise and safe DevOps environments with out impacting agility.
Why will we advocate it?
Trade’s most full Identification Safety Platform.
Presents privileged stable entry and identification safety.
Protects in opposition to threats throughout advanced built-in care supply networks.
Assist healthcare organizations meet compliance necessities.
Safe affected person confidentiality.
Professionals:
It stops ransomware and different threats with privileged entry safety and prevents lateral motion throughout the community.
Ensures adherence to laws like HIPAA with documented and auditable entry controls.
Reduces the burden on IT and workers by simplifying safety options.
Secures entry to enterprise purposes for each human and machine customers.
Cons:
It might be costly for smaller healthcare organizations.
9. Zscaler
Zscaler
The healthcare business suffers essentially the most from information breaches, with a mean value of $10.1 million per incident.
Zero Belief Structure (ZTA) can mitigate this threat by implementing entry management and implementing a number of layers of risk prevention.
ZTA makes use of entry management to restrict entry to externally managed purposes and web locations primarily based on person roles.
Menace prevention consists of superior risk safety, which delivers real-time safety from malicious content material, and day by day safety updates to the Zscaler cloud to make sure complete risk blockage.
Why will we advocate it?
It presents a Zero-Belief Structure (ZTA) compliant with HIPAA laws, which can assist scale back the chance of cyberattacks by limiting entry to information and purposes solely to licensed customers.
It encrypts information at relaxation and in transit, which can assist shield delicate healthcare data.
Inspects visitors for malware and different threats, which can assist stop information breaches.
Offers cloud-based safety, eliminating the necessity for on-premises safety infrastructure and saving money and time.
Simple to deploy and handle, which can assist scale back IT prices
Professionals:
Enforces entry management to affected person information
Offers a number of layers of risk safety
Actual-time safety from malicious Web content material
Every day updates to Zscaler cloud to guard customers
Cons:
It depends on cloud safety, which might not be mature in all healthcare organizations
10. CrowdStrike
CrowdStrike
CrowdStrike presents a cloud-native safety platform (Falcon) to handle the rising cyber threats in healthcare.
Falcon protects endpoints (desktops, laptops, servers, and so forth.) on any community and makes use of risk intelligence to proactively detect and reply to assaults, permitting healthcare organizations to transition to distant workforces and telemedicine securely.
It consolidates safety features throughout numerous units and platforms (Home windows, Linux, Macs, and so forth.), probably decreasing IT safety prices by 30%.
Moreover, CrowdStrike Falcon Full presents managed safety operations (24/7) and risk searching to establish and cease subtle assaults.
Falcon Uncover presents complete visibility and sturdy safety for Web of Medical Issues (IoMT) units.
Why will we advocate it?
Protects in opposition to numerous cyber threats with an AI-native cybersecurity platform.
Designed to be simple to make use of and deploy.
Reduces IT safety prices by 30%.
Protects endpoints from any location.
Offers visibility throughout numerous units.
Presents MDR (Managed Detection and Response) for steady risk monitoring.
Professionals:
Simple and fast deployment
Unified visibility throughout numerous units and platforms
Superior endpoint safety with risk detection and prevention
Managed safety operations and threat-hunting
Unmatched visibility for Web of Medical Issues (IoMT) units
Cons:
Requires expert workers to interpret outcomes
Conclusion
In 2026’s fast-evolving healthcare cybersecurity panorama, selecting the optimum community safety resolution is important to guard delicate affected person information and meet rigorous laws like HIPAA.
Perimeter 81 stands out because the premier possibility for healthcare organizations demanding sturdy, intuitive, and all-encompassing community protection.