A complicated malware marketing campaign has emerged that leverages faux on-line pace take a look at purposes to deploy obfuscated JavaScript payloads on Home windows techniques.
These malicious utilities masquerade as legit community pace testing instruments, guide readers, PDF utilities, and numerous search frontends to deceive unsuspecting customers into putting in harmful code that operates covertly within the background.
The assault begins when customers obtain what seems to be a practical pace testing software from compromised or malicious domains equivalent to onlinespeedtestservice[.]com.
Upon set up, the applying delivers its marketed performance, making a false sense of safety whereas concurrently deploying a hidden Node.js runtime surroundings alongside closely obfuscated JavaScript recordsdata.
The seen executable performs as anticipated, sustaining the person’s belief whereas the malicious elements set up themselves inside the system.
Safety Magic analysts recognized that these purposes are packaged utilizing Inno-Packer installers, which bundle legit performance with malicious elements together with a conveyable Node runtime, scheduled activity configurations, and obfuscated JavaScript payloads that serve no objective for the applying’s major perform.
The malware operates independently from the primary executable, considerably increasing the assault floor and offering menace actors with persistent entry to compromised techniques.
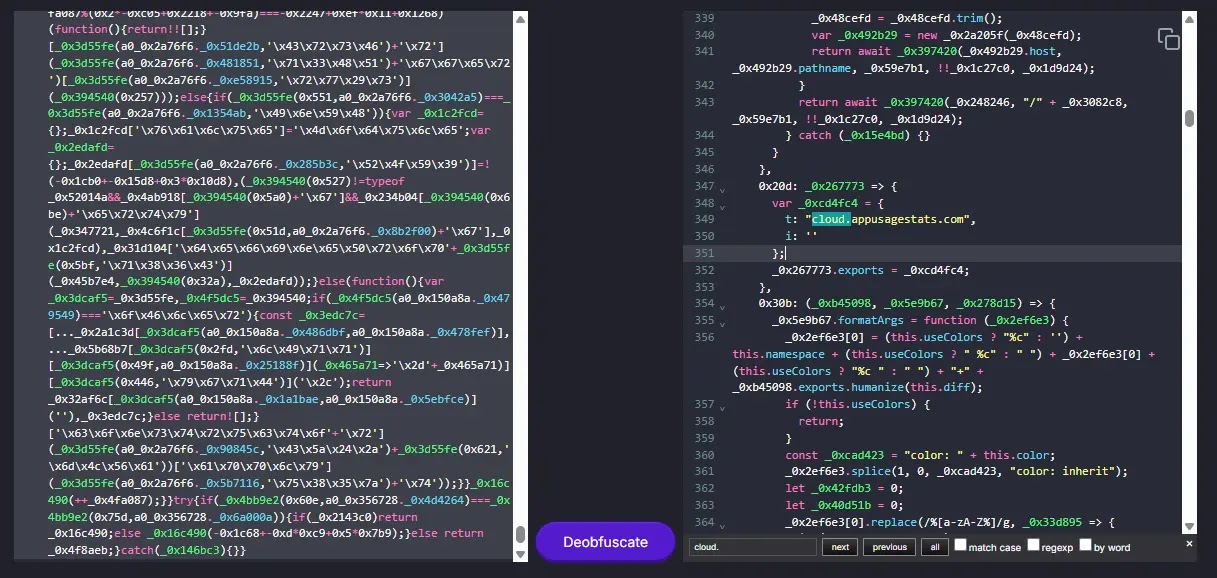
Obfuscated JS (Supply – Safety Magic)
The an infection establishes persistence by scheduled duties that execute the malicious JavaScript payload roughly each 12 hours.
This JavaScript element maintains encrypted communications with command and management servers, particularly cloud.appusagestats.com, and possesses the aptitude to execute arbitrary code delivered by distant servers.
The malware queries system data together with the Home windows registry key HKLMSoftwareMicrosoftCryptographyMachineGuid to assemble machine identification knowledge for transmission to attackers.
Superior Obfuscation and Command Execution Mechanisms
The JavaScript payload employs subtle obfuscation strategies that conceal its true objective from safety evaluation.
Researchers found that the obfuscated code accommodates encoded strings that may be decoded by patching the return assertion of the decode perform.
When decoded, the JavaScript reveals its communication protocol with the command and management infrastructure. The malware transmits JSON-formatted knowledge containing model data, system identifiers, and functionality flags.
Evaluation of community communications reveals the payload can obtain and execute PowerShell instructions, with researchers observing take a look at executions that displayed message packing containers by Home windows Kinds assemblies.
The command execution mechanism makes use of Node.js child_process modules to spawn system processes, enabling arbitrary code execution with person privileges whereas sustaining stealth by hidden window modes and no-profile PowerShell executions.
Observe us on Google Information, LinkedIn, and X to Get Extra On the spot Updates, Set CSN as a Most well-liked Supply in Google.