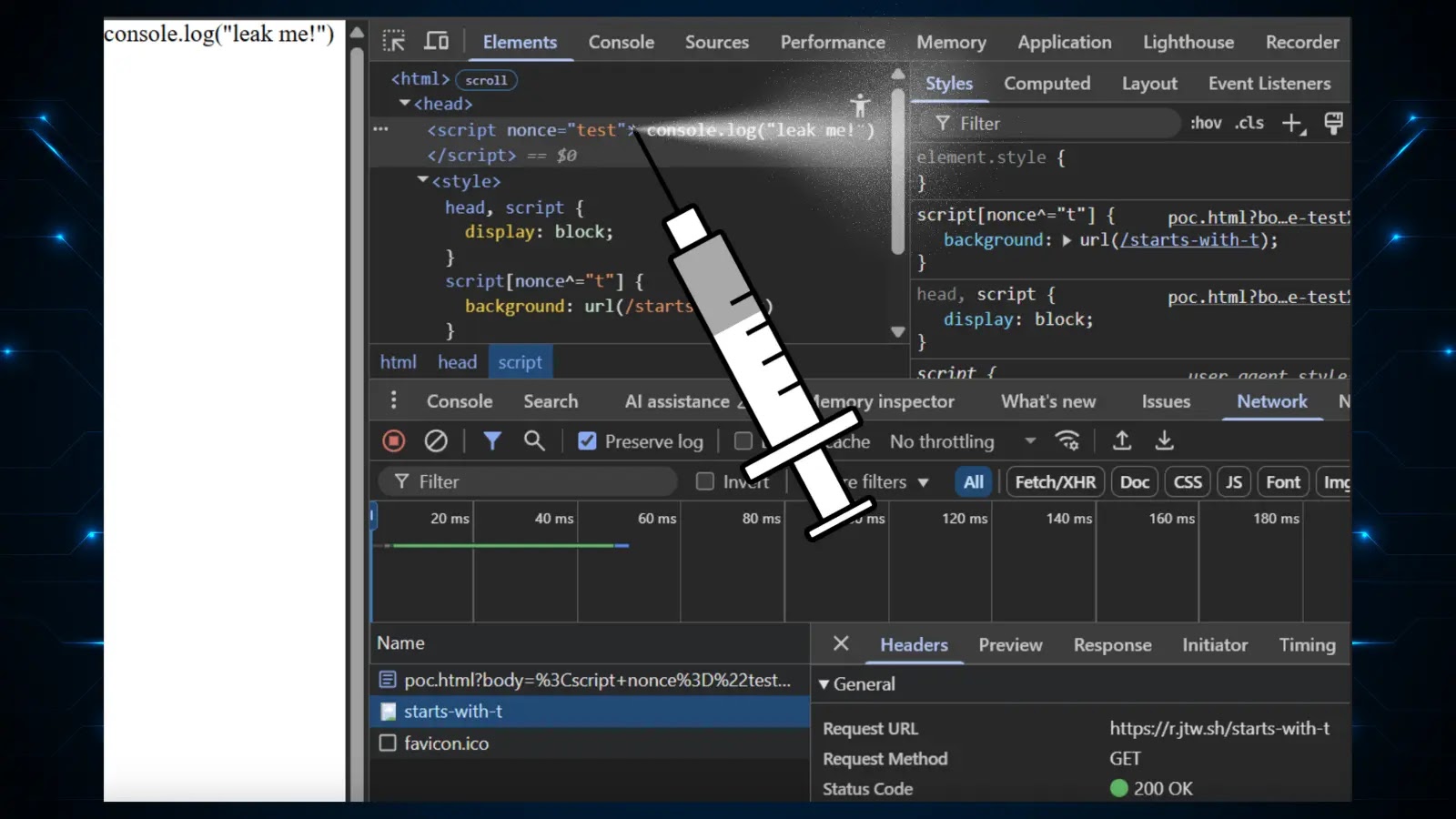
A important vulnerability in Microsoft’s BitLocker full disk encryption, demonstrating that it may be bypassed in beneath 5 minutes utilizing a software-only assault dubbed “Bitpixie” (CVE-2023-21563).
A public proof-of-concept (PoC) exploit has now been launched, highlighting the severity of the danger to tens of millions of Home windows gadgets counting on BitLocker with out pre-boot authentication.
How the Bitpixie Assault Works
Not like conventional hardware-based assaults, which require bodily tampering, soldering, or specialised tools, the Bitpixie vulnerability permits attackers to extract BitLocker’s Quantity Grasp Key (VMK) completely by way of software program.
This non-invasive methodology leaves no everlasting hint and doesn’t require a whole disk picture, making it significantly engaging for crimson teamers and adversaries concentrating on stolen or unattended laptops.
The vulnerability stems from a flaw within the Home windows bootloader’s dealing with of the PXE comfortable reboot course of. When a boot fails and the system makes an attempt a community restoration, the bootloader fails to clear the VMK from reminiscence. By exploiting this oversight, attackers can entry the VMK and decrypt the protected disk.
Two Assault Paths: Linux and Home windows PE Editions
Researchers have demonstrated two important exploitation methods:
Linux-Primarily based Assault (Bitpixie Linux Version):
Enter Home windows Restoration Atmosphere through Shift+Reboot.PXE boot right into a weak model of the Home windows Boot Supervisor.
Manipulate Boot Configuration Knowledge (BCD) to set off a PXE comfortable reboot.
Chain-load a signed Linux shim, GRUB, and Linux kernel.
Use a kernel module to scan bodily reminiscence for the VMK.
Mount the encrypted quantity with the extracted VMK utilizing the dislocker FUSE driver.
This methodology works so long as the gadget doesn’t require pre-boot authentication (comparable to a PIN or USB key).
Home windows PE-Primarily based Assault (Bitpixie WinPE Version):
For methods that block third-party signed elements (e.g., secured-core PCs), attackers can use solely Microsoft-signed elements.PXE boot into Home windows Boot Supervisor once more with a modified BCD.
Load a WinPE picture containing winload.efi, ntoskrnl.exe, and different signed Microsoft elements.
Use a custom-made model of WinPmem to scan reminiscence for the VMK.
Extract the restoration password from BitLocker metadata and unlock the quantity.
This method is relevant to any gadget trusting the Microsoft Home windows Manufacturing PCA 2011 certificates.
The general public PoC launched by researchers automates these assault chains, permitting for fast compromise-often in lower than 5 minutes. The assault’s pace and non-invasive nature make it a big danger, particularly in situations involving misplaced or stolen laptops protected solely by TPM-based BitLocker with out extra authentication.
The first mitigation in opposition to Bitpixie and related assaults is to implement pre-boot authentication, which requires a PIN, USB key, or key file earlier than the system boots. This extra layer prevents attackers from accessing the VMK, even when they will manipulate the boot course of.
“The Bitpixie vulnerability – and extra usually each {hardware} and software-based assaults – could be mitigated by forcing pre-boot authentication,” researchers emphasize.
Organizations relying solely on TPM-based BitLocker safety are urged to evaluate their safety posture instantly and deploy pre-boot authentication to safeguard delicate knowledge.
The Bitpixie vulnerability exposes a high-risk assault path in opposition to BitLocker encryption, with a working proof-of-concept now out there. This growth underscores the necessity for sturdy authentication measures and highlights the risks of counting on default configurations for disk encryption.
Vulnerability Assault Simulation on How Hackers Quickly Probe Web sites for Entry Factors – Free Webinar