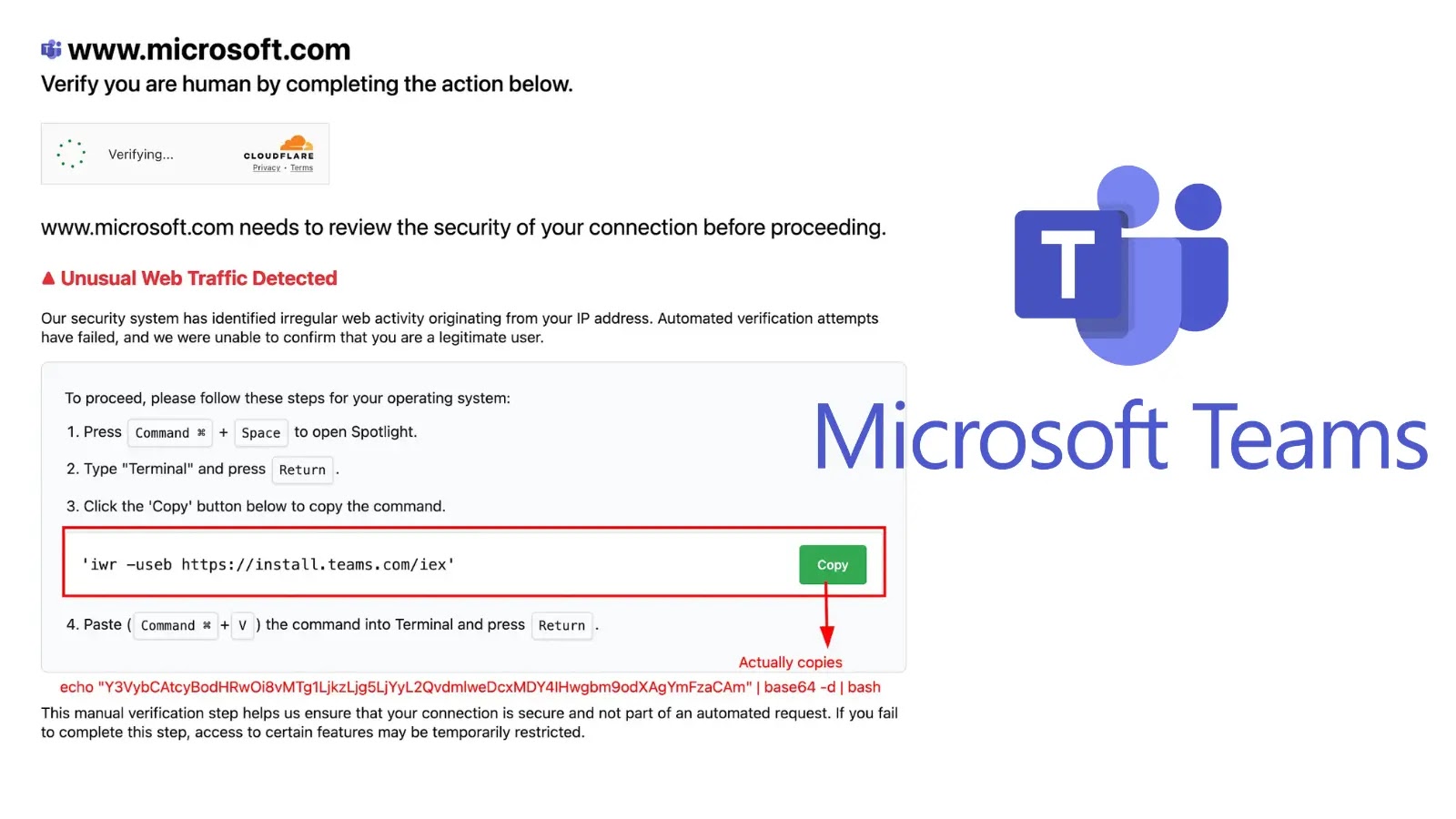
Microsoft has confirmed that Chinese language state-sponsored menace actors are actively exploiting crucial zero-day vulnerabilities in on-premises SharePoint servers, prompting pressing safety warnings for organizations worldwide.
The tech large’s Safety Response Heart reported coordinated assaults focusing on internet-facing SharePoint installations utilizing newly disclosed vulnerabilities that allow authentication bypass and distant code execution.
Key Takeaways1. CVE-2025-53770/53771 in on-premises SharePoint permits authentication bypass and RCE.2. Assaults are pushed by Chinese language state-sponsored teams.3. Set up Microsoft patches (KB5002768/2754/2760).
SharePoint Zero-Day Exploited in Energetic Assaults
The exploitation marketing campaign facilities round CVE-2025-53770, a complete vulnerability that mixes authentication bypass and distant code execution capabilities, alongside CVE-2025-53771, which addresses safety bypass points associated to the beforehand disclosed CVE-2025-49706.
These vulnerabilities particularly goal on-premises SharePoint Server installations, together with SharePoint Server 2016, 2019, and SharePoint Subscription Version, whereas SharePoint On-line in Microsoft 365 stays unaffected.
Microsoft safety researchers have noticed menace actors conducting reconnaissance by way of crafted POST requests to the ToolPane endpoint, adopted by profitable deployment of malicious net shells named spinstall0.aspx and variants corresponding to spinstall.aspx, spinstall1.aspx, and spinstall2.aspx.
The attackers make the most of these net shells to extract crucial ASP.NET MachineKey knowledge, enabling persistent entry to compromised techniques and potential lateral motion inside goal networks.
Three distinct Chinese language menace teams have been recognized as main exploiters of those vulnerabilities. Linen Hurricane, lively since 2012, has targeted on mental property theft focusing on authorities, protection, and human rights organizations.
Violet Hurricane, operational since 2015, focuses on espionage in opposition to former authorities personnel, NGOs, and academic establishments throughout america, Europe, and East Asia.
Moreover, Microsoft tracks Storm-2603, a China-based actor with medium confidence evaluation, famous for deploying Warlock and Lockbit ransomware in earlier campaigns.
The exploitation makes an attempt started as early as July 7, 2025, with menace actors leveraging these vulnerabilities for preliminary entry earlier than deploying PowerShell-based payloads and establishing persistence mechanisms.
CVETitleCVSS 3.1 ScoreSeverityCVE-2025-53770SharePoint ToolShell Auth Bypass and RCE9.8CriticalCVE-2025-53771SharePoint ToolShell Path Traversal6.5Medium
Mitigations
Microsoft has launched crucial safety updates for all supported SharePoint variations, together with KB5002768 for SharePoint Server Subscription Version, KB5002754 and KB5002753 for SharePoint 2019, and KB5002760 and KB5002759 for SharePoint 2016.
Organizations should instantly apply these patches whereas implementing further protecting measures.
Important mitigation steps embrace enabling Antimalware Scan Interface (AMSI) in Full Mode, deploying Microsoft Defender Antivirus on all SharePoint servers, and rotating ASP.NET machine keys adopted by Web Info Companies (IIS) restart.
Microsoft strongly recommends deploying Microsoft Defender for Endpoint or equal options to detect post-exploitation actions and contemplating short-term disconnection from web entry for unpatched techniques till safety updates will be utilized.
Increase detection, scale back alert fatigue, speed up response; all with an interactive sandbox constructed for safety groups -> Strive ANY.RUN Now