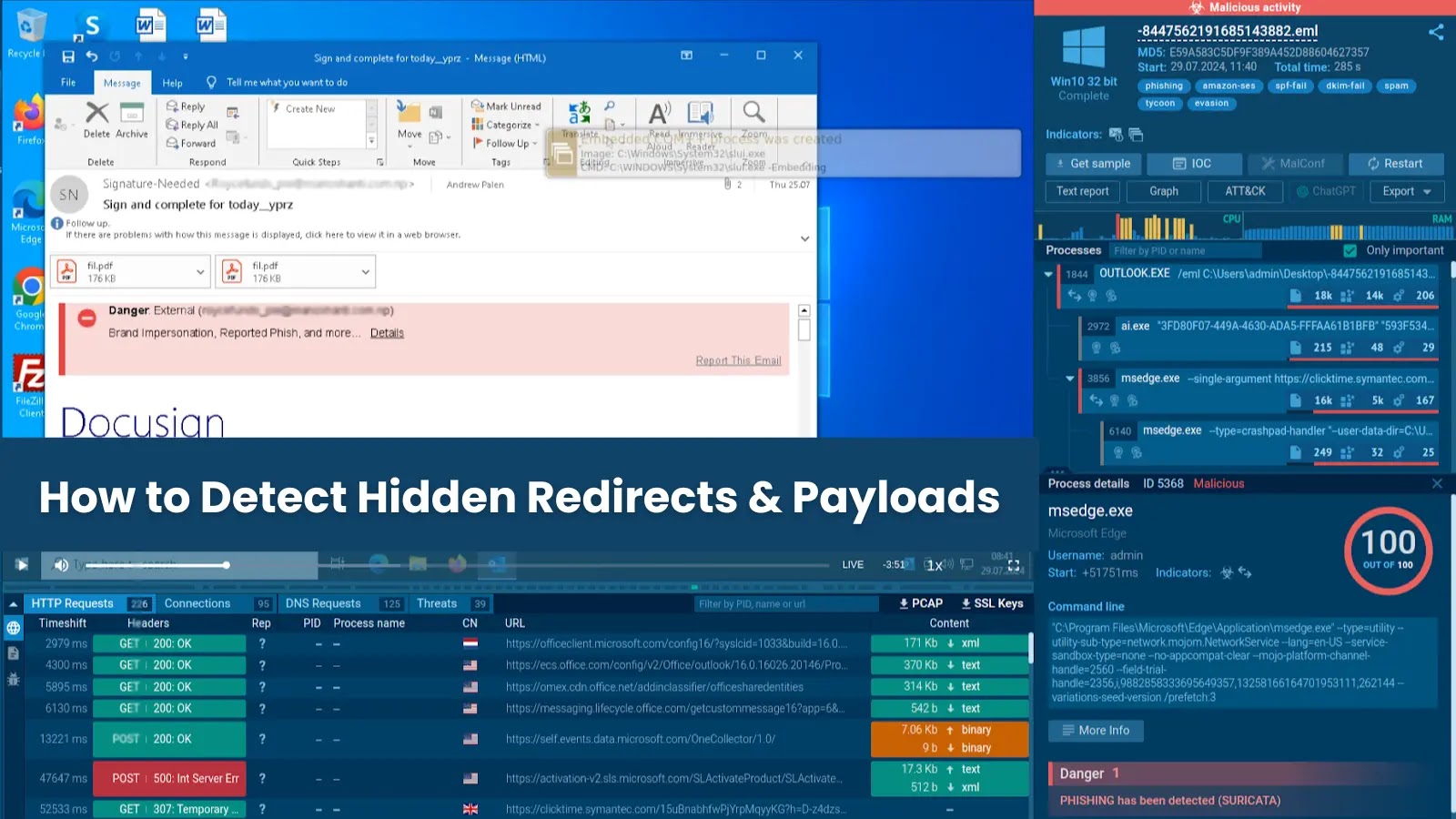
A complicated China-nexus risk actor designated MURKY PANDA has emerged as a big cybersecurity concern, conducting intensive cyberespionage operations towards authorities, know-how, educational, authorized, {and professional} companies entities throughout North America since late 2024.
This superior persistent risk group demonstrates distinctive capabilities in cloud atmosphere exploitation and trusted-relationship compromises, marking a regarding evolution in state-sponsored cyber actions.
The adversary has established itself as a formidable drive by its capability to quickly weaponize each n-day and zero-day vulnerabilities, regularly attaining preliminary entry by exploiting internet-facing home equipment.
MURKY PANDA’s operations are characterised by their concentrate on intelligence assortment goals, with documented instances of electronic mail exfiltration and delicate doc theft from high-profile targets.
CrowdStrike researchers recognized MURKY PANDA’s exercise as notably notable for its cloud-conscious method and superior operational safety measures.
The risk group’s refined tradecraft contains modifying timestamps and systematically deleting indicators of compromise to evade detection and complicate attribution efforts.
Their operations align with broader China-nexus focused intrusion actions tracked by trade sources as Silk Storm.
The group’s arsenal contains deployment of net shells corresponding to Neo-reGeorg, generally utilized by Chinese language adversaries, and entry to a low-prevalence customized malware household designated CloudedHope.
Moreover, MURKY PANDA has demonstrated proficiency in leveraging compromised small workplace/house workplace units as operational infrastructure, mirroring ways employed by different Chinese language risk actors like VANGUARD PANDA.
Trusted-Relationship Cloud Exploitation Strategies
MURKY PANDA’s most distinctive functionality lies in conducting trusted-relationship compromises inside cloud environments, representing a comparatively uncommon and undermonitored assault vector.
The group has efficiently exploited zero-day vulnerabilities to compromise software-as-a-service suppliers, subsequently leveraging their entry to maneuver laterally to downstream prospects.
In documented instances, the adversary obtained utility registration secrets and techniques from compromised SaaS suppliers utilizing Entra ID for buyer entry administration.
By authenticating as service principals, MURKY PANDA gained unauthorized entry to downstream buyer environments, enabling electronic mail entry and information exfiltration.
This refined approach demonstrates their deep understanding of cloud structure and identification administration methods.
The risk actor has additionally focused Microsoft cloud answer suppliers, exploiting delegated administrative privileges to realize World Administrator entry throughout a number of downstream buyer tenants, establishing persistent backdoors by newly created person accounts and modified service principal configurations.
Enhance your SOC and assist your workforce defend your small business with free top-notch risk intelligence: Request TI Lookup Premium Trial.