Cloud Software program Group has disclosed a number of high-severity vulnerabilities in NetScaler ADC (previously Citrix ADC) and NetScaler Gateway (previously Citrix Gateway) that may result in distant code execution (RCE) and denial of service (DoS).
Exploitation of CVE-2025-7775 has been noticed within the wild towards unmitigated home equipment, and prospects are urged to improve instantly.
Affected variations embody NetScaler ADC and NetScaler Gateway 14.1 earlier than 14.1-47.48 and 13.1 earlier than 13.1-59.22, plus NetScaler ADC 13.1-FIPS/NDcPP earlier than 13.1-37.241 and 12.1-FIPS/NDcPP earlier than 12.1-55.330.
Safe Personal Entry on-prem and SPA Hybrid deployments that use NetScaler cases are additionally affected and require the identical NetScaler upgrades. Observe that NetScaler ADC/Gateway 12.1 and 13.0 mainstream branches are Finish of Life and not supported; prospects ought to transfer to supported builds that remediate these flaws.
CVE-2025-7775 Underneath Lively Assault
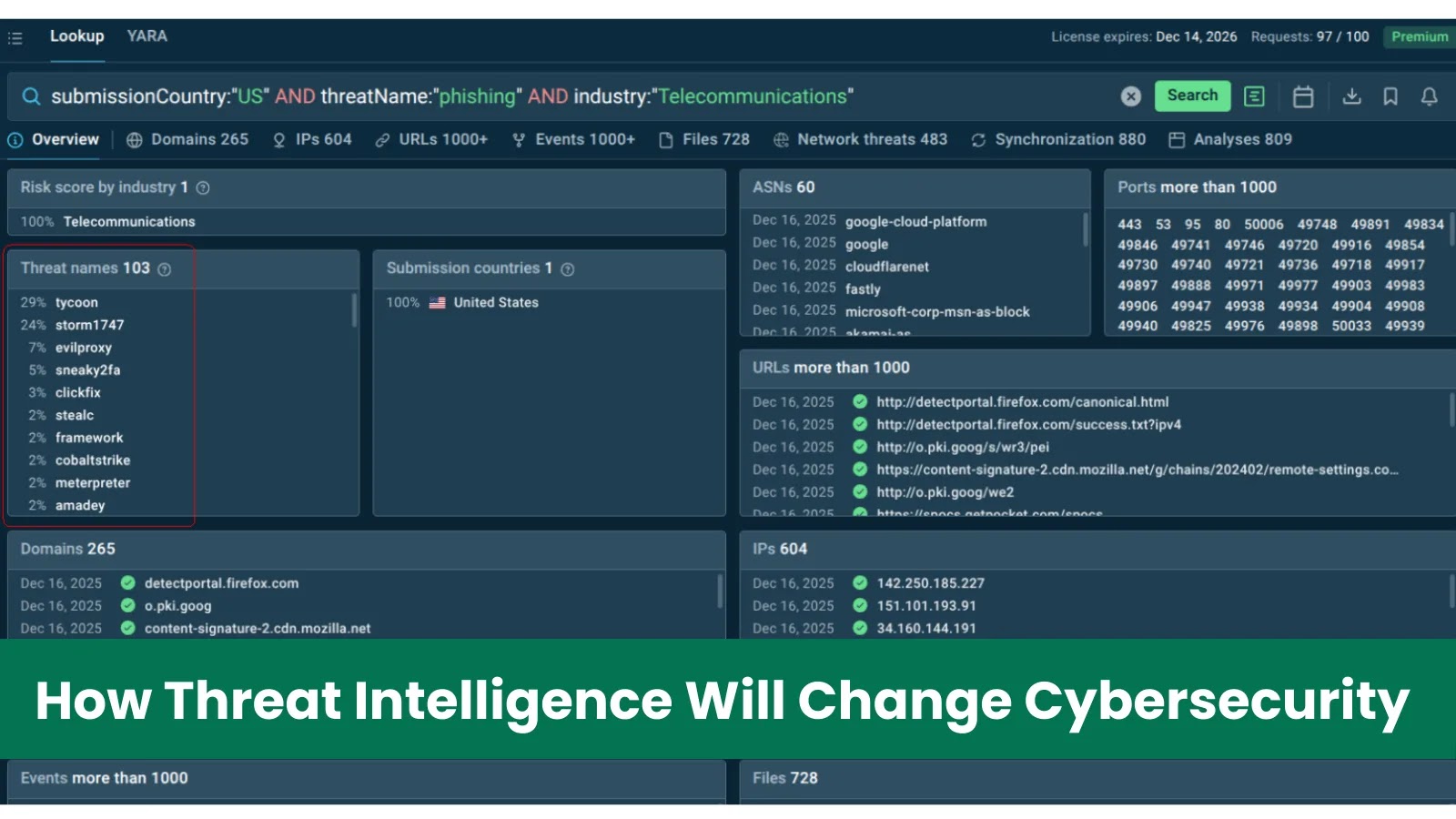
Three CVEs have been revealed with CVSS v4.0 base scores between 8.7 and 9.2. CVE-2025-7775 (CVSS 9.2) is a reminiscence overflow that may allow RCE and/or DoS.
It’s triggerable when the equipment is configured as a Gateway (VPN digital server, ICA Proxy, CVPN, RDP Proxy) or an AAA digital server, or when load balancing digital servers of kind HTTP/SSL/HTTP_QUIC are certain to IPv6 providers/service teams (together with DNS-based service decision to IPv6), or when a content material routing (CR) digital server is configured with kind HDX.
CVE-2025-7776 (CVSS 8.8) is one other reminiscence overflow that may trigger unpredictable habits and DoS when a Gateway (VPN vserver) has a PCoIP profile certain.
CVE-2025-8424 (CVSS 8.7) is an improper entry management problem on the administration interface; exploitation requires entry to NSIP, Cluster Administration IP, native GSLB Web site IP, or a SNIP with administration entry, and is scored with an adjoining community assault vector.
There are not any workarounds. Cloud Software program Group strongly advises upgrading to mounted releases: NetScaler ADC and Gateway 14.1-47.48 or later; 13.1-59.22 or later; NetScaler ADC 13.1-FIPS/13.1-NDcPP 13.1-37.241 or later; and 12.1-FIPS/12.1-NDcPP 12.1-55.330 or later.
SPA prospects ought to improve all NetScaler cases underpinning on-prem or hybrid deployments. The place potential, additionally prohibit administration airplane publicity to devoted admin networks and guarantee entry controls on NSIP/CLIP/SNIP/GSLB IPs are tightly enforced.
Clients can shortly decide publicity by reviewing ns.conf and operating configuration for telltale entries:
For CVE-2025-7775: presence of AAA or Gateway vservers (e.g., “add authentication vserver …”, “add vpn vserver …”); LB vservers of kind HTTP/SSL/HTTP_QUIC certain to IPv6 providers or IPv6 servers (together with DNS AAAA decision); CR vservers of kind HDX.
For CVE-2025-7776: Gateway (VPN vserver) with a PCoIP profile certain (e.g., “-pcoipVserverProfileName …”).
Given lively exploitation of CVE-2025-7775, organizations ought to prioritize patching internet-exposed Gateways and any home equipment with IPv6-enabled LB vservers. Monitor for crashes, surprising restarts, and anomalous management-plane entry, and evaluation logs for suspicious exercise round affected digital servers.
Cloud Software program Group credited Jimi Sebree (Horizon3.ai), Jonathan Hetzer (Schramm & Associate), and François Hämmerli for accountable disclosure.
Discover this Story Fascinating! Comply with us on LinkedIn and X to Get Extra Prompt Updates.