Vital flaw in Citrix NetScaler units echoes notorious 2023 safety breach that crippled main organizations worldwide.
The brand new vital vulnerability in Citrix NetScaler units has safety specialists warning of potential widespread exploitation, drawing alarming parallels to the devastating “CitrixBleed” assaults that plagued organizations in 2023.
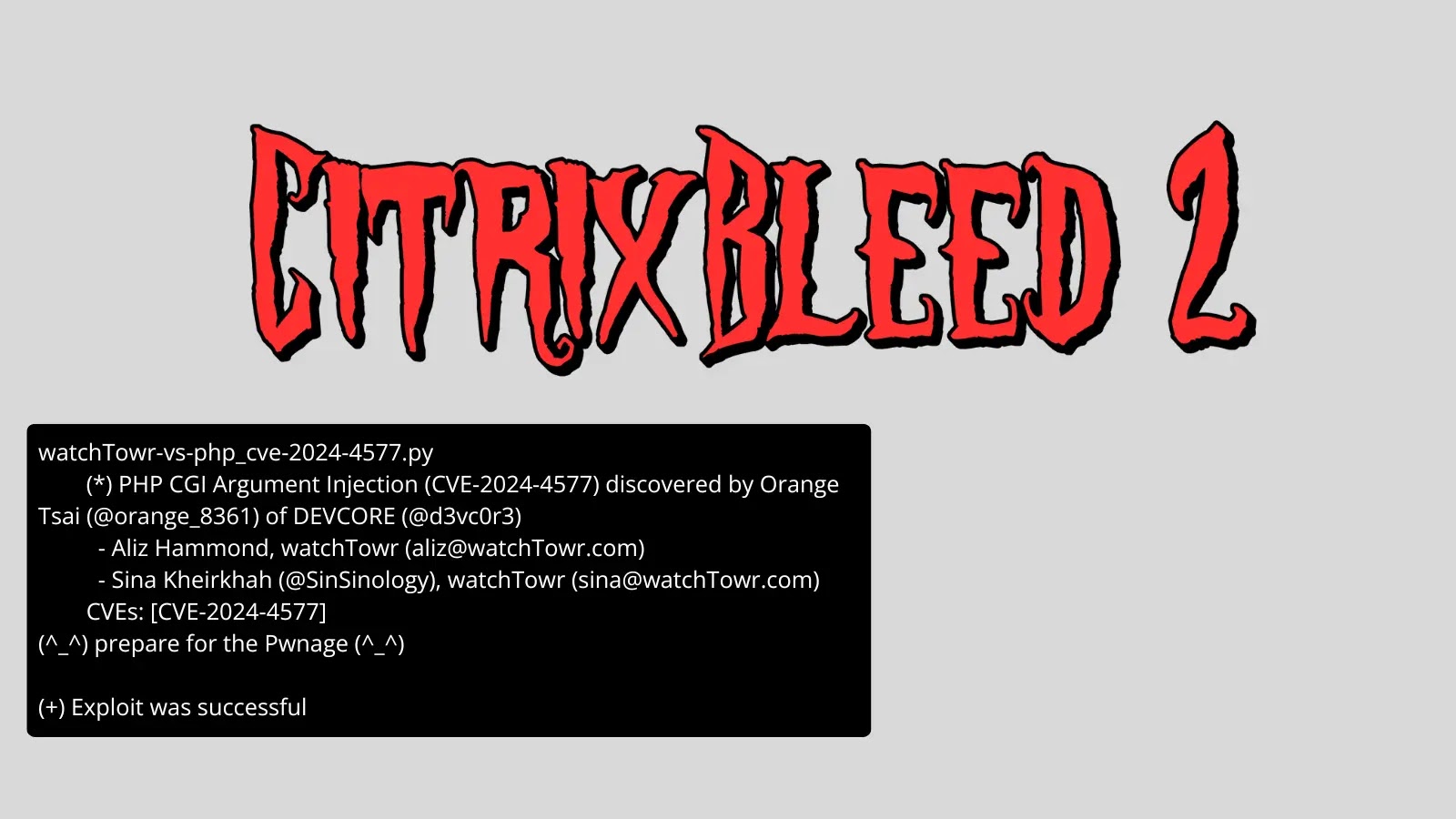
The vulnerability, tracked as CVE-2025-5777 and dubbed “CitrixBleed 2,” permits attackers to steal delicate data instantly from machine reminiscence, probably bypassing multi-factor authentication and hijacking consumer periods.
The vulnerability evaluation disclosed by watchTower Labs researchers exhibits that the reminiscence leak vulnerability impacts NetScaler ADC and NetScaler Gateway units configured as distant entry gateways.
With a vital CVSS severity rating of 9.3, the vulnerability stems from inadequate enter validation that results in reminiscence overread when processing authentication requests.
The unique CitrixBleed vulnerability (CVE-2023-4966) was extensively exploited by ransomware teams and nation-state actors, resulting in high-profile breaches together with assaults on Boeing and Comcast’s Xfinity service that affected 36 million prospects.
Lively Exploitation Suspected
Cybersecurity agency ReliaQuest reported that they’ve noticed “medium confidence” indicators suggesting the vulnerability is already being exploited in focused assaults.
Proof contains hijacked Citrix net periods the place authentication was granted with out consumer data, indicating profitable multi-factor authentication bypass.
The researchers recognized a number of regarding patterns: session reuse throughout suspicious IP addresses, LDAP queries related to Lively Listing reconnaissance, and a number of cases of the ADExplorer64.exe device being deployed throughout compromised environments. Attackers seem like utilizing client VPN companies to masks their actions whereas conducting post-breach reconnaissance.
The watchTower Labs evaluation reveals that the vulnerability’s exploitation is surprisingly easy. By sending a malformed HTTP request to the Citrix Gateway login endpoint with out correct parameter values, attackers can set off a reminiscence leak that exposes uninitialized variables containing delicate information from the machine’s reminiscence.
“What’s taking place below the hood here’s a basic case of C-language mischief,” the researchers defined. “The backend parser finally ends up handing us again an uninitialized native variable” containing no matter information was beforehand saved in reminiscence, probably together with session tokens and different delicate data.
The vulnerability manifests when attackers ship HTTP POST requests to the /p/u/doAuthentication.do endpoint with malformed login parameters. As an alternative of correctly initializing reminiscence variables, the system returns no matter residual information was beforehand saved in reminiscence, making a textbook instance of CWE-457: Use of Uninitialized Variable.
Safety researcher Kevin Beaumont, who coined the “CitrixBleed 2” moniker, famous that over 50,000 probably weak NetScaler cases are uncovered to the web primarily based on Shodan searches. The Shadowserver Basis found over 1,200 home equipment stay unpatched as of late June 2025, regardless of Citrix releasing fixes on June 17.
Citrix has launched safety updates for supported variations and strongly urges organizations to improve instantly.
The corporate recommends terminating all lively ICA and PCoIP periods after patching to stop potential session hijacking. Organizations working end-of-life variations 12.1 and 13.0 should improve to supported variations, as these is not going to obtain safety patches.
Given the extreme influence of the unique CitrixBleed assaults, which continued to be exploited for months after patches had been out there, safety specialists emphasize that organizations can’t afford to delay patching efforts.
The vulnerability’s similarity to its predecessor suggests it’s going to doubtless grow to be a popular device for cybercriminals in search of preliminary entry to enterprise networks.
Examine dwell malware conduct, hint each step of an assault, and make quicker, smarter safety choices -> Strive ANY.RUN now