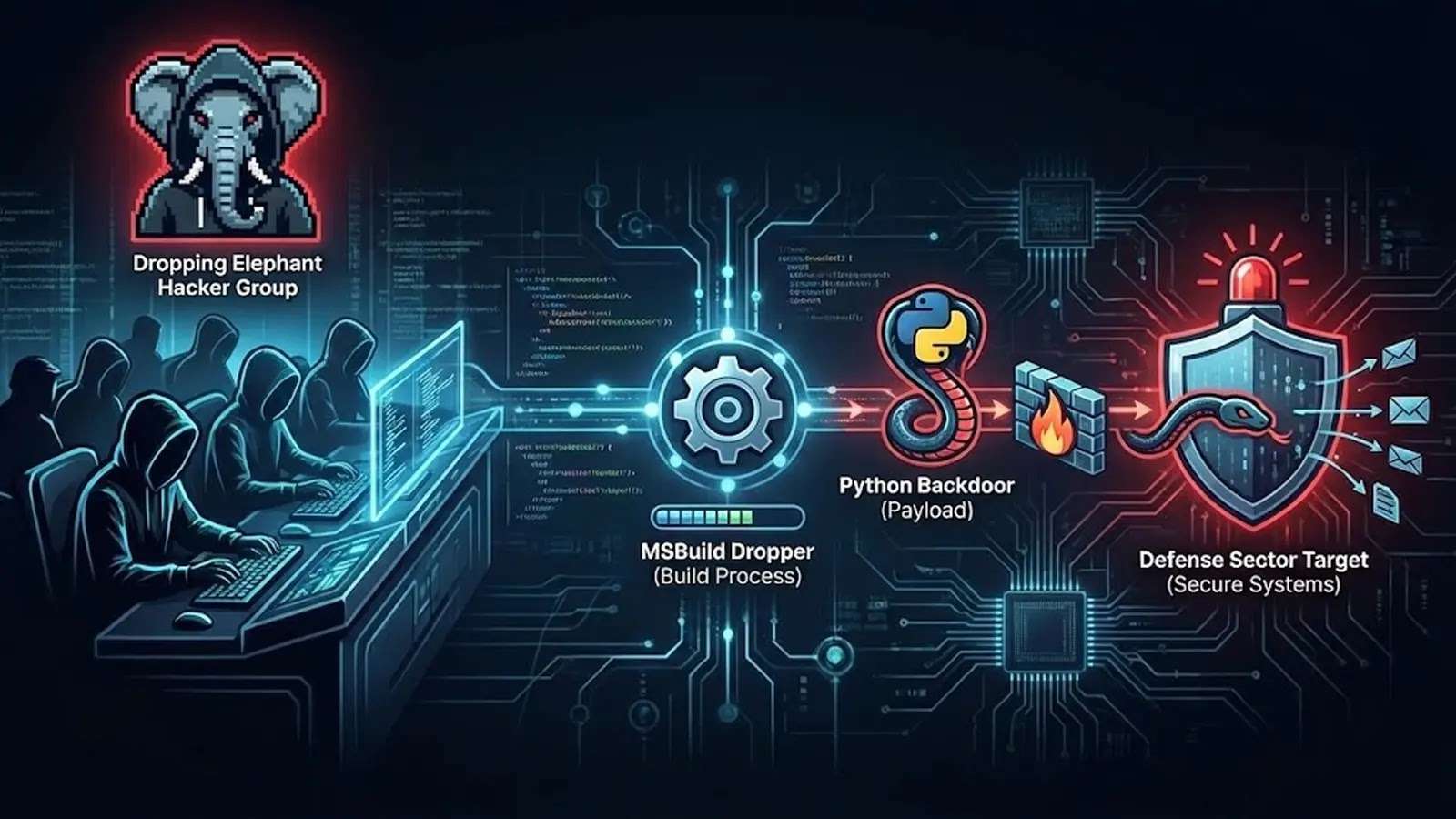
Google launched its August 2025 Android Safety Bulletin on August 4, revealing a important vulnerability that poses vital dangers to Android machine customers worldwide.
Probably the most extreme flaw, designated CVE-2025-48530, impacts the core System part and will allow distant code execution with out requiring any consumer interplay, making it notably harmful for hundreds of thousands of Android units globally.
The vulnerability carries a important severity ranking because of its potential for exploitation together with different safety bugs, requiring no extra execution privileges to compromise affected units.
Key Takeaways1. Important Android flaw allows distant code execution with out consumer interplay.2. All Android units are susceptible till up to date to safety patch degree 2025-08-05 or later.3. Set up the August 2025 safety patch instantly when accessible from the machine producer.
This represents one of the severe Android safety threats recognized in latest months, as attackers might doubtlessly achieve management of units with out victims being conscious of any malicious exercise.
Android System RCE Vulnerability
The vulnerability targets Android’s System part explicitly, which handles elementary machine operations and safety features.
Google’s inner monitoring system signifies the problem was recognized by way of inner safety analysis and testing processes.
The Distant Code Execution (RCE) classification means profitable exploitation might enable attackers to run arbitrary code with system-level privileges.
Android companions obtained notification of this important flaw a minimum of one month previous to public disclosure, following Google’s accountable disclosure timeline.
Gadgets with safety patch degree 2025-08-05 or later shall be protected towards this vulnerability and different points recognized within the bulletin.
CategoryDetailsAffected ProductsAndroid System part (all Android variations previous to patch degree 2025-08-05)ImpactRemote Code Execution (RCE) Exploit PrerequisitesNo consumer interplay required; may be exploited together with different bugsCVSS 3.1 ScoreNot accessible
Google plans to launch supply code patches to the Android Open Supply Venture (AOSP) repository inside 48 hours of the bulletin’s publication.
Regardless of the severity of CVE-2025-48530, Android’s built-in safety structure gives a number of layers of safety that considerably scale back exploitation dangers.
Google Play Shield, enabled by default on units with Google Cellular Providers, actively displays for malicious purposes and potential safety threats.
The Android safety platform incorporates numerous enhancements in newer variations that make vulnerability exploitation significantly more difficult.
Google’s safety staff repeatedly displays for abuse patterns and warns customers about doubtlessly dangerous purposes by way of automated detection techniques.
These mitigations work at the side of platform-level protections to create a complete safety framework, although customers are strongly inspired to put in the August 2025 safety patch instantly upon availability from their machine producers.
Combine ANY.RUN TI Lookup together with your SIEM or SOAR To Analyses Superior Threats -> Strive 50 Free Trial Searches