A important distant code execution (RCE) vulnerability tracked as CVE-2025-11953 within the @react-native-community/cli NPM package deal.
With almost 2 million weekly downloads, this package deal powers the command-line interface for React Native, a JavaScript framework beloved by builders constructing cross-platform cell apps.
The vulnerability, scored at CVSS 9.8 for its community accessibility, low complexity, and potential for high-impact injury, lets unauthenticated attackers execute arbitrary working system instructions on a developer’s machine through the package deal’s improvement server.
React Native’s CLI, extracted from the core codebase years in the past for higher maintainability, handles important duties like initializing tasks and working the Metro bundler.
Instructions equivalent to “npm begin” or “npx react-native run-android” launch this server, which bundles JavaScript for emulators or units.
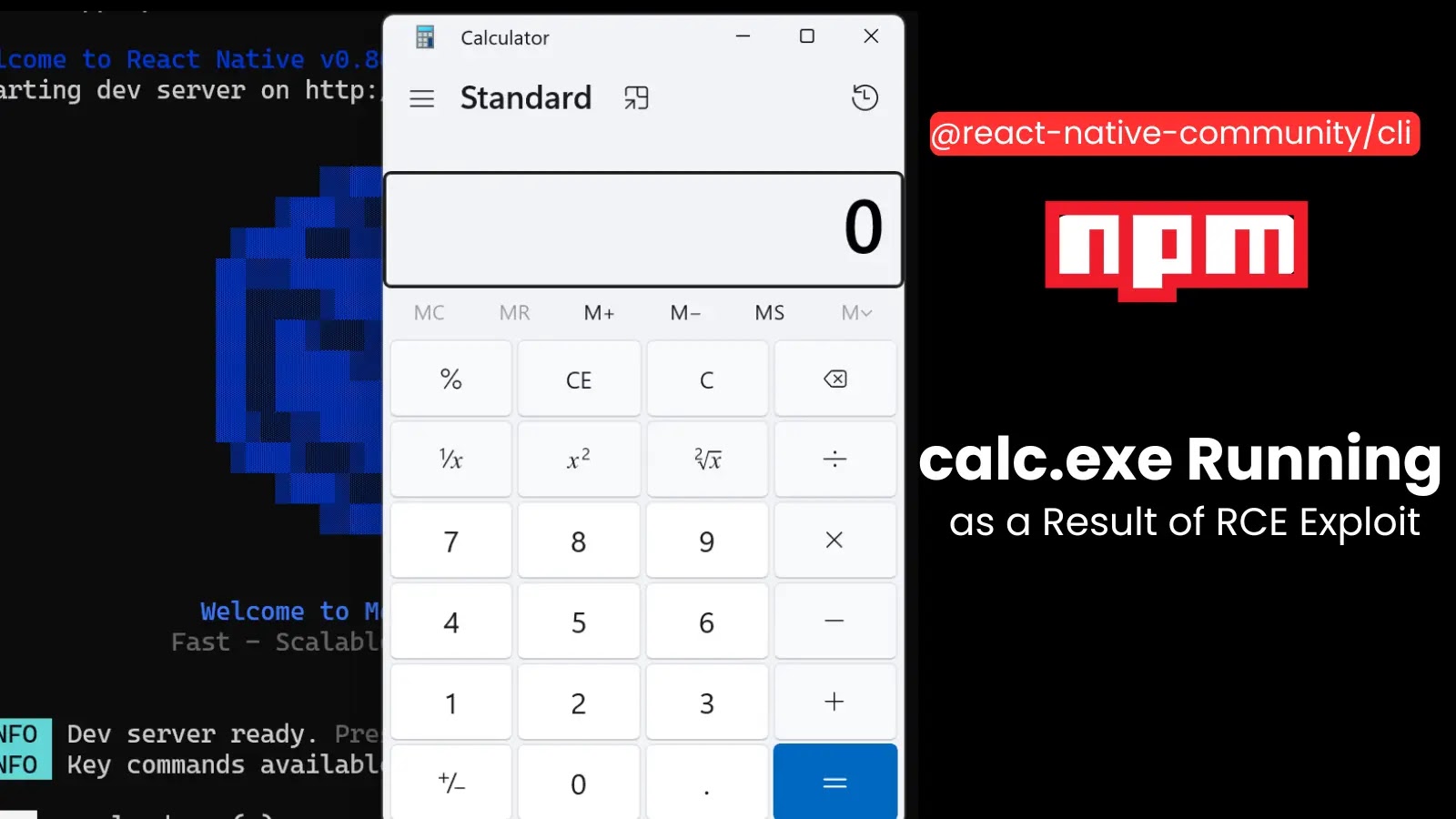
However JFrog researchers discovered that the server’s /open-url endpoint mishandles consumer enter, passing it on to the “open” NPM library’s unsafe open() operate.
On Home windows, this spawns shell instructions with full parameter management, assume launching calc.exe or writing information like a proof-of-concept “pwned.txt.” On macOS and Linux, execution is extra restricted however might escalate with additional tweaks to URI schemes or file handlers.
What elevates this from a neighborhood nuisance to a nightmare is a secondary challenge in React Native’s core: the Metro server binds to all community interfaces (0.0.0.0) by default, regardless of console messages claiming localhost-only entry.
This stems from an undefined host parameter within the runServer operate, exposing endpoints to distant attackers. Builders utilizing weak CLI variations (4.8.0 to twenty.0.0-alpha.2) within the @react-native-community/cli-server-api package deal are in danger, particularly these skipping frameworks like Expo, which use various servers.
Not everybody faces the identical degree of threat. Initiatives that use Metro for decent reloading throughout improvement, typically seen in fundamental React Native setups for Home windows, macOS, iOS, or Android, typically tackle extra challenges.
International installations or bundled dependencies amplify the menace. JFrog demonstrated Home windows exploits simply, whereas Unix-like methods demand artistic workarounds, equivalent to exploiting URI handlers for distant file execution.
The repair arrived swiftly, because of Meta’s safety workforce, in CLI model 20.0.0. Builders ought to replace through npm in venture folders or globally, then confirm with “npm record @react-native-community/cli-server-api.”
For speedy safety, bind the server to localhost: “npx react-native begin –host 127.0.0.1.” This vulnerability underscores the perils of third-party sinks just like the “open” package deal and default community exposures in dev instruments.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.