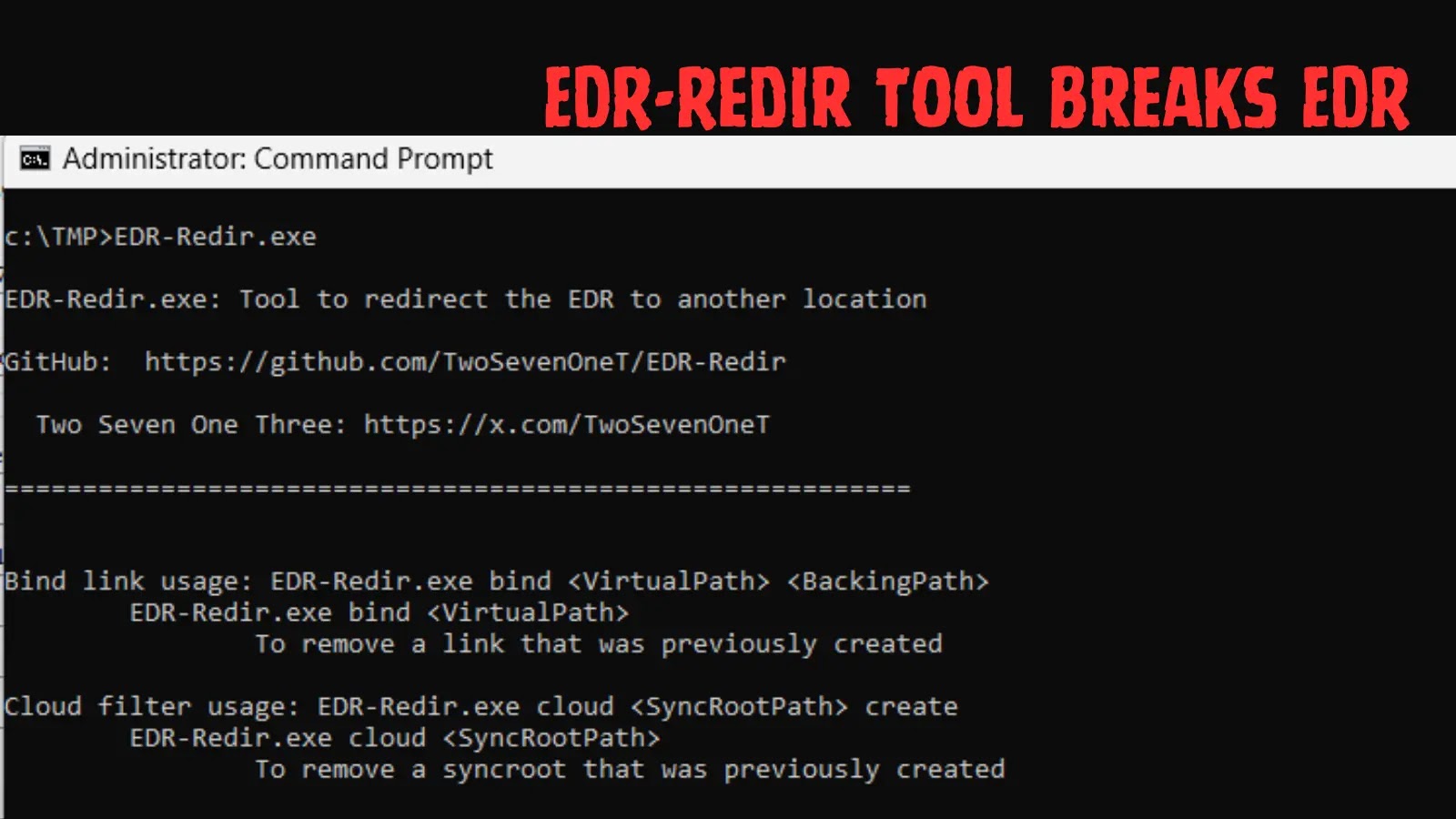
A extreme flaw in a serious automaker’s seller portal allowed unauthorized attackers to register for seller accounts, escalate privileges to a nationwide administrator, and in the end management automobiles remotely.
The vulnerability resides within the portal’s Java/SAP backend and AngularJS frontend, the place hidden registration kinds may very well be uncovered and abused.
Takeaways1. Attackers uncovered a hidden registration kind within the AngularJS frontend and submitted clean Invite_Token values.2. A JSESSIONID from the profile-update API, mixed with patched client-side checks, granted nationwide admin privileges.3. With elevated entry, the VIN enrollment API was abused to switch automobile possession and ship distant instructions.
Exploiting Hidden Registration and Session Tokens
In keeping with safety researcher Eaton Zveare, the assault started with the invention of a hidden HTML registration kind () that was meant to stay invisible till a sound invite token was equipped.
Registration Type
By forcing the shape to show through Chrome DevTools and omitting the Invite_Token parameter on the POST request, attackers bypassed server-side token validation fully.
The essential API endpoint accepted clean tokens, granting any rogue person the power to enroll as a seller worker.
As soon as registered, the attacker found that standard login didn’t create a usable session, however invoking the profile replace API did set up a sound JSESSIONID cookie.
With that session token, Zveare patched key JavaScript features utilizing Chrome’s Native Overrides function, commenting out commonUtil.srefInfo checks and bypasses the “Entry Denied” modal in commonUtil.checkStateValid().
This allowed navigation to the Inner & Exterior Consumer Administration module and publicity of each seller’s person record through the API:
Phishing on the seller’s dime
Distant Automobile Management
Following profitable privilege escalation to a nationwide admin group, Zveare accessed the seller SSO administration system and leveraged the “Portal Login As Seller” impersonation function.
By substituting the SSO_SYS_ID parameter within the SSO URL, he pivoted into sub-brand seller portals beforehand inaccessible.
This chain of exploits culminated in accessing the automobile enrollment API, which helps pairing buyer accounts to a VIN:
With possession transferred to his take a look at account, Zveare used the official cellular app to ship distant unlock and begin instructions, confirming full management.
Victims acquired an automatic electronic mail alert however lacked any means to reverse the silent takeover.
The flaw impacts all automobiles from the 2012 mannequin yr onward outfitted with commonplace telematics modules.
Automakers are urged to use fast patches to implement server-side invite token validation, tighten session administration for JSESSIONID cookies, and implement least-privilege checks on all administrative APIs.
The automaker in query has since launched model 1.2.3 of the seller portal, which mandatorily validates Invite_Token values and enforces role-based entry management on delicate endpoints.
Enhance your SOC and assist your crew defend your online business with free top-notch risk intelligence: Request TI Lookup Premium Trial.
Florence Nightingale is a senior safety and privateness reporter, overlaying knowledge breaches, cybercrime, malware, and knowledge leaks from cyber house every day.