Zoom has disclosed a essential vulnerability affecting a number of Home windows-based shoppers, doubtlessly permitting attackers to escalate privileges and compromise person programs.
Designated as CVE-2025-49457 below bulletin ZSB-25030, this flaw carries a CVSS rating of 9.6, classifying it as essential as a result of its excessive impression on confidentiality, integrity, and availability.
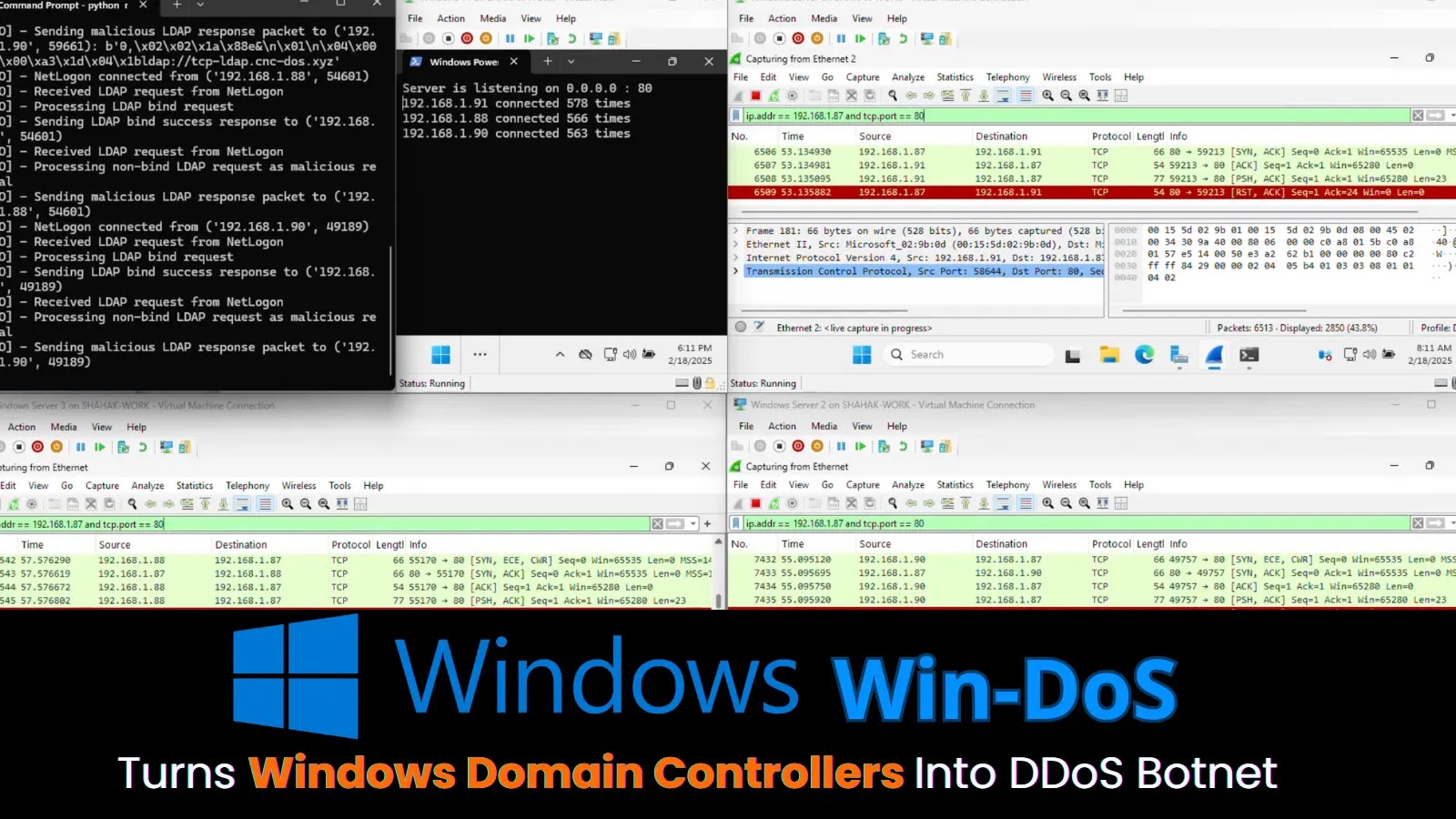
The vulnerability stems from an untrusted search path in sure Zoom Shoppers for Home windows. This situation permits an unauthenticated attacker to take advantage of the flaw over a community, requiring solely person interplay reminiscent of clicking a malicious hyperlink or opening a tainted file.
The CVSS vector string, CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H, highlights the benefit of assault: no privileges are wanted, complexity is low, and it will possibly change the scope of impression, resulting in excessive dangers of knowledge theft, system tampering, or full takeover.
Affected merchandise embody Zoom Office for Home windows earlier than model 6.3.10, Zoom Office VDI for Home windows earlier than 6.3.10 (excluding variations 6.1.16 and 6.2.12), Zoom Rooms for Home windows earlier than 6.3.10, Zoom Rooms Controller for Home windows earlier than 6.3.10, and Zoom Assembly SDK for Home windows earlier than 6.3.10. Customers operating these outdated variations are urged to replace instantly to mitigate dangers.
Zoom Shoppers for Home windows Vulnerability
Found and reported by Zoom’s Offensive Safety staff, this vulnerability underscores ongoing challenges in software program safety, significantly with path-handling mechanisms in Home windows environments.
Untrusted search paths happen when purposes load recordsdata from insecure directories, permitting malicious actors to inject dangerous DLLs or executables.
In Zoom’s case, this might allow privilege escalation, the place an attacker positive factors elevated entry, doubtlessly putting in malware, accessing delicate knowledge, or disrupting companies.
The implications are extreme for Zoom’s huge person base, which incorporates companies, educators, and people counting on the platform for digital conferences.
With distant work nonetheless prevalent in 2025, such flaws might result in widespread breaches, eroding belief in video conferencing instruments. Specialists word that comparable vulnerabilities have plagued software program up to now, usually exploited in provide chain assaults or phishing campaigns.
Zoom has responded swiftly, advising customers to obtain the most recent updates from its official website. “Making use of these patches is essential for sustaining safety,” a Zoom spokesperson said. Further protecting measures embody enabling computerized updates, utilizing antivirus software program, and avoiding suspicious hyperlinks.
This incident highlights the significance of proactive safety practices. As cyber threats evolve, common updates and vigilance stay key defenses in opposition to exploitation. Organizations ought to evaluation their Zoom deployments and educate customers on protected practices to stop potential incidents.
Enhance your SOC and assist your staff shield your enterprise with free top-notch risk intelligence: Request TI Lookup Premium Trial.