As organizations speed up cloud adoption, misconfigurations have emerged as a important vulnerability, accounting for 23% of cloud safety incidents and 81% of cloud-related breaches in 2024.
Excessive-profile circumstances, such because the 2025 Capital One breach that uncovered 100 million data because of a misconfigured firewall, underscore the urgency of addressing this difficulty.
With world cloud spending projected to succeed in $591.8 billion this 12 months, safety groups face mounting stress to implement sturdy detection and remediation frameworks.
The Rising Menace Panorama
Trendy cloud environments’ complexity exacerbates configuration dangers.
A 2024 Cloud Safety Alliance research revealed that 82% of enterprises skilled safety incidents from misconfigurations, typically stemming from overly permissive community guidelines or uncovered storage buckets.
These errors create assault vectors for risk actors, enabling credential theft, information exfiltration, and cryptojacking campaigns just like the 2025 Tesla Kubernetes breach.
The monetary repercussions are extreme: IBM estimates the typical information breach price at $4.35 million, whereas regulatory penalties beneath GDPR and HIPAA can escalate prices additional.
Past financial losses, reputational injury persists lengthy after incidents-63% of customers abandon manufacturers post-breach.
Detection Challenges in Dynamic Environments
Conventional safety instruments wrestle with cloud visibility gaps, as 67% of organizations lack complete insights into their infrastructure.
This opacity permits misconfigurations to linger, exemplified by Toyota’s 2023 publicity of 260,000 buyer data by an improperly secured database.
Automated Cloud Safety Posture Administration (CSPM) instruments now lead detection efforts. Platforms like Cloudanix and Verify Level CloudGuard make use of steady scanning to establish:
Overly permissive Id and Entry Administration (IAM) roles
Unrestricted inbound/outbound ports (e.g., SSH/RDP uncovered to 0.0.0.0/0)
Non-compliant storage buckets with public learn/write entry
Unpatched container photographs in Kubernetes clusters
CSPM options map configurations in opposition to frameworks like CIS Benchmarks and NIST, offering real-time danger scoring. For example, Sysdig’s 2025 evaluation discovered organizations utilizing CSPM decreased misconfiguration dwell time from 78 days to beneath 48 hours.
Whereas detection is essential, well timed remediation stays the last word problem. The Cloud Safety Alliance advocates a three-tier strategy:
1. Automated Guardrails
Cloud-native instruments like AWS GuardDuty and Azure Safety Heart allow prompt remediation for important dangers. When Cloudanix detects an uncovered S3 bucket, it might mechanically limit entry by way of pre-approved playbooks whereas alerting safety groups.
This balances pace with oversight, stopping 92% of important misconfigurations from progressing to breaches.
2. Infrastructure-as-Code (IaC) Validation
Integrating safety into CI/CD pipelines catches errors pre-deployment. Instruments like Tenable scan Terraform templates for:
Hardcoded credentials
Overprivileged service accounts
Non-compliant community ACLs
GitLab reviews a 40% discount in cloud breaches amongst groups adopting IaC validation.
3. Human-Centric Coaching
Regardless of automation’s rise, 88% of misconfigurations are nonetheless traced to human error. Progressive organizations now implement:
Cloud safety certifications for DevOps groups
Interactive labs simulating breach situations
Simply-in-time entry controls scale back standing privileges
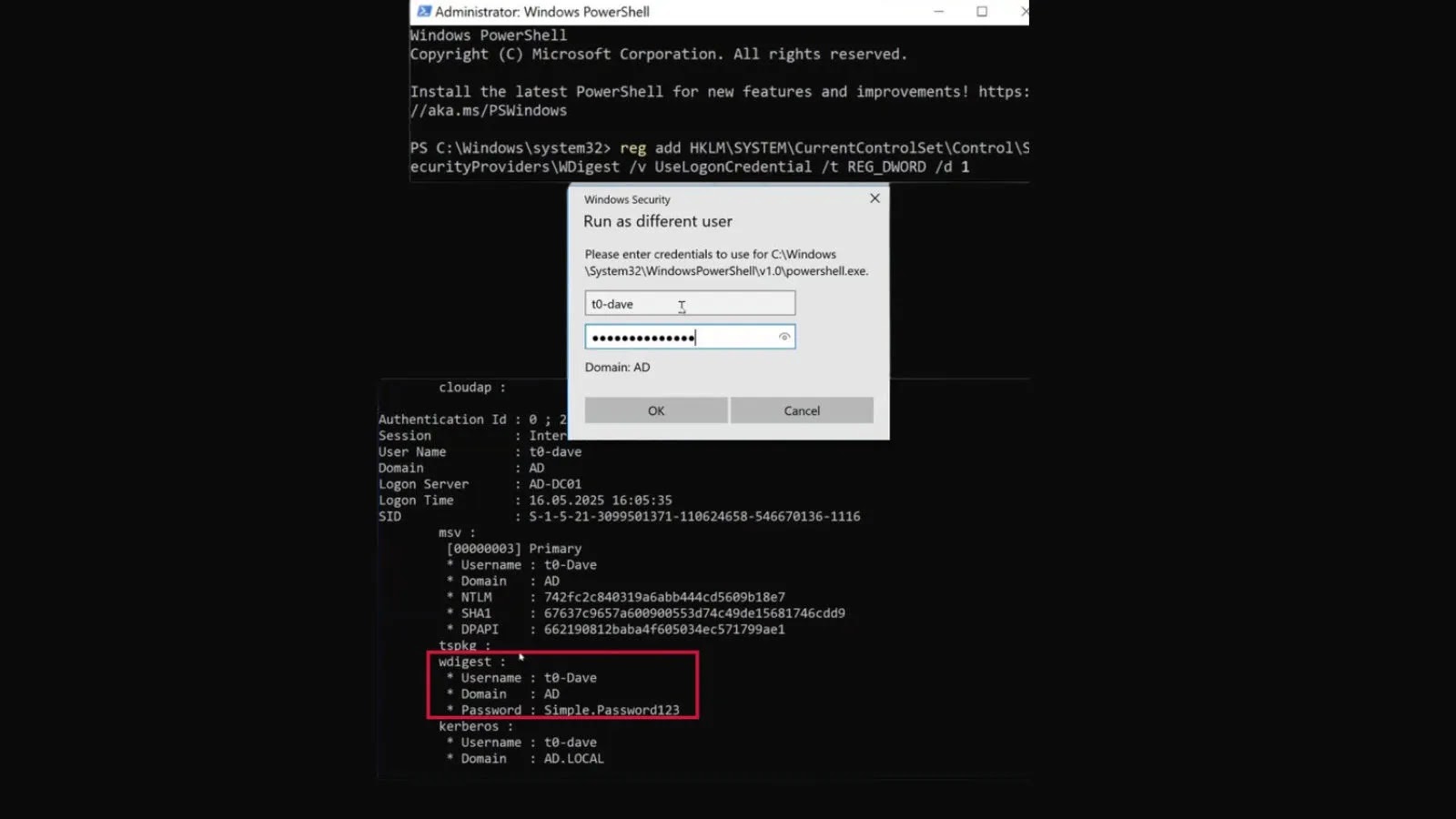
Capital One’s Firewall Misconfiguration (2025)
Attackers exploited a misconfigured net software firewall (WAF) to steal AWS credentials, accessing 100 million buyer records6. The breach highlighted gaps in:
Submit-incident, Capital One carried out Lacework’s AI-driven anomaly detection, lowering false positives by 70% whereas halving response occasions.
Tesla’s Cryptojacking Incident (2025)
Hackers infiltrated Tesla’s Kubernetes console by way of a passwordless admin interface, mining cryptocurrency whereas accessing delicate telemetry information. The assault underscored the necessity for:
Necessary MFA on all orchestration instruments
Community segmentation between improvement and manufacturing environments
Steady container picture vulnerability scanning
Future Outlook: AI and Proactive Protection
Rising applied sciences promise to reshape misconfiguration administration:
Predictive analytics: Machine studying fashions analyze historic information to forecast high-risk configuration modifications, reaching 89% accuracy in beta exams.
Self-healing clouds: Experimental reinforcement studying techniques mechanically modify safety teams and IAM insurance policies with out human intervention.
Quantum-resistant encryption: With quantum computing advancing, NIST-approved algorithms are being built-in into CSPM platforms to future-proof cloud information.
Nevertheless, consultants warning in opposition to over-reliance on instruments. Gartner emphasizes that by 2026, 45% of organizations will mix CSPM with enhanced developer coaching to deal with the basis causes of configuration errors.
As cloud environments grow to be advanced, a layered protection technique mixing automation, schooling, and proactive monitoring presents the very best path to resilience.
With misconfiguration-related breaches projected to price enterprises $5 trillion yearly by 2026, the time for motion is now.
Discover this Information Fascinating! Observe us on Google Information, LinkedIn, & X to Get Prompt Updates!