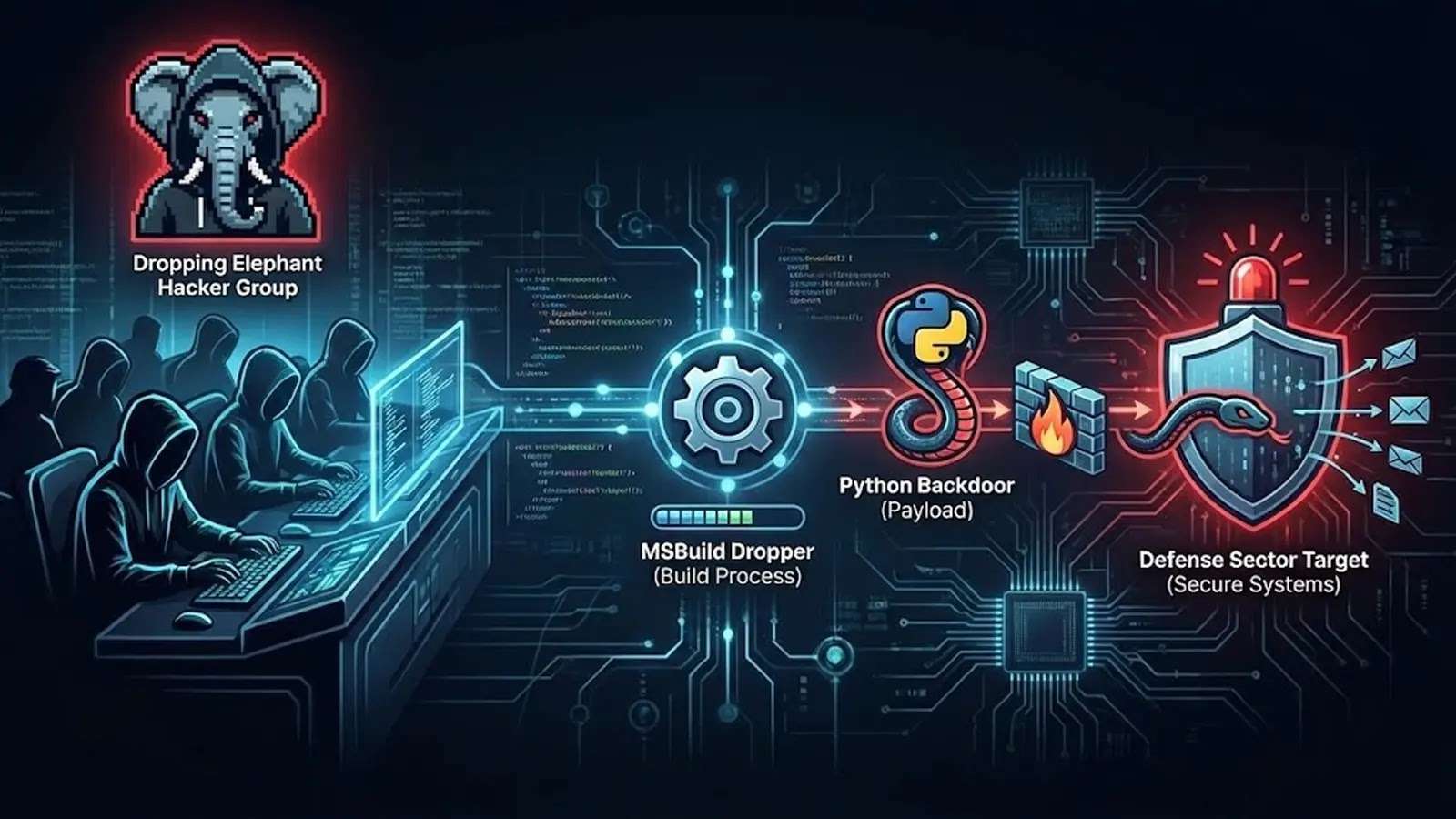
India-aligned menace group Dropping Elephant has launched a complicated multi-stage cyberattack concentrating on Pakistan’s protection sector utilizing a Python-based distant entry trojan disguised inside an MSBuild dropper.
Idan Tarab has recognized this superior marketing campaign that leverages pretend defense-related phishing lures to compromise army analysis and growth models and procurement services linked to Pakistan’s Nationwide Radio and Telecommunication Company.
The assault begins innocuously with a phishing e-mail containing a malicious ZIP archive. As soon as downloaded, the archive contains an MSBuild challenge file that serves because the preliminary dropper, together with a decoy PDF designed to look professional.
When executed, the dropper begins downloading a number of parts to the Home windows Duties listing, establishing persistence through scheduled duties with seemingly professional names comparable to KeyboardDrivers and MsEdgeDrivers.
Safety researcher Idan Tarab famous that Dropping Elephant employed subtle obfuscation methods all through the an infection chain, utilizing UTF-reverse encryption to reconstruct strings and dynamic API decision to keep away from detection by safety instruments.
The group’s method demonstrates vital technical maturity in weaponizing professional Home windows utilities as a part of their assault infrastructure.
The Stealth Python Persistence Mechanism
The operation’s centerpiece includes deploying a whole embedded Python runtime to the AppData listing, the place a pretend DLL file named python2_pycache_.dll really comprises marshalled Python bytecode relatively than professional library code.
This payload executes through pythonw.exe, which runs with out displaying a window, offering deep stealth towards potential defenders.
The Python backdoor contains a number of modules, comparable to consumer, instructions, remote_module, and base.py, enabling complete system management and data gathering from compromised machines.
The malware maintains command-and-control communication by way of domains together with nexnxky.data, upxvion.data, and soptr.data.
The recognized code comprises closely obfuscated variable names and base64-encoded command constructions, making handbook evaluation significantly difficult.
The group employed particular file paths and job scheduler entries that mimic professional Home windows operations, permitting the backdoor to mix seamlessly into common system exercise whereas remaining dormant till receiving instructions from attacker-controlled infrastructure.
This marketing campaign underscores the persistent menace from superior persistent menace teams concentrating on defense-critical infrastructure in South Asia.
Organizations ought to implement enhanced monitoring for suspicious MSBuild executions and for uncommon Python runtime deployments in system directories, and preserve strict controls over phishing protection mechanisms.
Observe us on Google Information, LinkedIn, and X to Get Extra On the spot Updates, Set CSN as a Most well-liked Supply in Google.