Cybersecurity consultants at ANY.RUN not too long ago unveiled alarming tendencies in how attackers are exploiting on a regular basis applied sciences to bypass safety operations facilities (SOCs).
They dissected techniques like QR code phishing, ClickFix social engineering, and Residing Off the Land Binaries (LOLBins), displaying how these strategies evade conventional defenses.
As threats develop extra refined, SOC groups face mounting strain to adapt, with low detection charges risking extreme breaches. Drawing from analyses of real-world samples, the session emphasised interactive instruments and real-time intelligence as very important countermeasures.
ClickFix Assaults: Mastering Human Deception
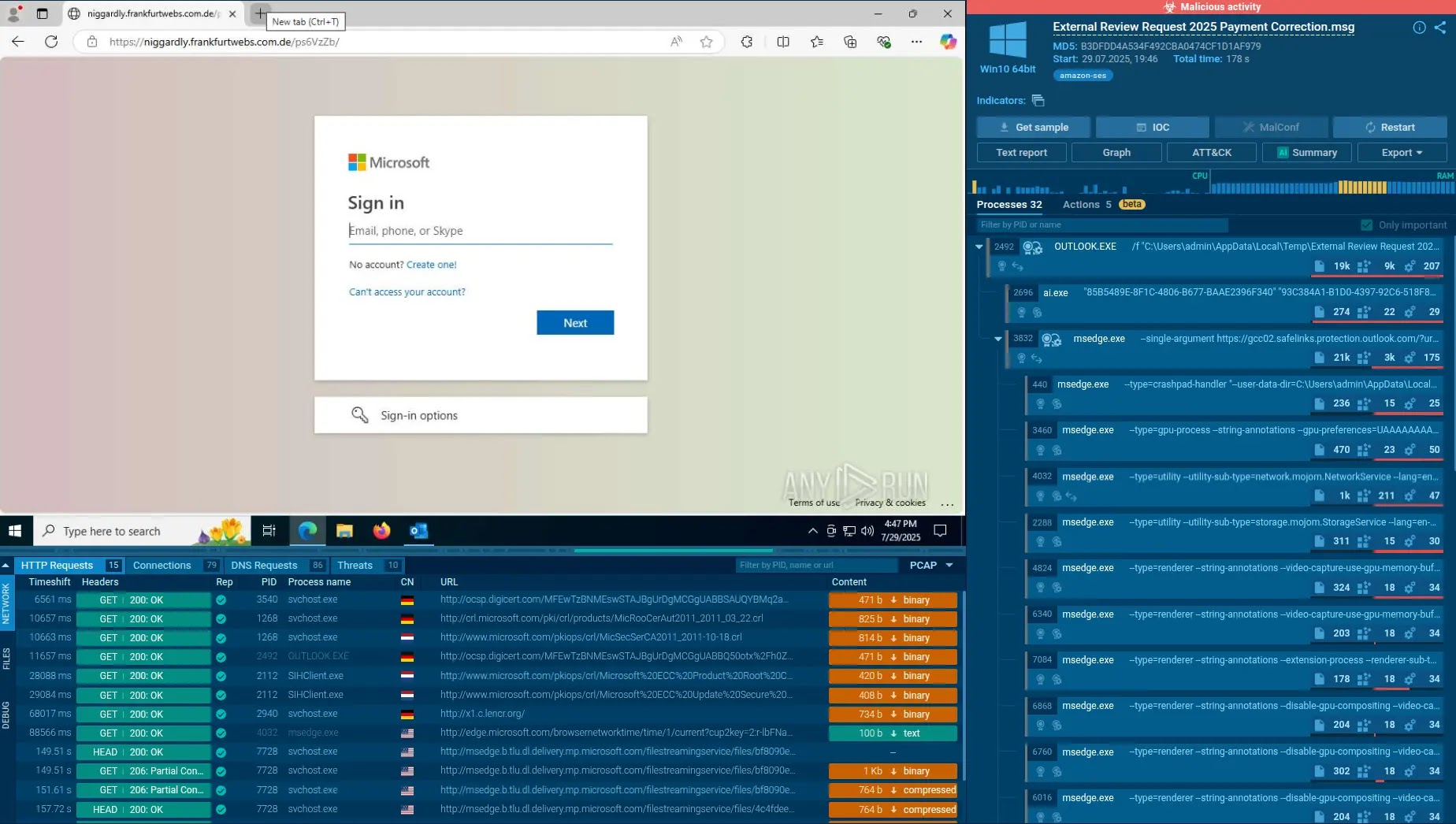
ClickFix assaults stand out for his or her reliance on consumer interplay, turning routine verifications into malware gateways. Attackers ship phishing emails mimicking trusted websites, like reserving platforms, full with faux CAPTCHAs.
As soon as a sufferer clicks, a malicious PowerShell script hijacks the clipboard unnoticed, prompting the consumer to stick and execute it by way of a system dialog.
This multi-stage ploy thrives on deception: double spoofing creates convincing replicas, whereas handbook steps foil automated scanners.
Sandbox analyses reveal how execution deploys stealers like Lumma or AsyncRAT, plus ransomware, establishing persistence via startup recordsdata.
Conventional instruments falter at CAPTCHAs, however interactive sandboxes simulate human actions, exposing the total chain from preliminary click on to payload supply in seconds.
With out such capabilities, SOCs miss threats that mix seamlessly into consumer workflows, resulting in credential theft and system compromise.
PhishKit Assaults: QR Codes as Stealth Vectors
Phishing kits, or phishkits, have developed into darkish internet staples, empowering novices to launch pro-level campaigns towards giants like Microsoft and Google.
The most recent twist integrates QR codes into PDF attachments disguised as DocuSign docs, directing scans to cell units the place phishing cues conceal on small screens.
These kits incorporate AI-generated lures, multi-stage checks, and CAPTCHAs like Cloudflare Turnstile, culminating in faux login pages for credential harvesting.
ANY.RUN’s automated detonation extracts QR hyperlinks, solves challenges, and traces the kill chain, revealing ties to teams like Storm-1747.
Many defenses overlook QR content material, permitting evasion, however superior sandboxes deal with this autonomously, reducing Tier 1 workloads by 20%. As phishkits proliferate, focusing on areas by way of localized lures, SOCs should prioritize QR scanning to curb widespread campaigns.
LOLBins: Weaponizing Trusted Instruments
LOLBins exploit Home windows’ personal utilities, PowerShell, mshta.exe, and cmd.exe to masks malice as routine operations. A phishing .lnk file may invoke mshta by way of PowerShell to fetch payloads from distant servers, downloading decoy PDFs to obscure the actual stealer, like DeerStealer.
This “residing off the land” strategy evades whitelists and antivirus software program by mimicking admin duties, leaving faint forensic traces.
Behavioral evaluation in sandboxes uncovers connections to C2 servers and persistence mechanisms, distinguishing abuse from legitimacy.
With out context from international investigations, alerts set off false positives. Risk intelligence feeds, pulling contemporary IOCs from 1000’s of periods, allow real-time blocking, slashing response occasions.
The techniques employed by ClickFix, together with interactivity, QR obfuscation, and LOLBin stealth, spotlight the restrictions of relying solely on automation.
ANY.RUN’s options, which mix interactive evaluation with shared intelligence, improve detection charges by 88% in underneath a minute and cut back imply time to resolve (MTTR) by 21 minutes.
Safety Operations Facilities (SOCs) that implement these options report a 30% lower in escalations and a tripling of effectivity, thereby strengthening their defenses towards an more and more relentless adversary panorama.
Improve your SOC Efficiency With Interactive Sandbox Risk Intelligence Lookup and Feeds => Strive Now