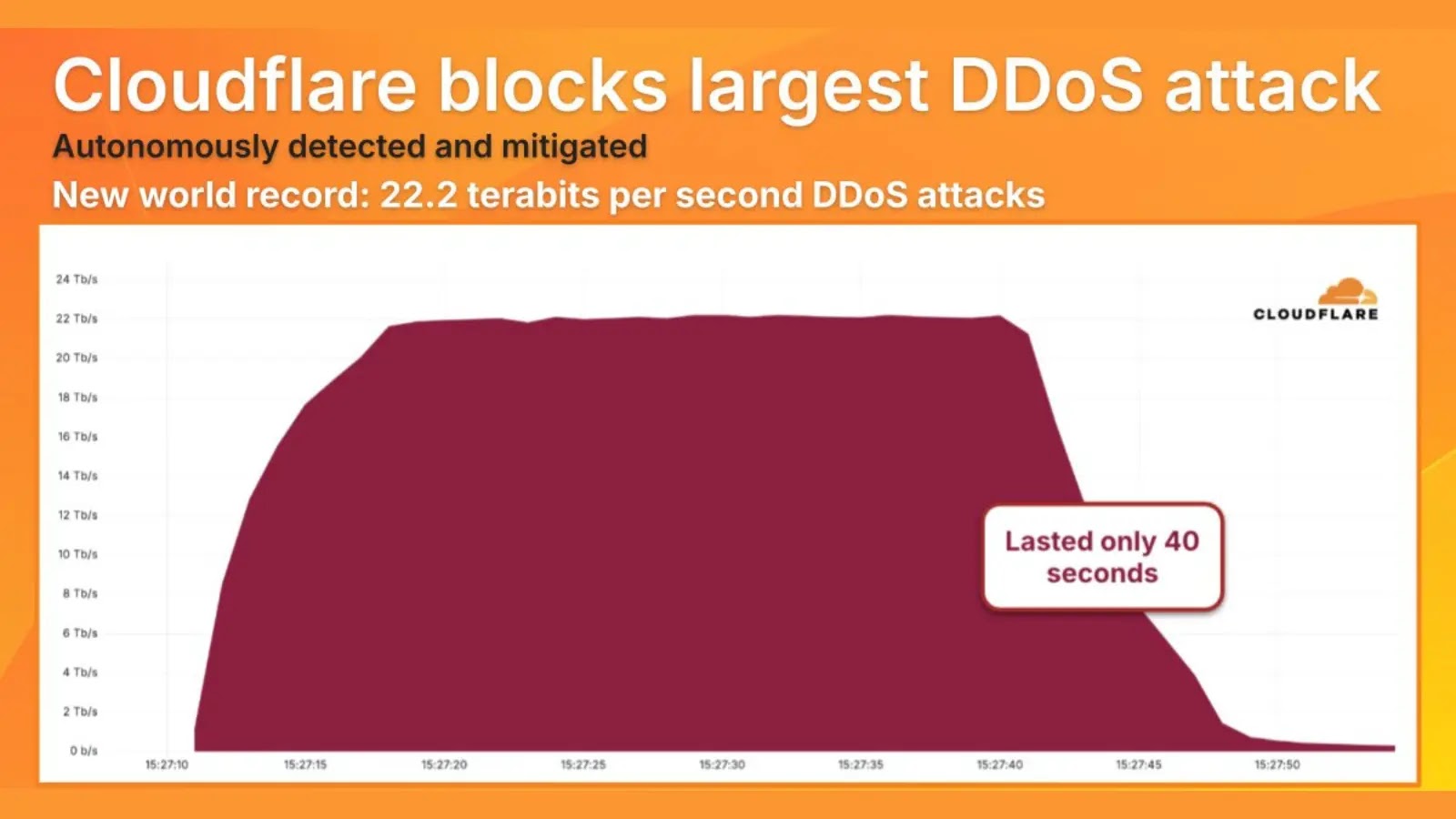
The cybersecurity trade is essentially reworking as organizations shift from conventional endpoint safety to superior menace detection with Endpoint Safety EDR vs XDR options.
With the worldwide Prolonged Detection and Response (XDR) market projected to achieve $3.07 billion by 2030, rising at a exceptional 19.8% compound annual development price, companies more and more acknowledge the restrictions of endpoint-focused safety options and embrace holistic approaches that span their whole digital infrastructure.
Market Forces Drive Safety Evolution
The surge in XDR adoption displays the altering nature of recent cyber threats and enterprise operations. The normal Endpoint Detection and Response (EDR) market, valued at $2.87 billion in 2022, continues to develop at a strong 24.9% CAGR. Nonetheless, organizations are discovering that endpoint-only safety leaves crucial safety gaps.
This shift grew to become notably pronounced throughout the COVID-19 pandemic, accelerating the adoption of distant work and increasing assault surfaces past conventional company boundaries.
Latest product launches underscore this evolution. Kaspersky’s debut of its “Kaspersky Subsequent” product line in April 2024 exemplifies the trade development, providing tiered options that mix EDR with XDR capabilities.
The corporate’s three-tier strategy, EDR Foundations, EDR Optimum, and XDR Skilled, displays the market’s recognition that totally different organizations require various ranges of safety sophistication based mostly on their assets and menace publicity.
Technical Capabilities: Scope Defines the Distinction
The elemental distinction between EDR and XDR lies of their operational scope and knowledge correlation capabilities. EDR options excel at monitoring endpoint actions, offering detailed forensic knowledge about particular person units, together with course of exercise, file adjustments, and system occasions.
These platforms function beneath an “assume breach” mentality, repeatedly analyzing endpoint behaviors to detect malicious actions and automate quick response actions equivalent to machine isolation.
XDR represents an evolutionary leap, extending safety past endpoints to embody networks, cloud workloads, e-mail programs, and purposes.
Reasonably than focusing solely on particular person units, XDR platforms accumulate and correlate knowledge throughout a number of safety layers, offering safety groups with a unified view of threats that will span varied assault vectors.
This broader perspective allows the detection of refined multi-stage assaults which may evade endpoint-only monitoring.
The info correlation capabilities distinguish XDR from conventional safety approaches. Whereas EDR operates primarily on the machine stage, XDR mechanically correlates seemingly unrelated alerts from telephones, servers, and community infrastructure, making it notably efficient at unraveling advanced, multi-vector assaults.
This correlation reduces false positives and improves detection accuracy by offering contextual consciousness throughout the whole safety ecosystem.
Strategic Enterprise Issues
Organizations evaluating EDR versus XDR face a number of crucial concerns past technical capabilities. Price stays a major issue, with EDR options usually providing extra budget-friendly choices for organizations with restricted monetary assets.
For corporations with established safety groups and well-defined endpoint safety wants, EDR supplies targeted, cost-effective safety protection.
Nevertheless, the enterprise case for XDR strengthens for organizations with advanced IT environments, restricted safety experience, or complete menace safety necessities.
Gartner analysis signifies that XDR adoption primarily targets organizations with smaller safety groups that won’t have totally utilized SIEM and SOAR merchandise. This makes XDR notably engaging for companies looking for to consolidate safety instruments whereas enhancing operational effectivity.
The managed XDR market, estimated at $5 billion in 2025 and projected to achieve $25 billion by 2033, displays the rising demand for outsourced safety experience.
This development addresses the crucial cybersecurity expertise scarcity, permitting organizations to entry superior menace detection capabilities with out constructing in depth in-house safety groups.
Business Functions and Regional Tendencies
Sector-specific adoption patterns reveal various safety priorities throughout industries. The Banking, Monetary Companies, and Insurance coverage (BFSI) sector leads EDR adoption with a 19.5% market share, pushed by regulatory necessities and high-value knowledge safety wants.
In the meantime, the retail and e-commerce sector exhibits the quickest EDR development at 28.3% CAGR, reflecting elevated digitalization and cyber menace publicity.
Geographically, North America dominates each markets, accounting for 32.4% of the EDR market, whereas Asia-Pacific emerges because the fastest-developing area with 27.2% CAGR development.
America XDR market alone is projected to achieve $1.32 billion by 2030, whereas Germany leads European adoption with over 18% regional market share.
Future Outlook: Integration and Intelligence
The cybersecurity panorama continues evolving towards built-in, intelligence-driven platforms that mix the strengths of each EDR and XDR approaches.
As organizations migrate to hybrid cloud environments and undertake extra distributed work fashions, the demand for complete menace detection and response capabilities will solely intensify.
The strategic shift from EDR to XDR represents greater than a technological improve; it displays a elementary change in how organizations strategy cybersecurity.
By embracing options that present holistic visibility, automated correlation, and coordinated response mechanisms, companies are higher positioned to defend in opposition to the subtle, multi-vector assaults that outline right this moment’s menace panorama.
Discover this Information Attention-grabbing! Comply with us on Google Information, LinkedIn, & X to Get On the spot Updates!