A complicated method dubbed “ECScape” that enables malicious containers operating on Amazon Elastic Container Service (ECS) to steal AWS credentials from different containers sharing the identical EC2 occasion.
The invention highlights crucial isolation weaknesses in multi-tenant ECS deployments and underscores the safety benefits of AWS Fargate’s micro-VM structure.
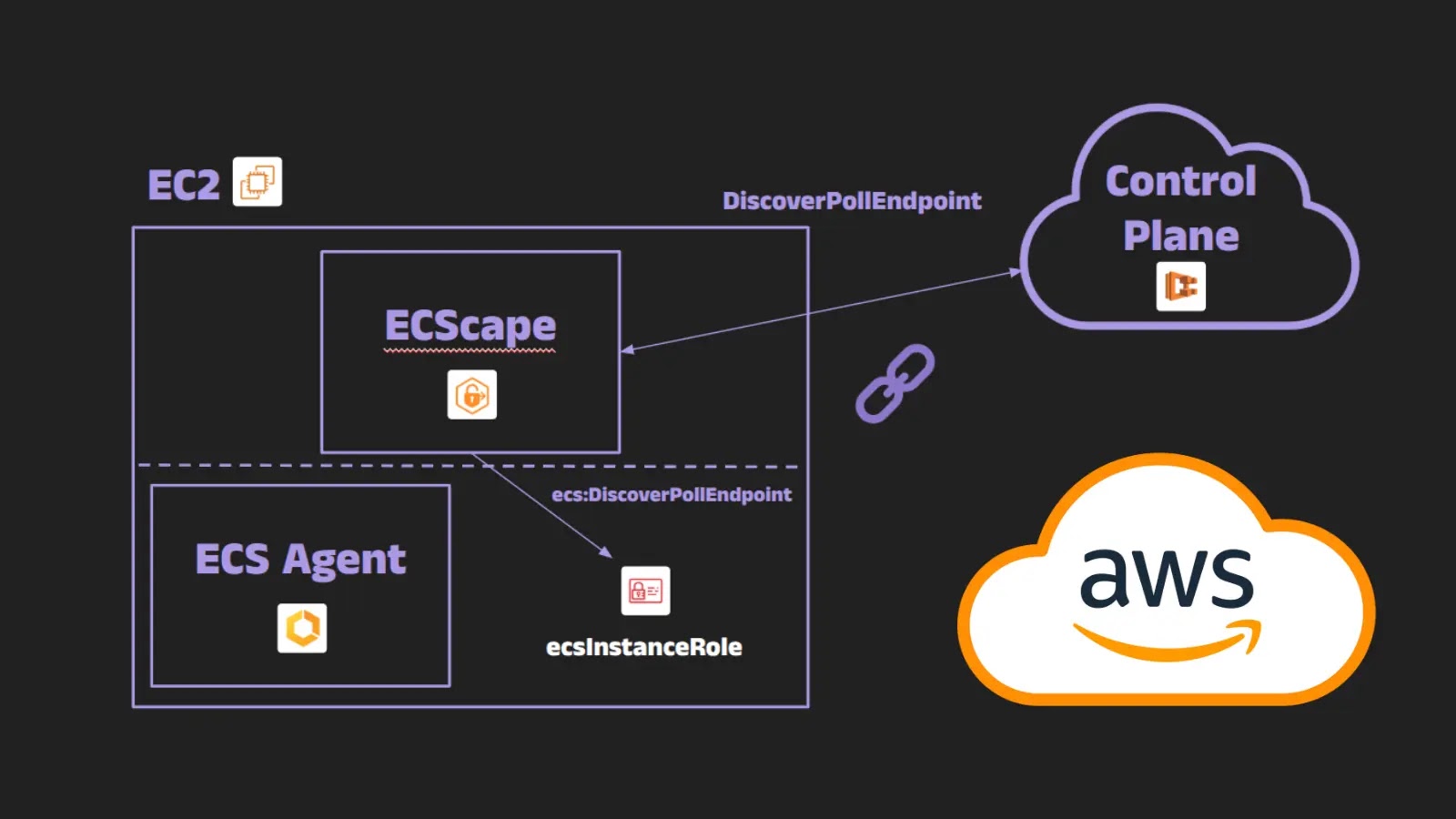
The method, developed by safety researcher Naor Haziz, exploits an undocumented inside protocol between ECS brokers and AWS’s management airplane to exfiltrate IAM credentials throughout container boundaries.
In contrast to conventional container escape strategies requiring host-level entry, ECScape operates completely throughout the container’s namespace whereas leveraging community manipulation to impersonate the ECS agent.
The assault begins when a compromised container accesses the Occasion Metadata Service (IMDS) at 169.254.169.254 to acquire the EC2 occasion’s IAM function credentials. These credentials, usually utilized by the ECS agent for reliable operations, turn into the inspiration for the following impersonation assault.
Utilizing the stolen occasion credentials, attackers can uncover the ECS management airplane’s polling endpoint by the ecs:DiscoverPollEndpoint API and collect important identifiers, together with cluster ARNs and container occasion ARNs.
The malicious course of then establishes a cast WebSocket connection to AWS’s Agent Communication Service (ACS), the inner channel by which ECS delivers job credentials to brokers.
ECScape Assault Abuses ECS Protocol
By together with the parameter sendCredentials=true within the WebSocket handshake, attackers can obtain all IAM credentials for each job operating on the shared EC2 occasion.
This consists of each software function credentials and job execution function credentials, which frequently comprise delicate permissions for accessing AWS Secrets and techniques Supervisor, ECR repositories, and CloudWatch Logs.
ECScape demonstrates significantly regarding stealth traits, as stolen credentials operate identically to reliable ones. AWS CloudTrail logs attribute API calls to the sufferer job’s function relatively than the attacking container, making preliminary detection extraordinarily difficult.
The method breaks basic assumptions about container isolation in ECS environments, permitting low-privileged duties to imagine the permissions of high-privileged containers on the identical host.
In demonstration environments, researchers confirmed how a container with deny-all IAM insurance policies might efficiently delete S3 buckets utilizing stolen credentials from a neighboring job with S3 full entry.
The assault additionally enabled the extraction of delicate secrets and techniques meant for different containers, successfully compromising the multi-tenant safety mannequin.
AWS reviewed the findings by their coordinated disclosure program however categorised the habits as a design consideration relatively than a vulnerability. The corporate emphasised that containers sharing EC2 cases are implicitly a part of the identical belief area until customers implement correct isolation measures.
Following the disclosure, AWS up to date its documentation to explicitly warn that “duties operating on the identical EC2 occasion might doubtlessly entry credentials belonging to different duties on that occasion”. The corporate strongly recommends AWS Fargate for situations requiring stronger isolation ensures.
Safety specialists advocate a number of mitigation methods: disabling or proscribing IMDS entry for containers by community controls or the ECS_AWSVPC_BLOCK_IMDS setting, avoiding co-location of high-privilege and low-privilege duties on shared cases, implementing least-privilege IAM insurance policies for all job roles, and deploying complete CloudTrail monitoring to detect uncommon credential utilization patterns.
Organizations operating ECS on EC2 ought to deal with every occasion as a possible failure area and take into account migrating delicate workloads to Fargate’s remoted micro-VM structure for enhanced safety boundaries.
Equip your SOC with full entry to the newest menace knowledge from ANY.RUN TI Lookup that may Enhance incident response -> Get 14-day Free Trial