Abstract
1. Scammers inject pretend cellphone numbers into official firm web sites (Netflix, Microsoft, Financial institution of America) utilizing malicious URL parameters.
2. Cybercriminals purchase Google adverts resulting in actual web sites with encoded URLs that exploit search vulnerabilities to show fraudulent contact info.
3. Victims see genuine firm URLs and layouts, making pretend numbers seem as official search outcomes.
4. Keep away from calling numbers present in URLs, and confirm contact information by official channels.
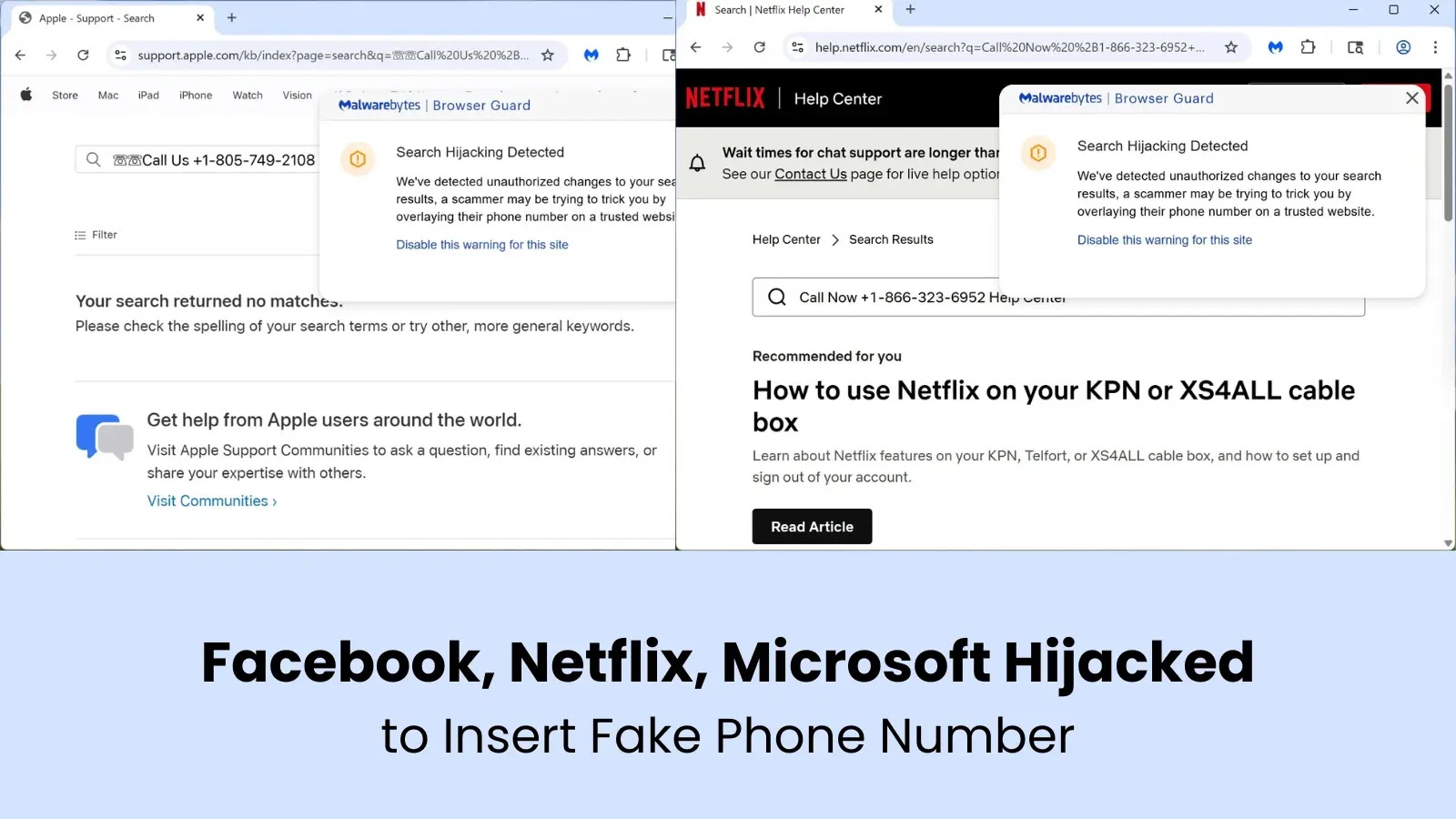
A classy rip-off operation focusing on main American corporations, together with Netflix, Microsoft, and Financial institution of America, the place attackers manipulate official web sites to show fraudulent cellphone numbers.
The assault, technically categorized as a search parameter injection assault, exploits vulnerabilities in web site search functionalities to embed scammer-controlled contact info immediately onto official firm pages.
This technique proves notably harmful as a result of victims see the genuine firm URL of their browser tackle bar whereas unknowingly viewing malicious content material, making the rip-off practically unattainable to detect with out specialised safety instruments.
Search Parameter Injection Assault
Malwarebytes studies that the scammers orchestrate their assaults by a multi-step course of starting with sponsored search outcomes on Google.
Cybercriminals buy ads that seem to signify official manufacturers, directing customers to what seems to be official assist pages.
Nevertheless, these hyperlinks include malicious URL parameters that exploit mirrored enter vulnerabilities within the goal web sites’ search performance.
When victims click on these poisoned hyperlinks, they land on real firm web sites—Netflix, Microsoft, Financial institution of America, PayPal, Apple, Fb, and HP—however with a vital distinction.
The attackers craft URLs containing encoded characters like %20 (representing areas) and %2B (representing plus indicators) together with their fraudulent cellphone numbers.
These parameters manipulate the location’s search outcomes to prominently show the scammer’s contact info as an alternative of official assist numbers.
Netflix Search Outcomes
The Netflix instance demonstrates how attackers embed pretend cellphone numbers immediately into the search outcomes show, making it seem as if the fraudulent quantity is an official search outcome from Netflix’s personal system.
This URL manipulation approach bypasses conventional safety measures as a result of the sufferer stays on the genuine web site all through the complete course of.
The success of those assaults depends on web sites’ failure to correctly sanitize search question parameters. When customers enter search phrases, many company web sites merely mirror no matter knowledge seems within the URL with out ample validation.
Apple Rip-off
This creates a mirrored enter vulnerability that scammers exploit to inject their malicious content material.
The encoded characters within the URLs serve a twin function: they assist bypass primary safety filters whereas guaranteeing the malicious cellphone numbers show accurately on the goal web sites.
As an illustration, the %20 encoding permits areas in cellphone numbers to render correctly, whereas %2B ensures plus indicators seem accurately in worldwide cellphone quantity codecs.
Customers ought to look ahead to crimson flags, together with cellphone numbers showing in URLs, suspicious search phrases like “Name Now” or “Emergency Assist” within the browser tackle bar, and extreme encoded characters alongside cellphone numbers.
Earlier than calling any assist quantity discovered by search outcomes, customers ought to confirm the contact info by official firm communications or social media channels to make sure authenticity and keep away from falling sufferer to those subtle scams.
Stay Credential Theft Assault Unmask & Prompt Protection – Free Webinar