A complicated new variation of cyberattacks emerged in July 2025, exploiting a crucial vulnerability in how Chrome and Microsoft Edge deal with webpage saving performance.
The assault, dubbed “FileFix 2.0,” bypasses Home windows’ Mark of the Internet (MOTW) safety characteristic by leveraging professional browser saving mechanisms mixed with HTML Software (HTA) execution.
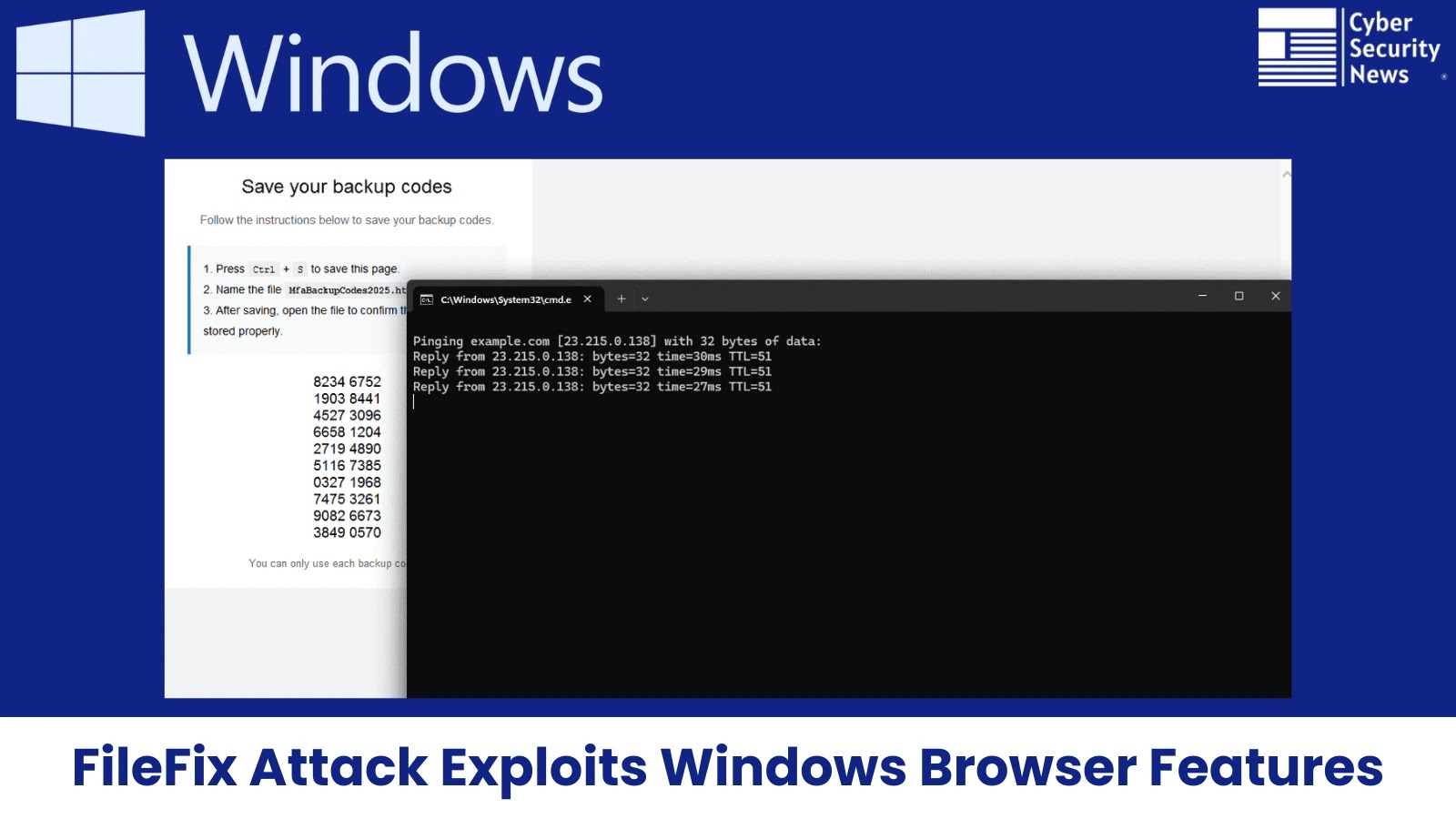
Key Points1. Saving HTML pages as “Webpage, Full” or “Webpage, Single File” in Chrome or Edge with sure MIME varieties leads to recordsdata with out Mark-of-the-Internet (MOTW) safety.2. Attackers trick customers into saving these recordsdata as .hta (HTML Software) recordsdata, which may execute malicious scripts with out warnings.3. Social engineering, comparable to faux backup code pages, prompts customers to save lots of and open these harmful recordsdata.4. Blocking or eradicating mshta.exe stops these .hta recordsdata from working and prevents the assault.
The invention comes amid a dramatic surge in social engineering assaults this yr.
In line with the newest ESET Menace Report, ClickFix assaults, the predecessor to FileFix, skyrocketed by 517% within the first half of 2025, turning into the second commonest assault vector after phishing and accounting for practically 8% of all blocked assaults.
This explosive progress demonstrates a rising reliance by risk actors on psychological manipulation somewhat than purely technical exploits.
The brand new assault variant exploits a beforehand unknown habits in Chrome and Microsoft Edge browsers.
When customers save webpages utilizing Ctrl+S with “Webpage, Single File” or “Webpage, Full” codecs chosen, recordsdata with HTML or XHTML+XML MIME varieties are saved with out MOTW safety, the Home windows safety characteristic that warns customers about doubtlessly harmful recordsdata from the web.
Cybersecurity researcher mr.d0x, who first documented the unique FileFix assault, has now revealed this extra insidious variation that mixes browser performance with HTML Purposes (HTA) recordsdata.
In contrast to conventional malware supply strategies, this method doesn’t require victims to disable security measures or ignore warning messages.
Social Engineering By means of Pretend Backup Codes
The assault’s social engineering element is especially intelligent. Menace actors create legitimate-looking web sites that mimic fashionable on-line providers, displaying what seems to be multi-factor authentication backup codes.
The pages instruct customers to save lots of the codes regionally utilizing Ctrl+S, particularly naming the file with a “.hta” extension for “correct storage”.
The misleading interface presents acquainted parts styled to resemble Google or Microsoft authentication pages, full with numbered backup codes {and professional} directions.
HTA through backup codes
Victims, believing they’re securely storing vital safety credentials, unknowingly obtain and execute malicious HTML Purposes that may run arbitrary instructions on their techniques.
MOTW historically serves as Home windows’ first line of protection towards internet-downloaded threats. When recordsdata carry this mark, Home windows shows safety warnings or blocks execution completely.
Nonetheless, the FileFix 2.0 approach circumvents this safety by professional browser habits. The vulnerability stems from browsers’ dealing with of particular MIME varieties in the course of the save operation.
Whereas most file varieties obtain MOTW safety, HTML and XHTML+XML content material saved by browser “Save As” performance bypasses this safety measure completely. This creates an execution pathway that seems professional to each safety software program and customers.
HTA Recordsdata: A Persistent Assault Vector
HTML Purposes symbolize a legacy Home windows characteristic that continues to pose safety dangers in 2025.
These recordsdata execute with full system privileges, basically functioning as desktop functions whereas sustaining HTML-based interfaces. Regardless of their age, HTA recordsdata stay supported throughout all Home windows variations, together with Home windows 11.
Current cybersecurity analysis signifies renewed curiosity in HTA-based assaults amongst risk actors.
The Hancitor malware household and varied nation-state teams have integrated HTA recordsdata into their assault chains, leveraging the format’s skill to execute PowerShell instructions, obtain extra payloads, and set up persistent entry to compromised techniques.
The assault methodology extends past conventional webpage saving. Researchers have demonstrated that Information URIs containing HTML content material with textual content/html MIME varieties additionally bypass MOTW safety when saved by browsers.
This system permits attackers to embed malicious content material straight inside URLs, creating self-contained assault vectors that require no exterior internet hosting infrastructure.
The FileFix household represents a part of a broader evolution in social engineering techniques. The unique ClickFix approach, which methods customers into executing malicious PowerShell instructions disguised as troubleshooting steps, has spawned quite a few variants focusing on completely different working techniques and assault situations.
Safety researchers notice that ClickFix builders instruments that automate the creation of those assaults at the moment are actively bought in cybercriminal marketplaces.
This commoditization has lowered the barrier to entry for much less technically refined risk actors whereas rising the general quantity of assaults.
Cybersecurity professionals advocate a number of instant defensive actions. Organizations ought to take into account eradicating or limiting the mshta.exe executable that processes HTA recordsdata, although this may occasionally influence professional enterprise functions that depend on HTML Purposes.
Further protecting measures embrace implementing utility whitelisting, enhancing person schooling about social engineering techniques, and deploying endpoint detection techniques able to figuring out suspicious HTA execution patterns.
FileFix 2.0 represents a regarding evolution in social engineering assaults, demonstrating how risk actors proceed to seek out novel methods to bypass safety controls by inventive exploitation of professional system options.
Because the cybersecurity group grapples with AI-enhanced threats and more and more refined social engineering campaigns, this discovery underscores the crucial significance of defense-in-depth methods that handle each technical vulnerabilities and human elements in cybersecurity.
The intersection of professional browser performance with malicious intent creates assault vectors that problem conventional safety assumptions and require adaptive defensive approaches.
Examine reside malware habits, hint each step of an assault, and make quicker, smarter safety choices -> Attempt ANY.RUN now