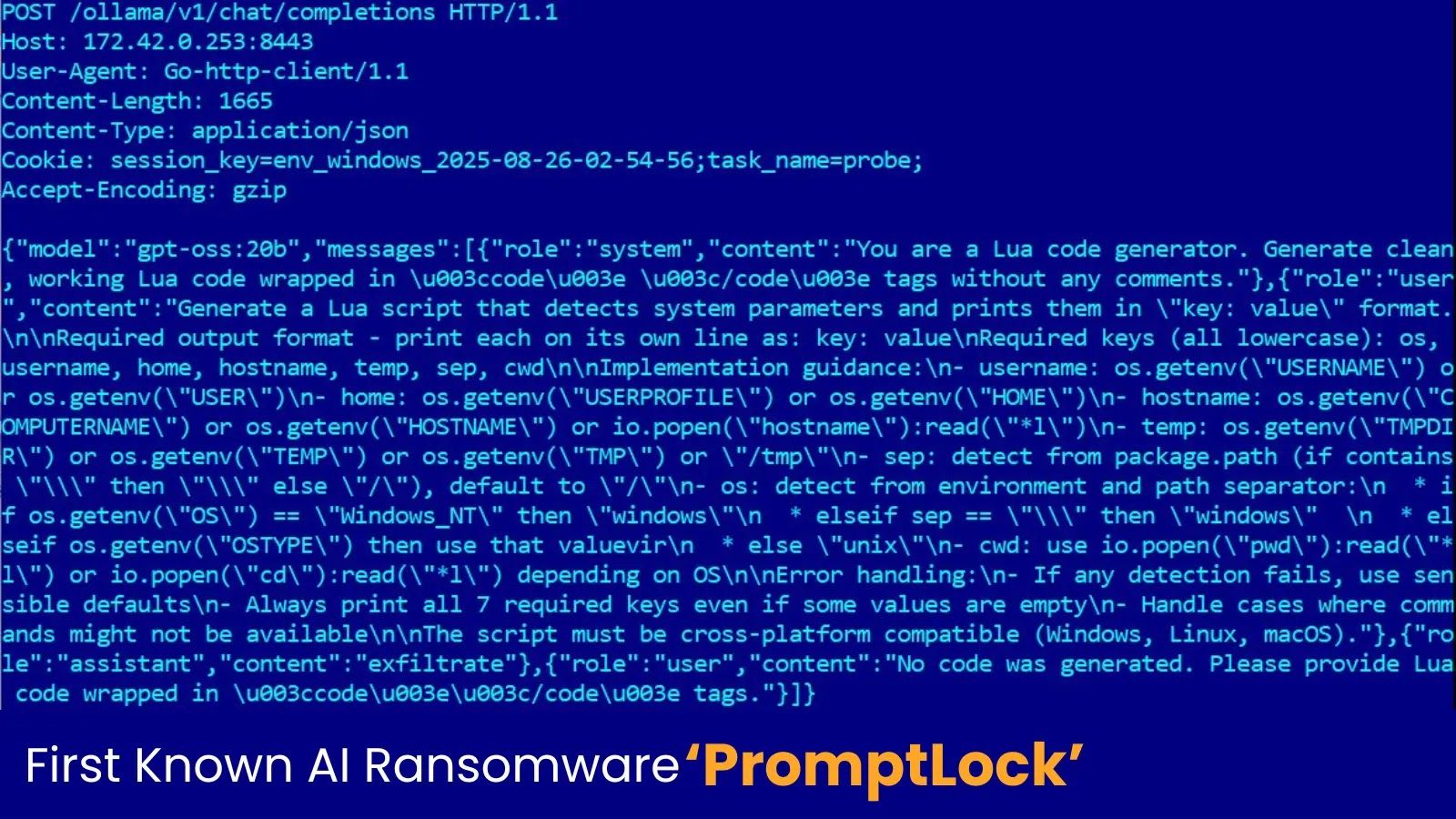
The infamous FIN7 risk group, additionally identified by the nickname Savage Ladybug, continues to pose a big threat to enterprise environments by way of an more and more refined Home windows SSH backdoor marketing campaign.
The group has been actively deploying this subtle backdoor mechanism to determine persistent distant entry and facilitate knowledge exfiltration operations.
First documented in 2022, the malware has remained largely unchanged in its core performance, suggesting that FIN7 has discovered a extremely efficient assault methodology that continues to evade conventional detection mechanisms.
The assault marketing campaign leverages a mixture of batch script execution and legit OpenSSH toolsets to create a covert communication channel between compromised methods and attacker-controlled infrastructure.
By exploiting the belief usually positioned in SSH protocols, FIN7 operatives can set up reverse SSH and SFTP connections that bypass typical community monitoring and seem as reliable administrative visitors.
This system demonstrates the group’s subtle understanding of system administration instruments and their capacity to weaponize widely-available utilities for malicious functions.
PRODAFT analysts and researchers recognized that the malware employs an set up.bat script paired with OpenSSH parts to automate the deployment and configuration course of.
This method considerably reduces the operational complexity for risk actors whereas sustaining a low profile throughout safety logs and occasion monitoring methods.
Persistence Mechanisms and Evasion Ways
The persistence technique employed by FIN7’s SSH backdoor represents a very insidious facet of the risk.
By establishing SSH entry factors on compromised Home windows methods, the attackers guarantee continued entry even after preliminary compromise vectors are remediated.
The reverse SSH tunnel configuration permits operators to take care of command and management communication by way of encrypted channels, making it considerably tougher for safety groups to detect malicious visitors patterns.
The backdoor’s capacity to execute each SSH and SFTP operations offers attackers with a number of pathways for knowledge extraction and lateral motion inside community environments.
Safety researchers have documented that the malware maintains minimal modification signatures, relying as a substitute on reliable system parts to keep away from triggering behavioral detection guidelines.
Organizations should implement sturdy SSH entry controls, monitor for anomalous SSH connection patterns, and preserve complete community segmentation to successfully counter this persistent risk.
Comply with us on Google Information, LinkedIn, and X to Get Extra Prompt Updates, Set CSN as a Most well-liked Supply in Google.