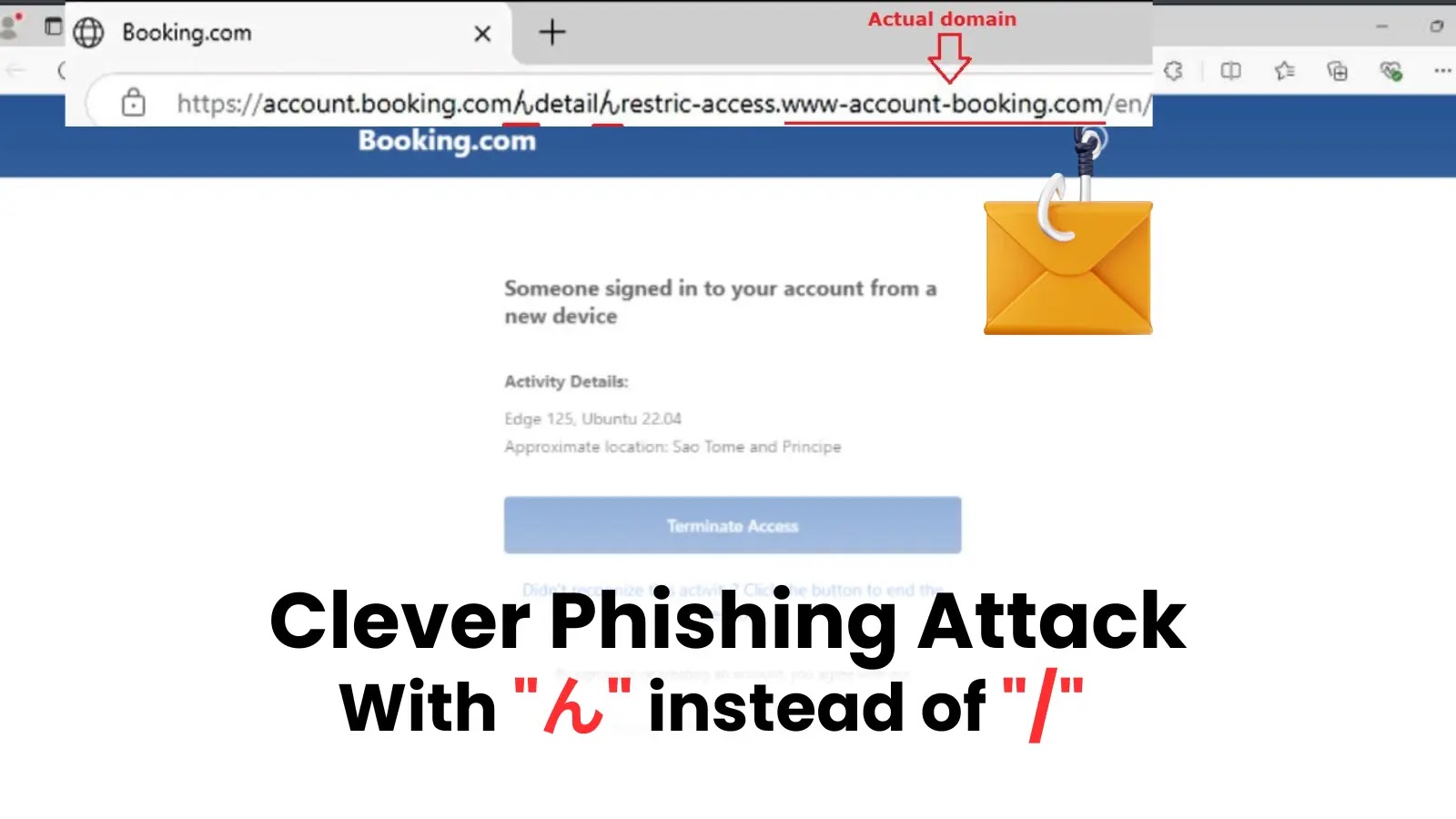
The digital frontlines of contemporary battle have expanded dramatically in 2025, with state-sponsored hackers from China, Russia, North Korea, and Iran executing refined assaults towards vitality grids, telecommunications networks, and transportation techniques worldwide.
These operations, usually masked as routine cybercrime, are reshaping nationwide safety paradigms whereas testing the resilience of democracies and allied partnerships.
China’s Strategic Prepositioning in U.S. Vital Programs
Beijing’s cyber operations have entered an aggressive new section, with the Volt Hurricane marketing campaign compromising U.S. vitality, water, and transportation networks since at the very least 2023.
By exploiting vulnerabilities in routers and IoT gadgets, Chinese language hackers established persistent entry to techniques controlling energy distribution in Hawaii and pipeline operations in Texas.
The marketing campaign’s aims grew to become extra obvious throughout a December 2024 U.S.-China summit, the place Beijing tacitly acknowledged the assaults as a warning towards American help for Taiwan.
Parallel operations by the Salt Hurricane group focused Cisco gadgets at vital telecom suppliers, together with Verizon and T-Cellular, enabling surveillance of communications between U.S. protection officers and Asian allies.
This two-pronged strategy—infrastructure sabotage and intelligence gathering—displays China’s doctrine of “profitable info wars” via coordinated digital dominance.
Russia’s Multi-Area Assault on Ukraine and NATO
Moscow’s cyber forces intensified their hybrid warfare techniques, launching 4,315 documented assaults towards Ukraine in 2024, a 70% surge from the earlier yr. Vital incidents included:
Disabling emergency communication techniques throughout missile strikes via malware-infected firmware updates
Compromising railway networks to disrupt army logistics by way of manipulated SCADA techniques
Exfiltrating protection plans from Ukrainian army servers utilizing AI-powered phishing lures
Russian-aligned hacktivists like NoName057(16) amplified these efforts, concentrating on European vitality companies and monetary establishments supplying Kyiv assist.
A February 2025 assault on Poland’s gasoline pipeline operator compelled guide overrides at 17 pumping stations, inflicting non permanent gasoline shortages in Germany.
North Korea’s AI-Pushed Monetary Warfare
Pyongyang’s newly established Analysis Centre 227 has weaponized machine studying to automate cryptocurrency theft and significant infrastructure penetration.
The unit’s algorithms analyzed 58 historic assaults to develop adaptive ransomware strains, netting over $200 million in 2024 from Japanese and South Korean exchanges. Strategic targets included:
AI-controlled good grids in Seoul, bypassing conventional intrusion detection via behavioral mimicry
Shipbuilding CAD techniques in Busan, exfiltrating labeled designs for submarine parts
Agricultural IoT networks, manipulating fertilizer distribution algorithms to create synthetic shortages
This technical evolution enhances North Korea’s standard cyber espionage, with compromised South Korean protection contractors offering blueprints for missile steering techniques.
Iran’s Persistent Vital Infrastructure Penetration
Tehran’s Lemon Sandstorm group demonstrated unprecedented persistence in a 22-month marketing campaign towards Center Japanese water remedy crops and oil refineries. By exploiting unpatched Fortinet VPN vulnerabilities, hackers gained management of:
Chlorination techniques at a Saudi desalination plant
Stress valves alongside the Iraq-Turkey pipeline
SCADA controllers for the UAE’s Barakah nuclear facility
The group’s Dwelling-Off-the-Land techniques, utilizing reliable admin instruments for lateral motion, allowed undetected community residency, enabling each real-time surveillance and dormant assault capabilities.
World Responses and Mitigation Methods
Nations are adopting multi-layered protection frameworks to counter these threats:
Air-Hole Reinforcement: The U.S. DOE mandated bodily isolation of all nuclear plant management techniques by Q3 2025, reversing earlier IT/OT convergence insurance policies.
AI-Powered Anomaly Detection: South Korea’s NIS deployed neural networks analyzing 12 billion each day community occasions, decreasing incident response time to eight.7 seconds.
Cross-Border Risk Intel Sharing: The 5 Eyes Alliance established a real-time malware fingerprint database, correlating 17,000 state-sponsored assault signatures.
Vital Infrastructure Stress Checks: EU regulators performed war-game simulations at 438 energy crops, exposing vulnerabilities in 63% of legacy PLC techniques.
As Forescout’s 2025 World Risk Report warns, 90% of disruptive assaults now originate from state-aligned teams masking operations as hacktivism or ransomware campaigns.
This obfuscation challenges conventional guidelines of engagement, with the U.S. Cyber Command lately authorizing preemptive counter-hacks towards international infrastructure internet hosting assault infrastructure.
The worldwide group faces a pivotal selection: escalate defensive cyber capabilities via AI and quantum-resistant encryption or threat cascading failures in interconnected crucial techniques.
Assaults on industrial management techniques have elevated by 214% since 2023, narrowing the window for coordinated motion. As digital and bodily battlefields converge, the subsequent main battle could also be determined not by troops or tanks however by silent, persistent traces of malicious code.
Discover this Information Attention-grabbing! Comply with us on Google Information, LinkedIn, & X to Get On the spot Updates!