A crucial safety vulnerability in Google’s account restoration system allowed malicious actors to acquire the telephone numbers of any Google person by way of a complicated brute-force assault, in accordance with a disclosure by a BruteCat safety researcher revealed this week.
The vulnerability, which has since been patched, exploited Google’s No-JavaScript username restoration kind to bypass safety protections and extract delicate private data.
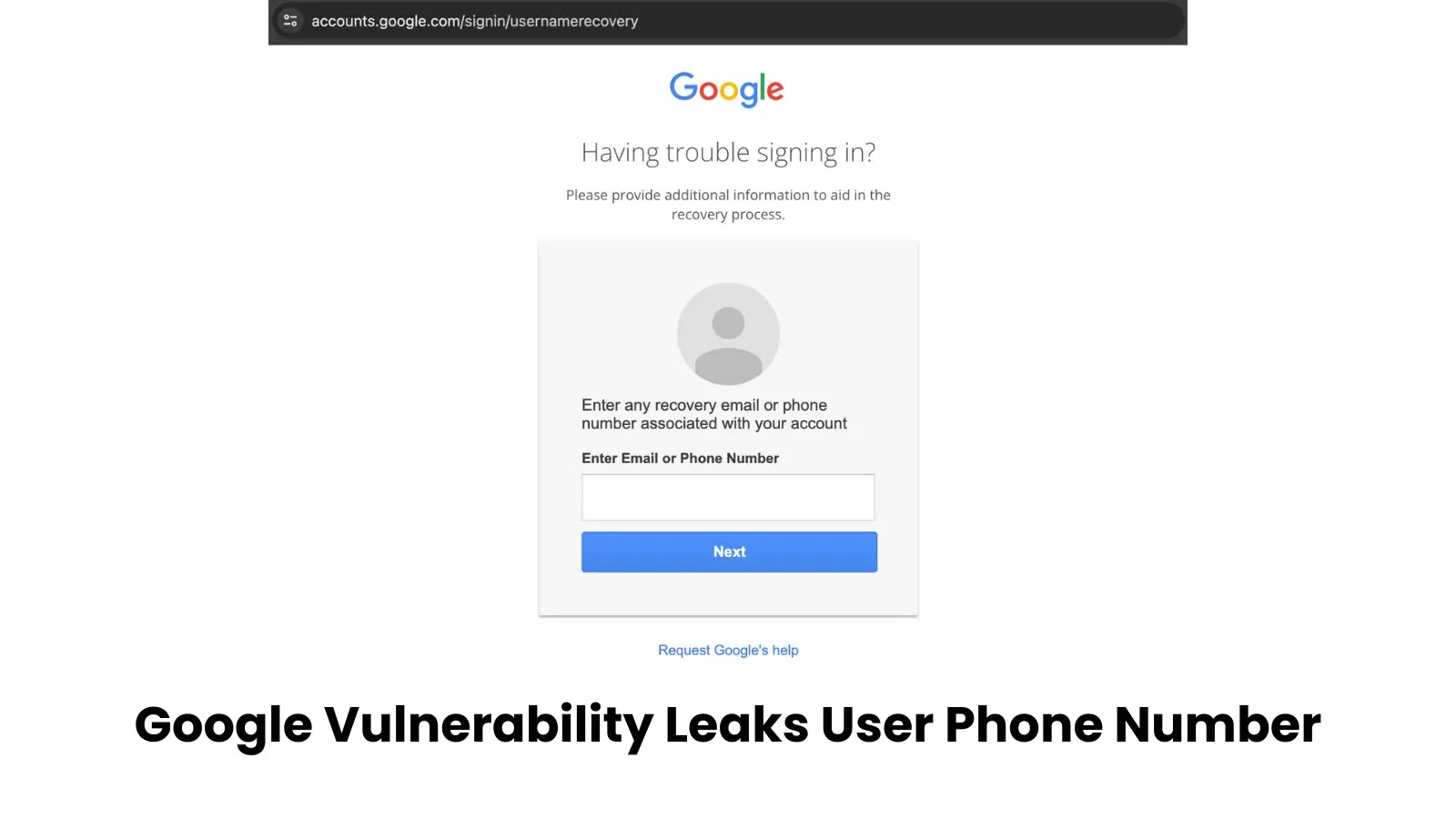
The vulnerability centered on Google’s legacy username restoration system that functioned with out JavaScript enabled. A safety researcher found that this forgotten endpoint might be manipulated to confirm whether or not particular telephone numbers have been related to specific show names, creating a chance for systematic telephone quantity enumeration.
Account restoration
The assault methodology concerned three key steps: first, acquiring a goal’s Google account show identify by way of Looker Studio by transferring doc possession, which might leak the sufferer’s identify with none interplay required.
Second, initiating Google’s forgot password movement to retrieve a masked telephone quantity trace, displaying solely the previous couple of digits. Lastly, utilizing a custom-built device known as “gpb” to brute-force the whole telephone quantity by testing mixtures in opposition to the identified show identify, reads the BruteCat report.
Vulnerability Leaks Customers’ Telephone Numbers
The researcher overcame Google’s rate-limiting protections by way of intelligent technical workarounds. By using IPv6 handle ranges offering over 18 quintillion distinctive IP addresses, the assault might rotate by way of totally different addresses for every request, successfully bypassing Google’s anti-abuse mechanisms.
Moreover, the researcher found that botguard tokens from JavaScript-enabled kinds might be repurposed for the No-JS model, eliminating captcha challenges that may in any other case stop automated assaults.
The assault proved remarkably environment friendly, with the researcher reaching roughly 40,000 verification makes an attempt per second utilizing a modest $0.30/hour server.
Relying on the nation code, full telephone numbers might be extracted in timeframes starting from mere seconds for smaller nations like Singapore to round 20 minutes for the US.
Google was notified of the vulnerability on April 14, 2025, and responded rapidly by implementing non permanent mitigations whereas working towards a everlasting resolution.
The corporate absolutely deprecated the susceptible No-JS username restoration kind by June 6, 2025, successfully eliminating the assault vector.
Google acknowledged the severity of the invention, initially awarding $1,337 earlier than rising the bounty to $5,000 after the researcher appealed, citing the assault’s lack of stipulations and undetectable nature.
This incident highlights the continuing safety challenges posed by legacy techniques and the significance of complete safety audits throughout all service endpoints, even these seemingly out of date or hardly ever used.
Velocity up and enrich risk investigations with Menace Intelligence Lookup! -> 50 trial search requests