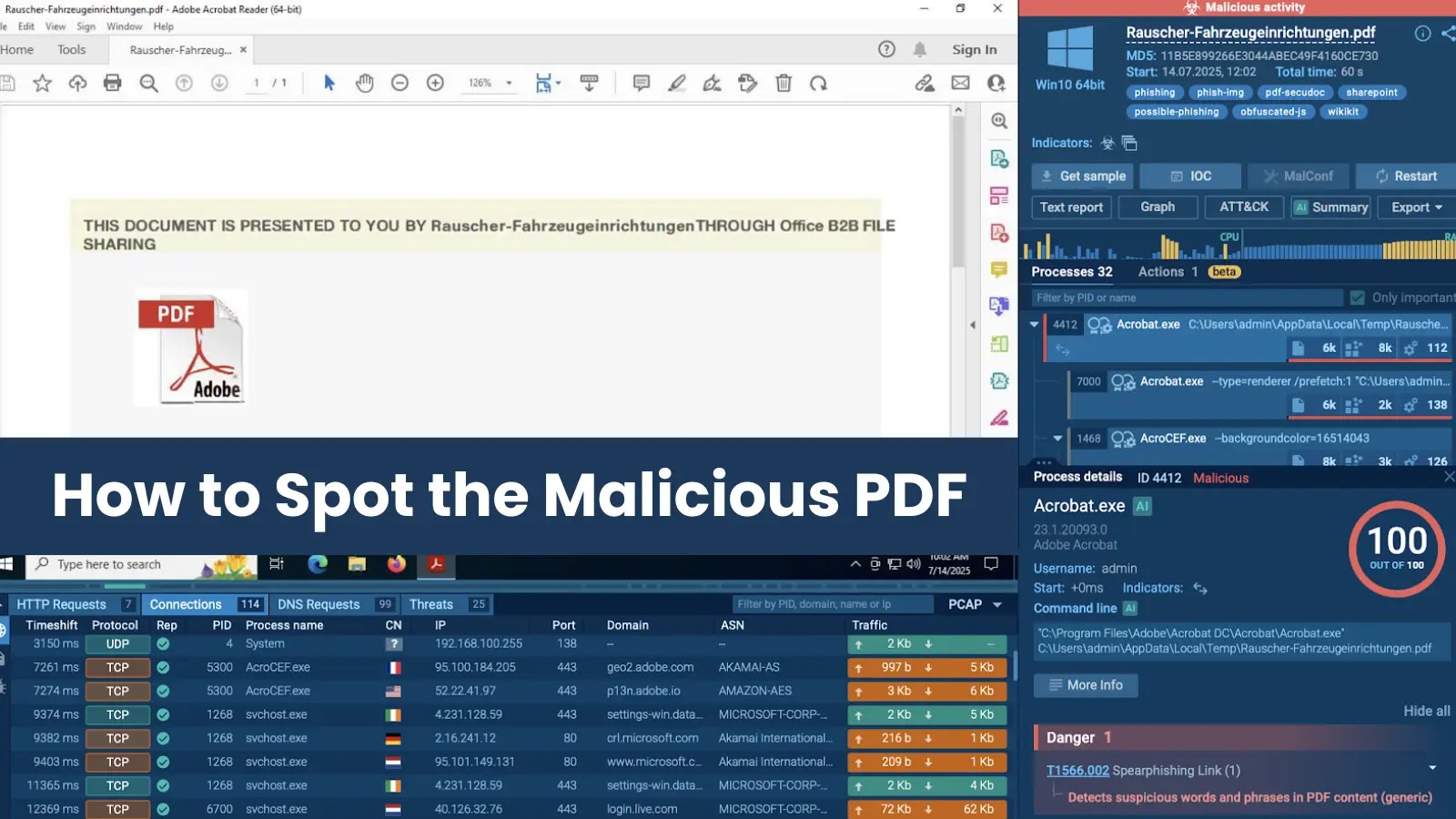
Google has confirmed that certainly one of its company Salesforce situations was compromised in June by the risk group tracked as UNC6040.
This incident is a part of a Salesforce assault marketing campaign involving voice phishing assaults geared toward stealing delicate knowledge from organizations’ Salesforce environments, adopted by extortion calls for.
The breach highlights the rising dangers of social engineering techniques concentrating on cloud platforms, with attackers impersonating IT assist to achieve unauthorized entry.
Based on Google’s Risk Intelligence Group (GTIG), the intrusion occurred by way of comparable strategies noticed in different UNC6040 operations.
In Google’s case, the impacted occasion saved contact info and notes for small and medium companies. GTIG’s evaluation confirmed that the risk actors retrieved knowledge throughout a short window earlier than entry was revoked.
Luckily, the exfiltrated info was restricted to primary, largely publicly out there particulars like enterprise names and speak to particulars. Google swiftly responded by reducing off entry, conducting an impression evaluation, and implementing mitigations.
UNC6040 Vishing Ways
This occasion highlights UNC6040’s altering techniques. Initially counting on Salesforce’s Information Loader, the group has transitioned to customized Python scripts that replicate its capabilities.
UNC6040 hackers provoke assaults with voice calls by way of Mullvad VPN or TOR networks, automating knowledge assortment afterward. GTIG notes that attackers have moved from creating trial accounts with webmail to utilizing compromised accounts from unrelated organizations to register malicious apps.
This adaptation complicates monitoring and attribution, making it more durable for safety groups to detect and reply.
Extortion performs a key function in UNC6040’s playbook. After knowledge theft, which may happen months prior, victims obtain calls for for Bitcoin funds inside 72 hours, usually by way of emails from addresses like shinycorp@tuta[.]com or shinygroup@tuta[.]com.
The actors falsely declare affiliation with the infamous ShinyHunters group to intensify stress. GTIG warns that these risk actors might quickly launch an information leak website to escalate techniques, doubtlessly exposing stolen knowledge from latest breaches, together with these tied to Salesforce hacks.
The marketing campaign’s infrastructure overlaps with components linked to “The Com,” a loosely organized collective identified for comparable social engineering ploys. UNC6040 targets English-speaking workers in multinational companies, exploiting their belief in IT assist calls to reap credentials and entry platforms like Okta and Microsoft 365.
In some intrusions, attackers have custom-made instruments with names like “My Ticket Portal” to align with their phishing pretexts, demonstrating a excessive degree of sophistication.
GTIG emphasizes that these assaults exploit human vulnerabilities reasonably than Salesforce flaws. No inherent platform weaknesses have been concerned; as a substitute, success stems from convincing customers to grant entry. This development indicators a shift towards concentrating on IT personnel as entry factors for knowledge exfiltration.
To fight such threats, consultants advocate strong defenses. Organizations ought to implement the precept of least privilege, limiting permissions for instruments like Information Loader. Rigorous administration of related apps, IP-based entry restrictions, and common multi-factor authentication (MFA) is essential.
Superior monitoring by way of Salesforce Defend can detect anomalies like massive knowledge downloads. Common audits and person coaching on vishing techniques are important to forestall MFA fatigue and credential sharing.
Equip your SOC with full entry to the newest risk knowledge from ANY.RUN TI Lookup that may Enhance incident response -> Get 14-day Free Trial