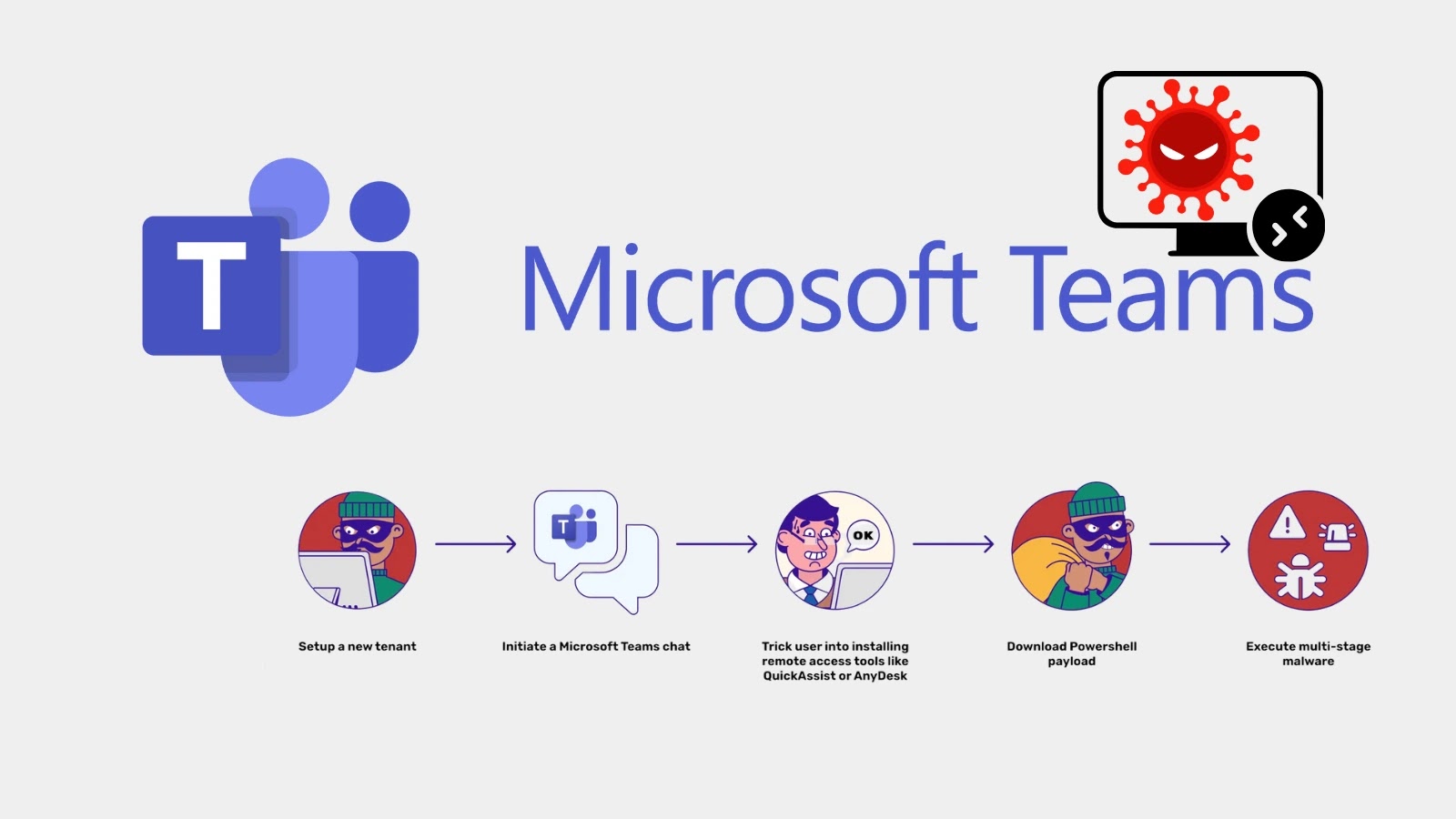
Cybercriminals are more and more weaponizing Microsoft Groups, exploiting the platform’s trusted position in company communications to deploy malware and seize management of sufferer programs.
In a classy marketing campaign, risk actors are impersonating IT assist employees in Microsoft Groups chats to trick staff into granting distant entry, marking a harmful evolution from conventional email-based phishing assaults.
Social engineering stays a extremely efficient tactic for hackers, and as companies have built-in platforms like Microsoft Groups into their core operations, attackers have adopted. The inherent belief staff place in inner messaging makes it a fertile floor for deception.
Current campaigns analyzed by Permiso cybersecurity researchers reveal a multi-stage assault that begins with a easy message and culminates within the deployment of potent, multifunctional malware.
PowerShell-based Malware through Microsoft Groups
The assault chain typically begins with a direct message or name from a newly created or compromised Microsoft Groups account. These accounts are designed to look reputable, utilizing show names like “IT SUPPORT ✅” or “Assist Desk Specialist” to impersonate trusted personnel.
Microsoft crew Assault Chain
Attackers typically use checkmark emojis to simulate a verified standing and leverage Microsoft’s onmicrosoft.com area construction to seem as if they’re a part of the group.
Posing as IT employees addressing a routine problem like system upkeep, the attackers construct rapport with their goal.
As soon as belief is established, they persuade the worker to put in distant entry software program, similar to QuickAssist or AnyDesk, beneath the guise of offering technical help. This vital step provides the attacker a direct foothold into the consumer’s machine and the company community.
Whereas comparable methods involving distant entry instruments have been linked to ransomware teams like BlackBasta since mid-2024, these newer campaigns are extra direct, typically forgoing the preliminary mass e-mail campaigns seen up to now.
The malicious payloads have additionally diversified, with current incidents involving the DarkGate and Matanbuchus malware loaders.
As soon as distant entry is secured, the attacker executes a PowerShell command to obtain the first malicious payload. This script is much from easy, outfitted with capabilities for credential theft, establishing long-term persistence, and distant code execution, Permiso mentioned.
To evade detection and complicate elimination, the malware can designate its personal course of as “vital,” which might trigger the system to crash if terminated.
It additionally makes use of a legitimate-looking Home windows credential immediate to trick customers into coming into their passwords, that are then exfiltrated to an attacker-controlled server.
Evaluation of the payload’s code revealed hardcoded encryption keys that hyperlink the marketing campaign to a recognized financially motivated risk actor tracked as Water Gamayun (also referred to as EncryptHub).
This group has a historical past of mixing refined social engineering with customized malware to focus on English-speaking IT professionals and builders.
Workers have to be skilled to stay vigilant in opposition to unsolicited contact, even on trusted inner platforms. All requests for credentials or the set up of distant entry software program ought to be independently verified by means of a recognized, separate communication channel.
OHere is a desk of the Indicators of Compromise (IoCs) based mostly on the offered data.
IndicatorTypehttps://audiorealteak[.]com/payload/construct.ps1URLhttps://cjhsbam[.]com/payload/runner.ps1URL104.21.40[.]219IPv4193.5.65[.]199IPv4Mozilla/5.0 (Home windows NT; Home windows NT 10.0; en-US) AppleWebKit/534.6 (KHTML, like Gecko) Chrome/7.0.500.0 Safari/534.6User Agent (UA)&9*zS7LYpercentZN1thfIInitialization Vector123456789012345678901234r0hollahEncryption Key62088a7b-ae9f-2333-77a-6e9c921cb48eMutexHelp Desk Specialist ✅Person Show NameIT SUPPORT✅Person Show NameMarco DaSilva IT Assist ✅Person Show NameIT SUPPORT ✅Person Show NameHelp DeskUser Show [email protected][.]comUser Principal [email protected][.]comUser Principal [email protected][.]comUser Principal [email protected][.]comUser Principal [email protected][.]comUser Principal [email protected][.]comUser Principal [email protected][.]comUser Principal Identify
As risk actors proceed to innovate, a defense-in-depth technique, combining technical controls with strong consumer training, is crucial to guard in opposition to assaults that flip collaboration instruments into conduits for compromise.
Discover this Story Attention-grabbing! Observe us on LinkedIn and X to Get Extra Prompt Updates.