A complicated new breed of ransomware assaults is leveraging respectable database instructions to compromise organizations worldwide, bypassing conventional safety measures by “malware-less” operations.
Not like typical ransomware that encrypts recordsdata utilizing malicious binaries, menace actors are exploiting uncovered database providers by abusing normal database performance to steal, wipe, and ransom crucial information.
The assault methodology represents a major evolution in cybercriminal techniques, with attackers focusing on Web-facing database servers configured with weak passwords or no authentication.
This malicious exercise has been noticed throughout a number of database platforms, together with MySQL, PostgreSQL, MongoDB, Hadoop, CouchDB, and Elasticsearch. Attackers join remotely to those servers, copy information to exterior places, execute damaging instructions to wipe databases, and depart ransom notes saved immediately inside the compromised database constructions.
This method has confirmed significantly efficient at evading detection as a result of no malicious binary is ever deployed on the goal system.
The injury is achieved solely by respectable database instructions, making it troublesome for typical endpoint safety options to determine the compromise.
The ransom tactic has advanced from remoted incidents into full-scale automated campaigns, with specialised bots constantly scanning the Web for misconfigured databases.
Wiz.io researchers recognized that these assaults have grown exponentially since their preliminary statement in February 2017, when researchers from Rapid7 first documented 1000’s of open databases being hijacked in bulk operations.
At this time’s menace actors function subtle automated methods able to compromising newly uncovered targets inside hours or minutes of them coming on-line.
The benefit of automation and potential for fast earnings has made malware-less database ransomware a persistent and rising menace to organizations globally.
Assault Execution and Command Exploitation
The technical execution of those assaults follows a methodical method that maximizes each stealth and effectiveness.
Attackers start operations with Web-wide scanning for uncovered database ports, particularly focusing on port 3306 for MySQL and port 5432 for PostgreSQL servers.
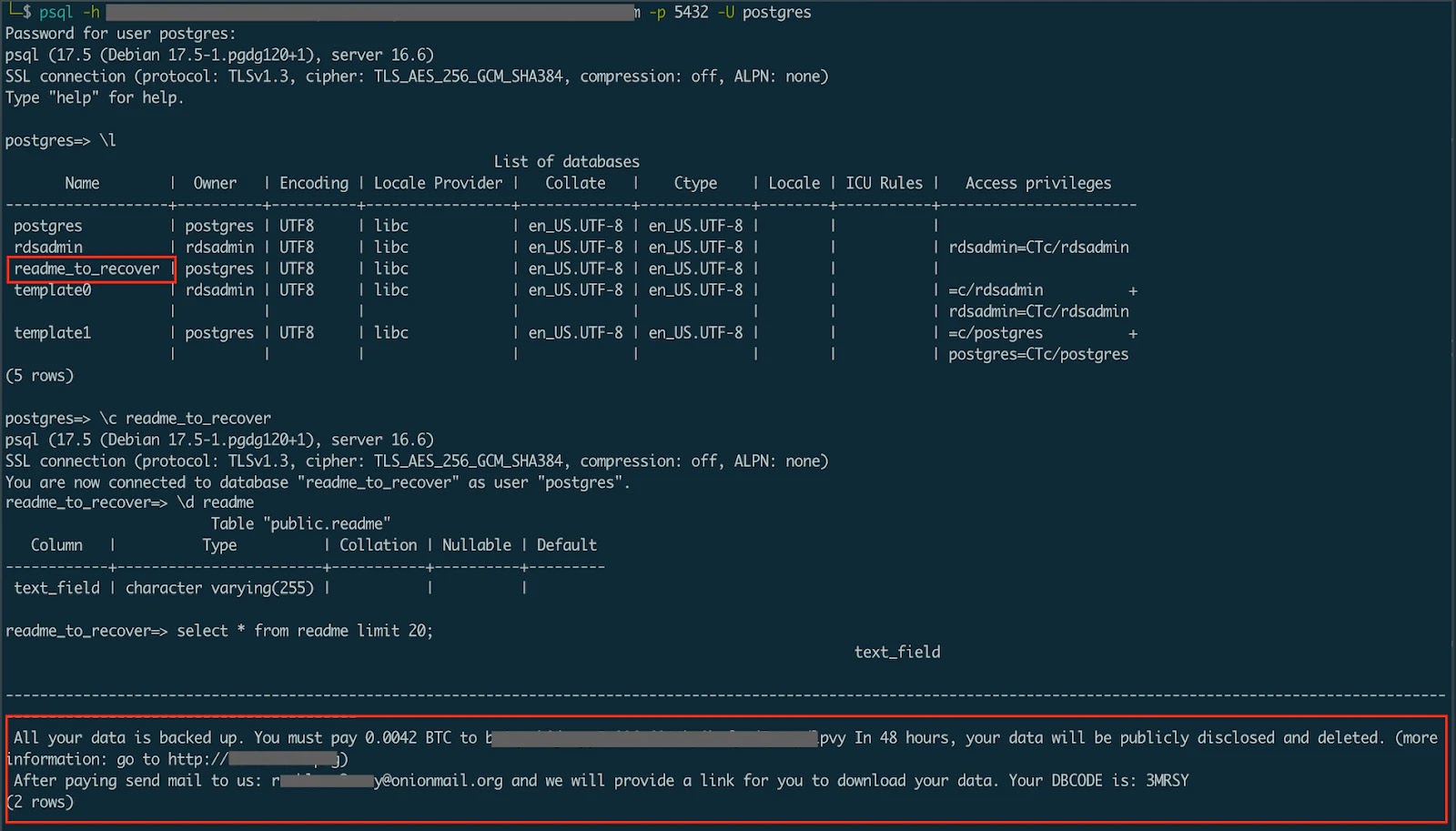
Ransom observe (Supply – Wiz.io)
As soon as potential targets are recognized, they make use of fingerprinting strategies to substantiate the providers are real database servers quite than honeypots or different decoy methods.
Authentication bypass represents a crucial part the place attackers take a look at for lacking authentication controls, try default username and password mixtures, and execute brute-force assaults towards weak credentials.
Upon profitable authentication, the assault proceeds with information extraction the place attackers pattern small parts of knowledge to evaluate worth and make sure database entry.
The damaging part makes use of respectable SQL instructions comparable to DROP DATABASE for full database elimination or bulk DELETE operations to systematically erase information.
In relational databases like PostgreSQL, attackers create new tables with names comparable to RECOVER_YOUR_DATA or README_TO_RECOVER and insert ransom notes as desk rows.
For NoSQL databases like MongoDB, the method includes creating new collections with indicative names and inserting ransom notes as paperwork.
A captured MongoDB session demonstrates the assault development: mongosh “mongodb://goal:27017/” adopted by database enumeration instructions like present dbs to determine worthwhile targets.
The ransom observe insertion sometimes incorporates messages comparable to “All of your information is backed up. You need to pay 0.043 BTC to recuperate it.
After 48 hours expiration we’ll leak and expose all of your information.” These respectable database operations make detection difficult, because the instructions seem as regular administrative actions to monitoring methods.
Comply with us on Google Information, LinkedIn, and X to Get Extra Immediate Updates, Set CSN as a Most popular Supply in Google.