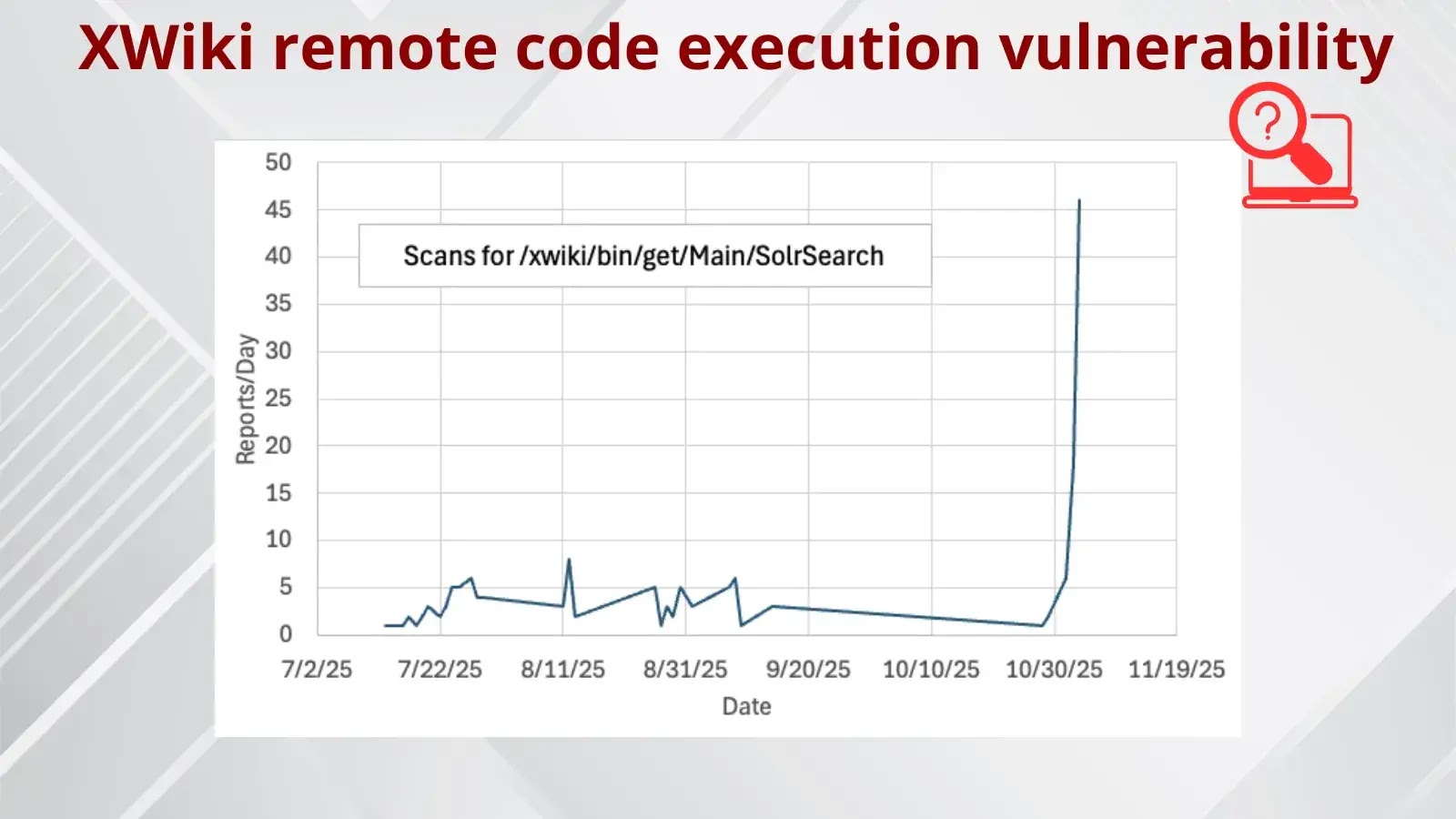
A important distant code execution vulnerability affecting XWiki’s SolrSearch part has grow to be the goal of widespread exploitation makes an attempt, prompting cybersecurity authorities so as to add it to their watchlist.
The flaw permits attackers with minimal visitor privileges to execute arbitrary instructions on susceptible programs, posing a big safety danger to organizations utilizing this open-source enterprise wiki platform.
XWiki, which positions itself as a sophisticated open-source enterprise wiki and various to platforms like Confluence and MediaWiki, launched a safety advisory and patch in February addressing this extreme vulnerability.
The flaw resides within the SolrSearch part and remarkably requires solely guest-level privileges for exploitation, making it accessible to nearly any consumer with fundamental system entry.
Vulnerability Discovery and Delayed Exploitation
The early launch of proof-of-concept code alongside the advisory meant that the vulnerability skilled an unusually delayed exploitation timeline. Preliminary reconnaissance scans appeared in July, however precise exploitation makes an attempt didn’t surge till just lately.
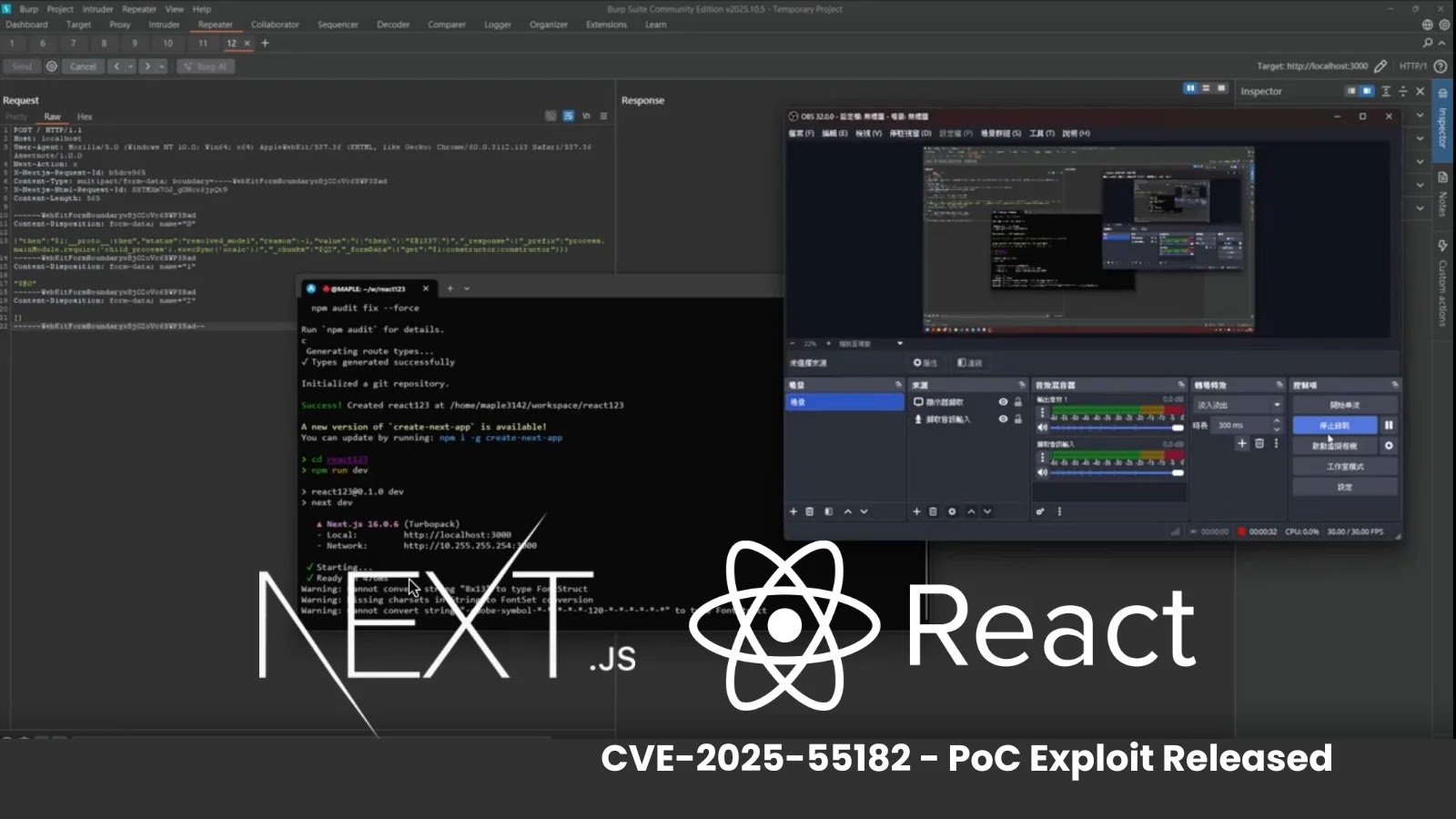
The exploitation technique demonstrates comparatively easy execution patterns. Attackers ship specifically crafted GET requests to the susceptible XWiki endpoint, particularly concentrating on the SolrSearch RSS media operate.
SANS noticed that the malicious requests embed Groovy script instructions inside asynchronous execution blocks, permitting distant code execution via shell instructions.
Captured exploit makes an attempt reveal attackers making an attempt to obtain and execute shell scripts from exterior servers, particularly from the IP tackle 74.194.191.52.
The Person-Agent string in these requests incorporates the e-mail tackle [email protected], doubtlessly belonging to the risk actor.
Investigation of the internet hosting server uncovered an sudden connection to Chicago rap tradition, with references to captivity rapper King Lil Jay and rival RondoNumbaNine, each beforehand related to opposing gang affiliations.
The vulnerability presents important dangers as a result of it permits full system compromise via distant code execution capabilities. Organizations operating XWiki installations should prioritize fast patching to stop potential breaches.
The assault requires no consumer interplay and minimal complexity, making it significantly engaging to opportunistic risk actors conducting mass web scanning campaigns.
Safety groups ought to confirm their XWiki installations are up to date with the February safety patch, monitor for suspicious SolrSearch requests, and implement network-level protections to detect exploitation makes an attempt.
The mix of low assault complexity and widespread scanning exercise signifies this vulnerability will stay a high-priority goal for malicious actors.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.