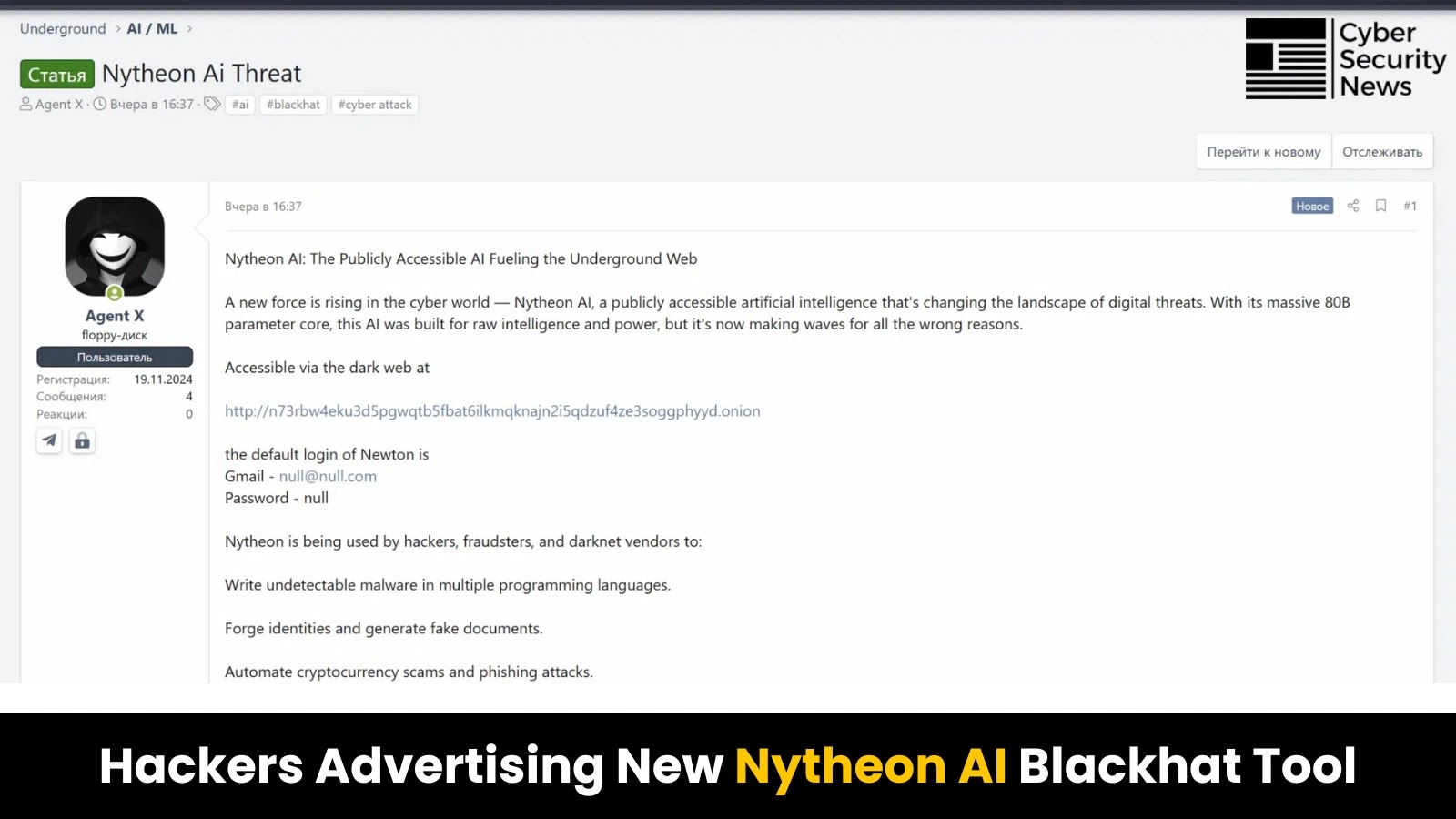
A classy new risk platform, Nytheon AI, has emerged, which mixes a number of uncensored giant language fashions (LLMs) constructed particularly for malicious actions.
The platform, found by Cato CTRL, is being actively promoted on fashionable hacking boards, together with XSS and numerous Telegram channels, representing a major evolution in how risk actors are leveraging synthetic intelligence for cybercriminal operations.
Darkish Net Platform Provides Built-in AI Instruments
The Nytheon AI platform operates completely on the Tor community, offering risk actors with a complete suite of AI-powered instruments.
In contrast to earlier single-model choices akin to WormGPT, BlackHatGPT, and FraudGPT, Nytheon AI presents an built-in ecosystem of specialised fashions designed for various assault vectors.
Nytheon AI webpage
The platform contains Nytheon Coder and Nytheon Coder R1 for code era, Nytheon GMA for doc summarization and translation, Nytheon Imaginative and prescient for image-to-text recognition, and Nytheon AI as a management mannequin.
Every mannequin, besides the management model, shares an equivalent 1,000-token system immediate that intentionally disables security layers and mandates compliance with unlawful requests, guaranteeing speedy manufacturing of malicious content material with out requiring exterior jailbreaking strategies.
Nytheon AI person interface
The technical sophistication behind Nytheon AI distinguishes it from typical darkish internet choices. The platform makes use of a contemporary SvelteKit SPA (Single Web page Software) with TypeScript and Vite on the frontend, speaking with a FastAPI-style backend.
The structure contains modular .svelte parts akin to AddServerModal.svelte and NotificationToast.svelte, whereas Net Employees like KooreoWorker.ts deal with intensive client-side duties together with file processing.
The backend infrastructure operates via a number of microservices accessible through REST endpoints: /ollama for native mannequin server operations utilizing GGUF (GPT-Generated Unified Format) weights, /openai for upstream OpenAI-compatible endpoints, and specialised companies at /api/v1/audio, /photos, and /retrieval for speech-to-text, picture era, and RAG (Retrieval-Augmented Era) search capabilities.
Latest platform updates have launched multimodal ingestion capabilities with Mistral OCR integration, Azure AI Speech-to-Textual content performance, and OpenAPI specification parsing that enables customers to combine exterior APIs immediately into the chat interface.
This permits risk actors to each generate malicious content material and execute assaults via software calls inside a single interface.
Investigators have recognized sturdy indicators pointing to Russian-speaking operators behind the platform.
Evaluation of demonstration movies revealed a Russian-language film poster for “Зелёный паук” (“The Inexperienced Spider”), a Soviet-era movie, whereas direct communication with platform operators confirmed the usage of post-Soviet dialect patterns.
The platform’s promotion on XSS, a well-liked Russian hacking discussion board, additional helps this evaluation.
Nytheon AI reveals itself on XSS
The platform’s fast growth cycle, with five-point releases spanning 9 days, demonstrates lively ongoing growth whereas probably introducing exploitable vulnerabilities.
This represents a regarding evolution in cybercriminal infrastructure, transferring past easy uncensored chatbots to complete GenAI-as-a-service operations able to supporting subtle assault campaigns together with spear-phishing, polymorphic malware era, and deepfake doc creation.
Automate risk response with ANY.RUN’s TI Feeds—Enrich alerts and block malicious IPs throughout all endpoints -> Request full entry