A risk actor often called “888” has purportedly dumped delicate information stolen from electronics big LG Electronics, elevating alarms within the cybersecurity neighborhood.
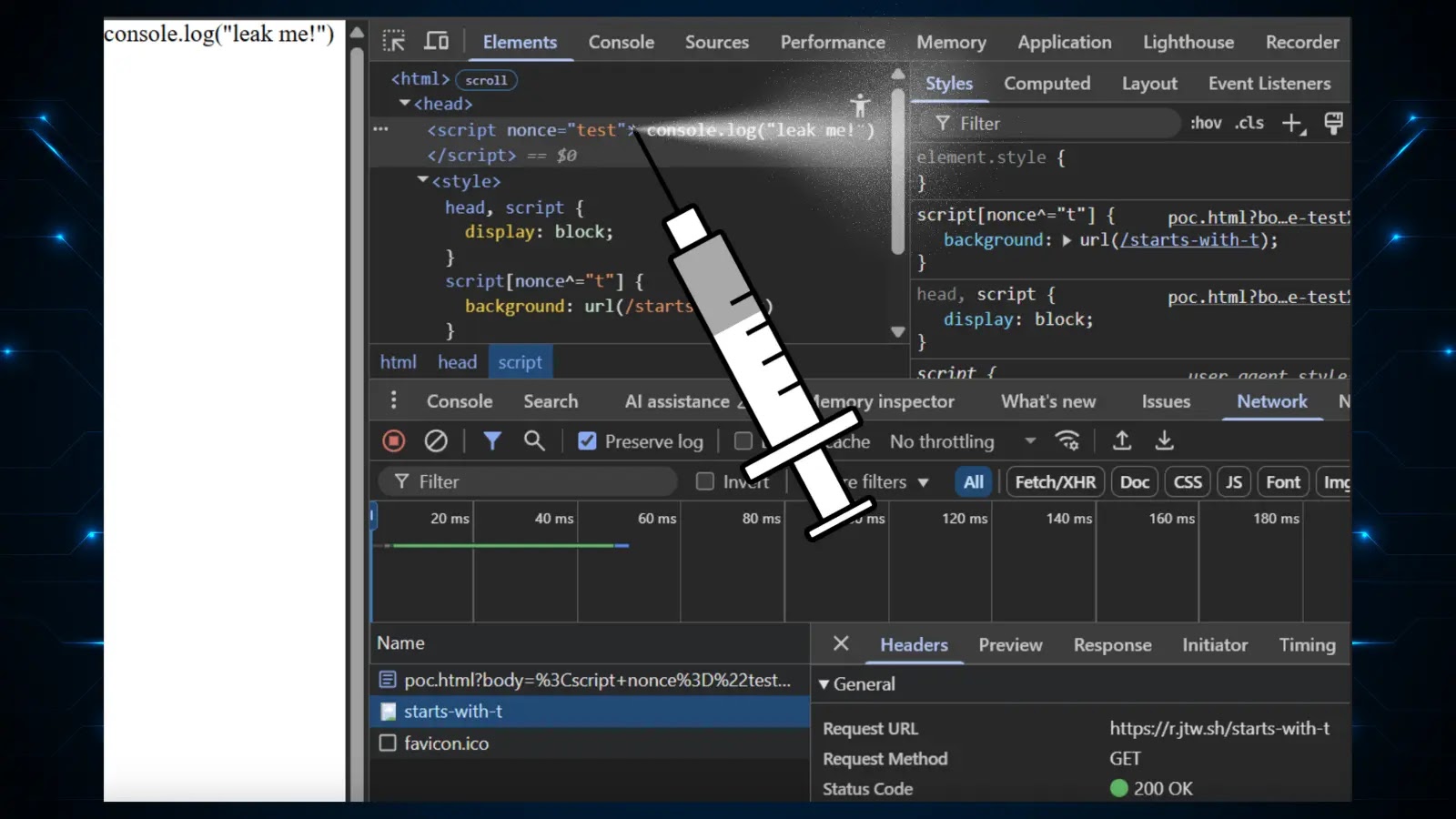
The breach, first spotlighted on November 16, 2025, allegedly contains supply code repositories, configuration recordsdata, SQL databases, and, critically, hardcoded credentials and SMTP server particulars probably exposing LG’s inner communications and growth pipelines to widespread exploitation.
The leak surfaced by way of a submit on ThreatMon, a platform that tracks darkish net exercise, the place “888” shared samples to show authenticity. Described as originating from a contractor entry level, the dataset reportedly spans a number of LG techniques, hinting at a provide chain vulnerability relatively than a direct company hack.
LG Information Leak Declare
Cybersecurity analysts observe that hardcoded credentials embedded instantly in code for comfort pose extreme dangers, as they may allow attackers to impersonate LG personnel or pivot to linked providers.
SMTP credentials, which handle e-mail routing, may additional enable phishing campaigns or spam operations disguised as respectable LG correspondence.
Menace actor “888” is not any stranger to high-profile claims. Energetic since a minimum of 2024, this particular person has focused entities like Microsoft, BMW Hong Kong, Decathlon, and Shell, usually extorting ransoms or promoting information on breach boards.
Their techniques sometimes contain preliminary entry brokers and infostealer malware, and so they monetize leaks by cryptocurrency funds. On this LG incident, no ransom demand has been publicly confirmed.
Nonetheless, samples shared embody file buildings suggesting the presence of gigabytes of proprietary code, which may undermine LG’s mental property in shopper electronics and good home equipment.
LG Electronics has but to challenge an official assertion, however the timing aligns with a turbulent yr for the corporate. Earlier in October 2025, LG’s telecom arm, LG Uplus, confirmed a separate breach affecting buyer information, amid a wave of South Korean telecom hacks.
Specialists speculate these incidents might share widespread vectors, akin to unpatched vulnerabilities in cloud integrations or third-party instruments. The publicity of supply code may reveal flaws in LG’s IoT gadgets, amplifying dangers for thousands and thousands of customers worldwide.
As investigations unfold, safety corporations urge organizations to scan for leaked credentials utilizing instruments like Have I Been Pwned and to rotate all suspected keys instantly.
This alleged breach underscores the fragility of worldwide provide chains, the place a single contractor’s lapse can cascade into company espionage. For LG, swift disclosure and remediation shall be key to mitigating fallout amid relentless cyber threats.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to function your tales.