Crucial vulnerabilities in Microsoft Groups, a platform central to office communication for over 320 million customers worldwide, allow attackers to impersonate executives and tamper with messages undetected.
These vulnerabilities, now patched by Microsoft, allowed each exterior company and insiders to spoof identities in chats, notifications, and calls, probably resulting in fraud, malware distribution, and misinformation.
Test Level disclosed the difficulty to Microsoft responsibly in March 2024. The problems spotlight how belief in collaboration instruments may be weaponized by refined risk actors concentrating on distant work infrastructure.
Launched in 2017 as a part of Microsoft 365, Groups integrates chat, video calls, file sharing, and apps, making it indispensable for companies from startups to Fortune 500 corporations.
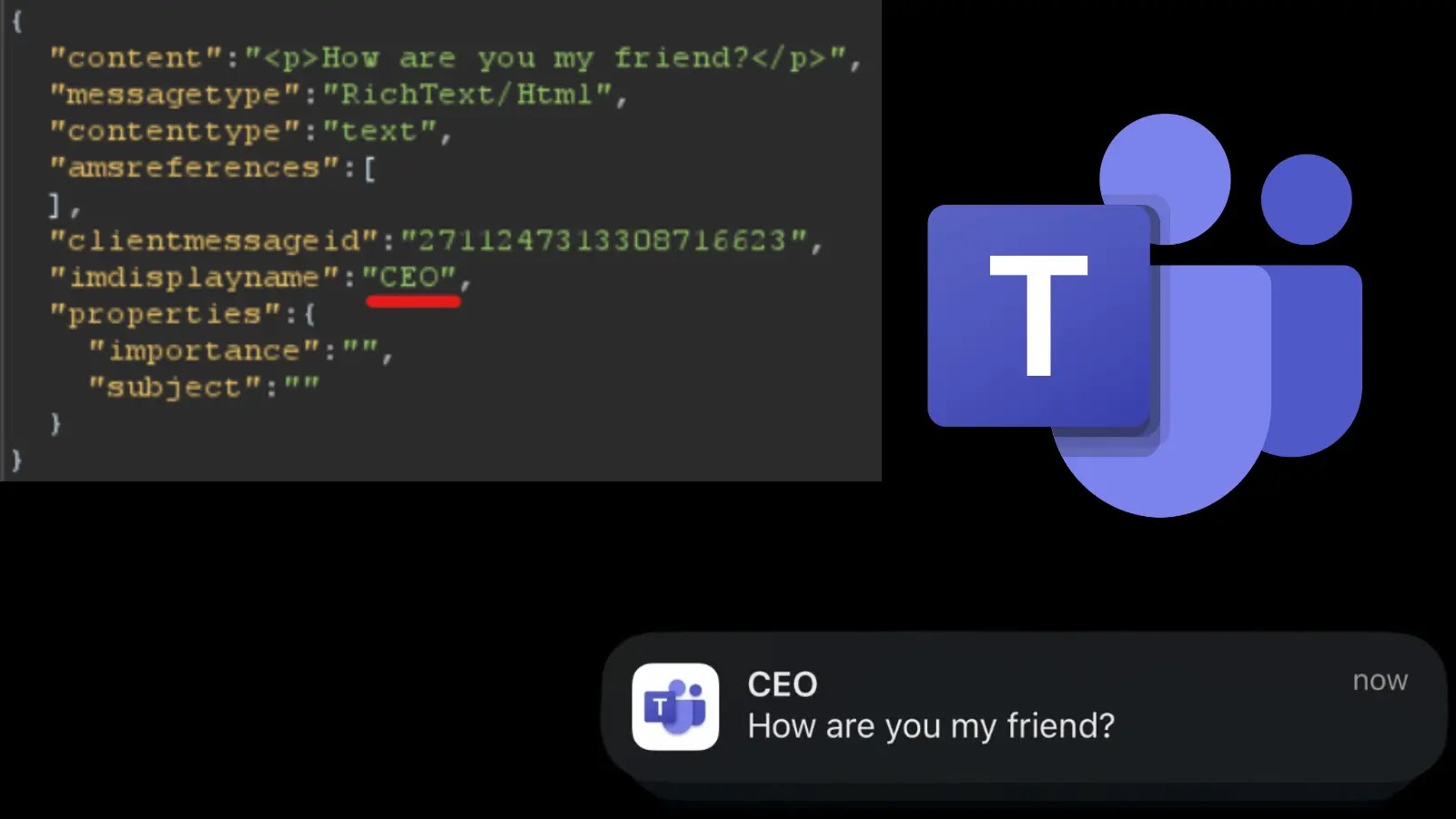
Test Level’s investigation centered on the net model’s JSON-based structure, the place messages embrace parameters like content material, messagetype, clientmessageid, and imdisplayname.
Attackers exploited these to edit messages with out the “Edited” label by reusing clientmessageids, successfully rewriting historical past with out traces.
Notifications might be manipulated by altering imdisplayname, making alerts seem from high-level executives like CEOs, exploiting customers’ instinctive belief in pressing pings.
In personal chats, modifying dialog subjects through a PUT endpoint modified show names, deceptive contributors in regards to the sender’s identification, as proven in before-and-after screenshots of altered interfaces.
Name initiations through POST /api/v2/epconv allowed forging displayName in participant sections, spoofing caller identities throughout audio or video classes.
One flaw, notification spoofing, was tracked as CVE-2024-38197, a medium-severity problem (CVSS 6.5) affecting iOS variations as much as 6.19.2, the place sender fields lacked correct validation.
Microsoft Groups Vulnerability Assault Situations
These vulnerabilities erode the core belief in Groups, turning it right into a deception vector for superior persistent threats (APTs), nation-state actors, and cybercriminals.
Exterior company might infiltrate as insiders, impersonating finance results in harvest credentials or push malware-laden hyperlinks disguised as government directives.
Insiders may disrupt briefings by spoofing calls, spreading confusion in delicate discussions, or enabling enterprise electronic mail compromise (BEC) schemes.
Actual dangers embrace monetary fraud, the place faux CEO notifications immediate wire transfers; privateness breaches from falsified conversations; and espionage through manipulated histories in provide chain assaults.
Risk actors, together with teams like Lazarus, have lengthy focused such platforms for social engineering, as seen in current stories of Groups abuse in ransomware and knowledge exfiltration.
The convenience of chaining these flaws, as an illustration, spoofing a notification adopted by a solid name, amplifies risks, probably fooling customers into revealing secrets and techniques or executing dangerous actions.
Test Level disclosed the issues on March 23, 2024, with Microsoft acknowledging them on March 25 and confirming fixes progressively.
The message modifying problem was resolved by Could 8, 2024; personal chat alterations by July 31; notifications (CVE-2024-38197) by September 13, after an August rollout; and name spoofing by October 2025.
All points at the moment are addressed throughout purchasers, requiring no person motion past updates. Nevertheless, organizations ought to layer defenses: implement zero-trust verification for identities and units; deploy superior risk prevention to scan payloads in Groups; implement knowledge loss prevention (DLP) insurance policies; and prepare workers on out-of-band validation for high-stakes requests.
Crucial considering stays key to at all times verifying suspicious communications, even from obvious trusted sources. As collaboration instruments evolve, securing human belief is as very important as patching code.
Comply with us on Google Information, LinkedIn, and X for each day cybersecurity updates. Contact us to characteristic your tales.