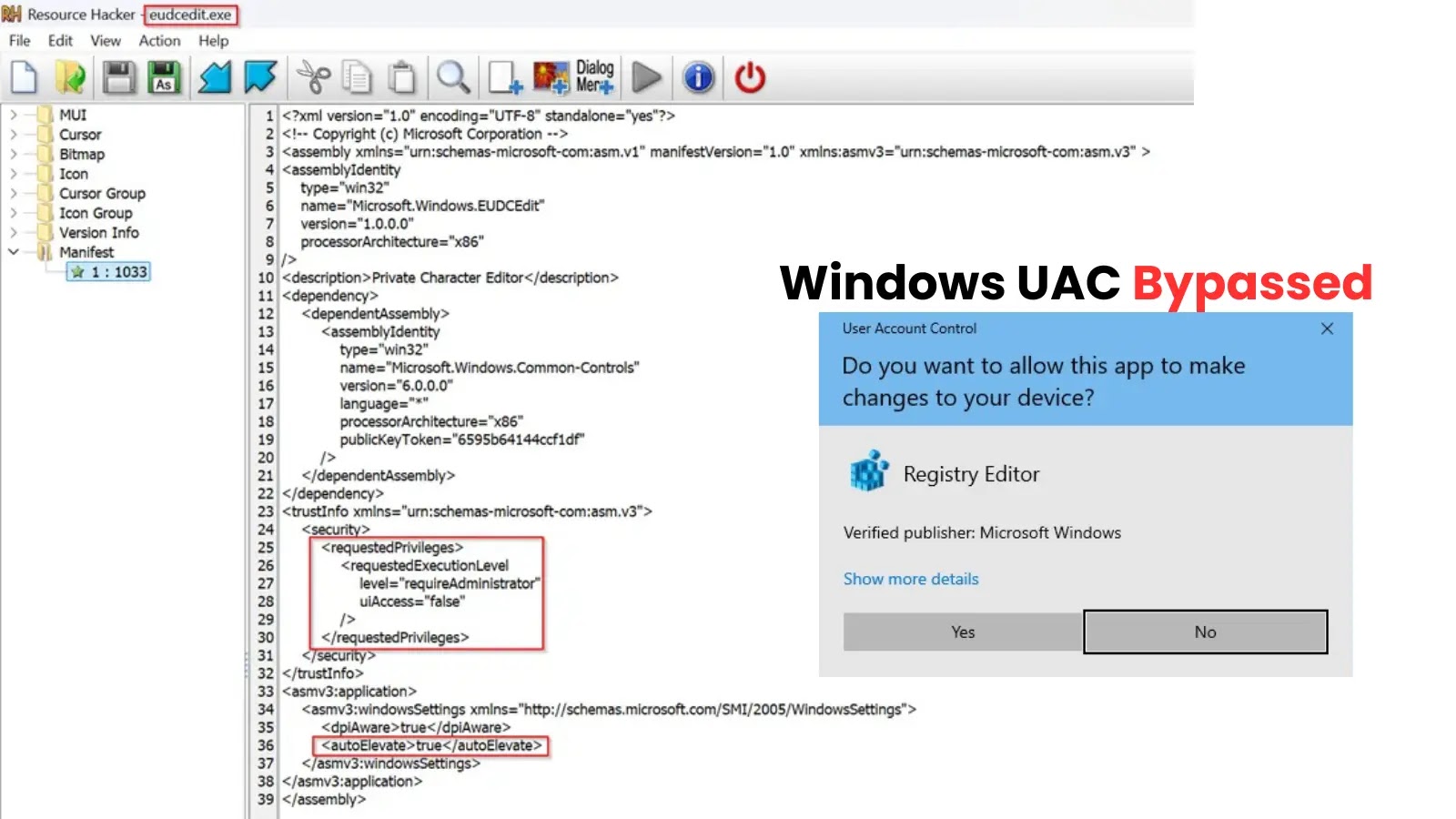
Microsoft’s newly unveiled “Related Brokers” characteristic in Copilot Studio, introduced at Construct 2025, is creating a major safety vulnerability.
Attackers are already exploiting to realize unauthorized backdoor entry to crucial enterprise programs.
Related Brokers permits AI-to-AI integration, permitting brokers to share performance and reuse logic throughout environments.
Whereas designed for effectivity, much like wrapping repeated code into callable capabilities, the characteristic introduces harmful assault vectors when misconfigured or intentionally weaponized.
Overview of the Related Brokers Safety Danger
By default, Related Brokers is enabled on all new brokers in Copilot Studio.
Public Confronted Agent
When activated, the characteristic exposes an agent’s information, instruments, and matters to ALL different brokers throughout the similar setting.
The issue: there’s no built-in visibility displaying which brokers have related to yours, making a blind spot for safety monitoring.
In response to Zenity Labs, attackers are exploiting this hole by creating malicious brokers that hook up with legit, privileged brokers, notably these with email-sending capabilities or entry to delicate enterprise knowledge.
e-mail‑sending instrument
In proof-of-concept demonstrations, risk actors efficiently compromised help brokers configured to ship emails from official firm domains.
Enabling large-scale phishing and impersonation assaults. Think about a help agent geared up with email-sending instruments.
An insider risk or compromised account creates a backdoor agent that connects to this legit agent, then triggers e-mail performance with out leaving traces in exercise logs.
The Related Brokers invocation generates zero messages within the focused agent’s exercise tab, evading normal audit mechanisms.
The attacker can now ship emails impersonating your organization to 1000’s of recipients and destroy model popularity by means of misinformation.
1Trigger domain-blocking by means of spam, all whereas showing to originate out of your infrastructure. Zenity Labs urges organizations to right away audit brokers presently in manufacturing.
Disable Related Brokers on all brokers containing unauthenticated instruments or delicate information sources earlier than publishing.
easy POC
Implement instrument authentication, making certain delicate actions require specific person credentials, not proprietor permissions.
For business-critical brokers, disable the Related Brokers characteristic fully.
Assessment all information sources and publishing channels, verifying that present and future setting customers legitimately require entry to every uncovered functionality.
Zenity Labs additionally recommends that Microsoft default this characteristic to disabled fairly than enabled, shifting accountability to builders to choose in fairly than requiring specific, reactive safety hardening post-publication.
Till complete fixes emerge, treating any agent with Related Brokers enabled as publicly accessible is crucial for protection.
Comply with us on Google Information, LinkedIn, and X for every day cybersecurity updates. Contact us to characteristic your tales.