A new malicious campaign has surfaced, targeting unsuspecting users through a counterfeit version of the popular 7-Zip file archiving tool. This deceptive operation turns home computers into residential proxy nodes, exploiting users who download from an imposter domain.
Imposter Domains and Malware Installation
The attack hinges on a fraudulent site, 7zip[.]com, which closely resembles the official 7-zip.org, misleading users into installing a compromised installer. This installer appears genuine but harbors dangerous malware components, as reported by a Reddit user who experienced issues after following a PC-building tutorial on YouTube.
After downloading from the fake site, the user faced persistent errors and eventually discovered the infection when Microsoft Defender detected a generic trojan. The malware was present on both a laptop and a newly assembled desktop.
Malware Components and Persistence
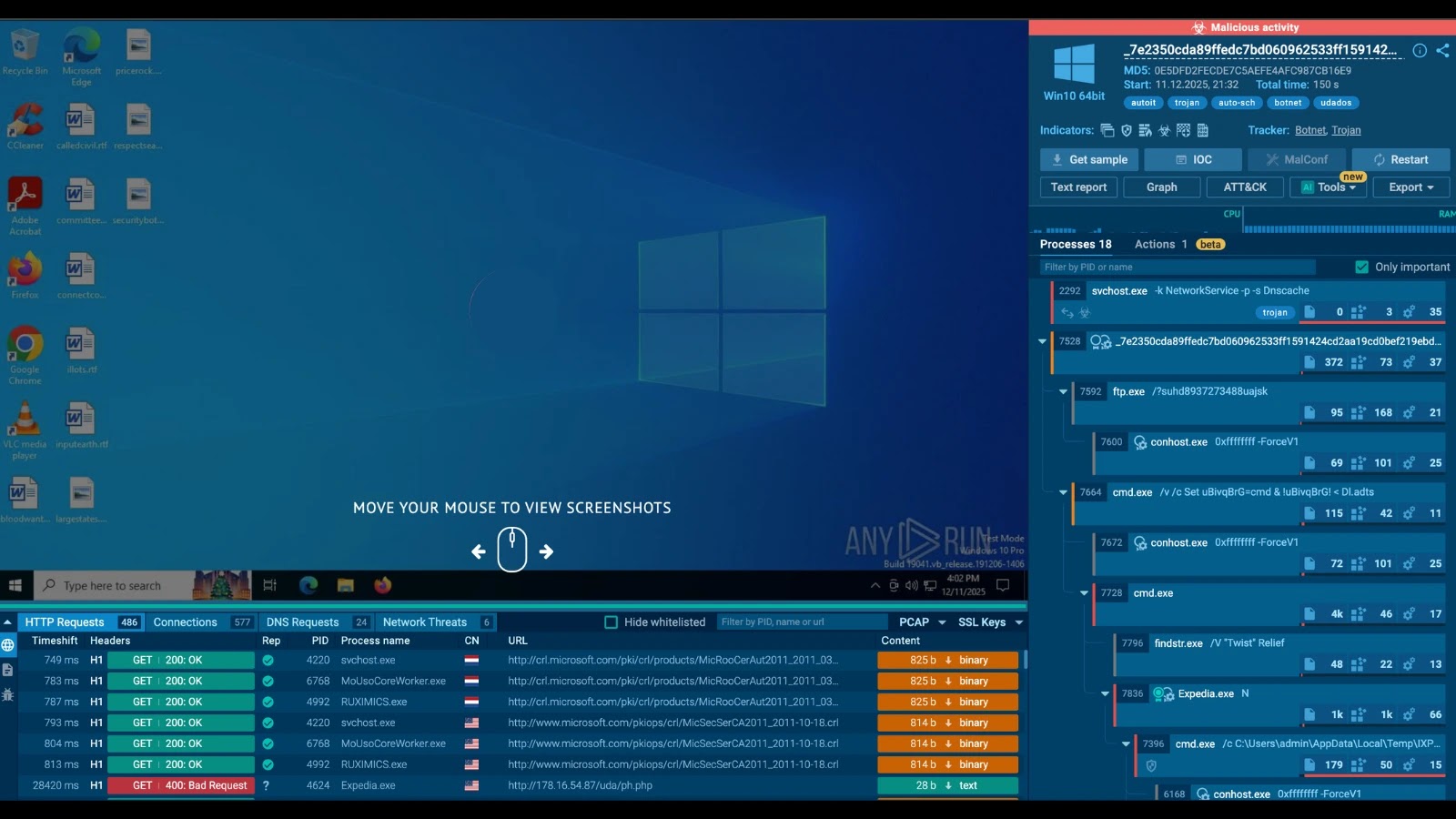
Security experts from Malwarebytes identified that the malicious installer delivers a working version of 7-Zip alongside three hidden malware components: Uphero.exe, hero.exe, and hero.dll. These files are placed in the C:WindowsSysWOW64hero directory, a location not commonly checked by users.
The installer bore a digital signature from Jozeal Network Technology Co., Limited, initially adding false legitimacy. This signature has since been revoked. The malware gains persistence by registering as Windows services with SYSTEM-level startup privileges, manipulating firewall settings, and transmitting detailed system data to external servers.
Proxy Network and Detection Challenges
The malware’s core purpose is to turn infected systems into nodes in a residential proxy network. Using “smshero” themed domains, the malware communicates with command-and-control servers via encrypted channels, making detection difficult.
Researchers found that the malware uses a lightweight XOR-encoded protocol to obscure messages and creates outbound proxy connections through non-standard ports. This setup is typical of residential proxy services used for activities like fraud and web scraping. The malware also uses DNS-over-HTTPS to evade traditional monitoring.
Victims of this malware should consider their systems compromised. Security solutions like Malwarebytes can detect and eliminate known variants, but a full operating system reinstall might be necessary for complete removal. Users are advised to verify software sources, be skeptical of unexpected code-signing identities, and monitor for unauthorized system changes.
Network administrators can enhance security by blocking known malicious domains and endpoints. Stay informed by following us on Google News, LinkedIn, and X for more updates.